OverTheWire Natas Level 24 Walkthrough
The Natas walkthrough series continues with level 24. This challenge is based around PHP data types and how they can affect web security.
What is Natas?
Natas is an online hacking game meant to help you learn and practice security concepts.
OverTheWire is a website with a number of “war games”, which are online hacking games that allow you to practice security concepts. If you are looking for a beginner introduction to web security (albeit an older tech stack), then Natas is a great place to start.
Natas is hosted on different subdomains following the pattern of http://natas<level#>.natas.labs.overthewire.org. As you progress through the levels, you’ll need to increment the level number in the URL in order to view the correct level.
Each level requires the levels below it to be solved, so you will need the level 24 flag found in level 23 to begin this walkthrough. As before, make sure you keep notes and write down the passwords as you find them!
Level 24 ➔ 25
Head over to http://natas24.natas.labs.overthewire.org/ (log in with username natas24 and password OsRmXFguozKpTZZ5X14zNO43379LZveg). We’ve got another password-themed challenge:
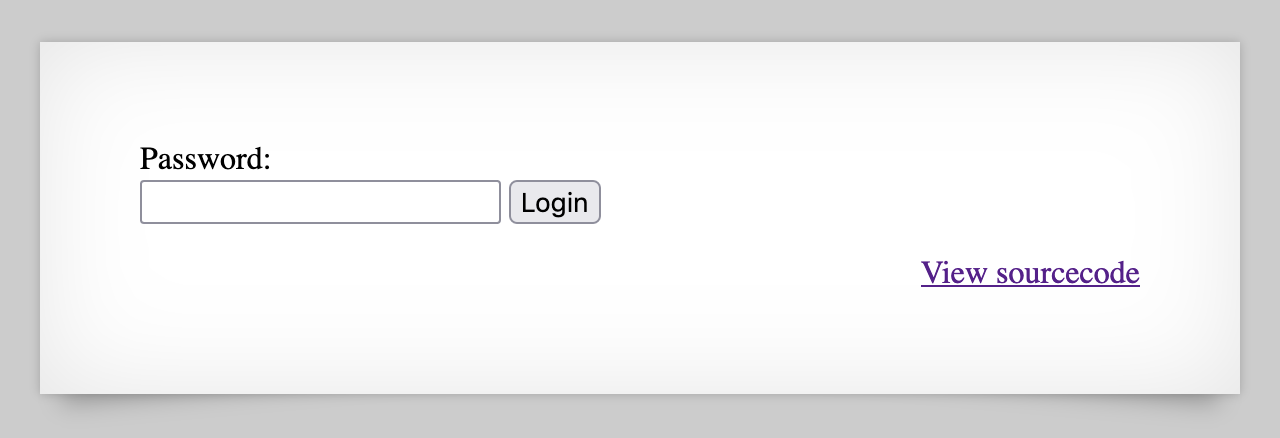
The source code provided shows that the password comparison is done using strcmp().
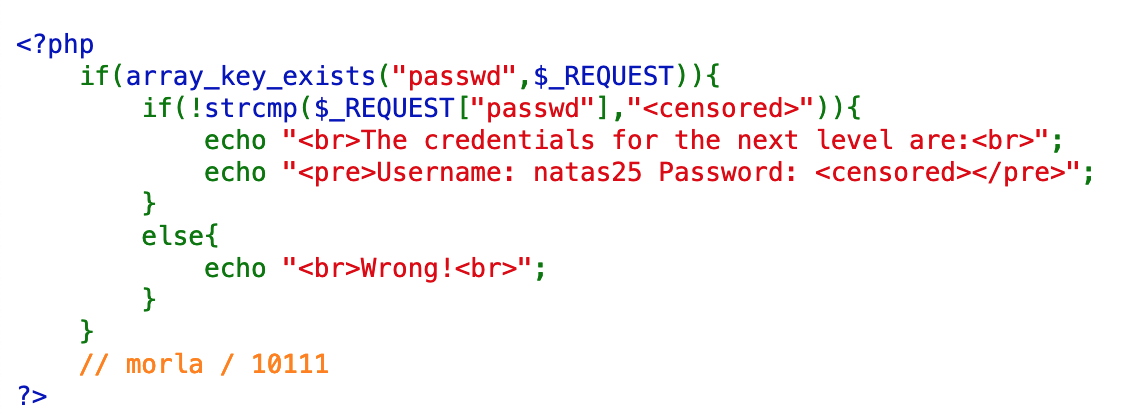
The strcmp() function will:
- Return < 0 if string1 is less than string2
- Return > 0 if string1 is greater than string2
- Return 0 if equal
For example, we can use a PHP sandbox or php -a in a terminal window to test this out:
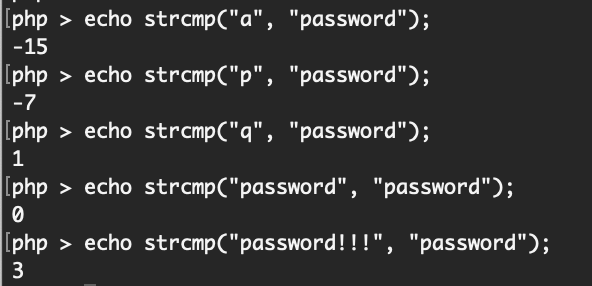
If we were able to get any feedback from the strcmp() function, it might be possible to brute force the password by using the negative or positive feedback from the strcmp() function. But that’s not the case for us.
A little bit of digging around for “bypassing strcmp” helped me find this CTF writeup from CSAW. In the CSAW challenge, players are able to bypass the check entirely by getting the $password value to equal NULL, which in PHP is equal to 0. The way they do this is by setting $password equal not to a string but to an array. And, the natas24 source code has no checks to make sure we don’t do this.
Natas Level 24 Solution
If we submit a password through the form, the URL is updated to reflect this.
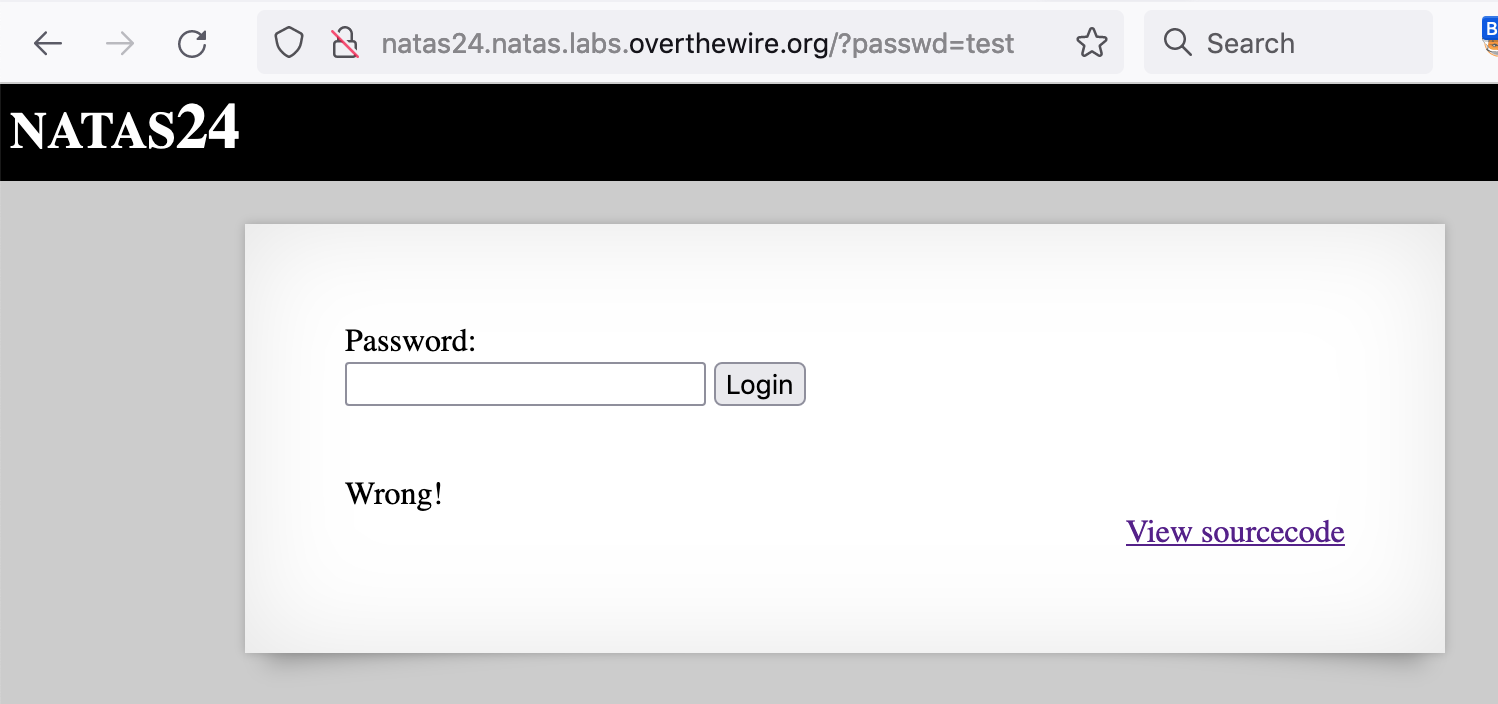
For example, submitting “test” results in a URL of
http://natas24.natas.labs.overthewire.org/?passwd=test
Where passwd is set equal to the string test.
If instead, we submit this request with passwd as an array (by adding in []), passwd will be equal to NULL, which is equal to 0. This will pass the strcmp() comparison:
http://natas24.natas.labs.overthewire.org/?passwd[]=test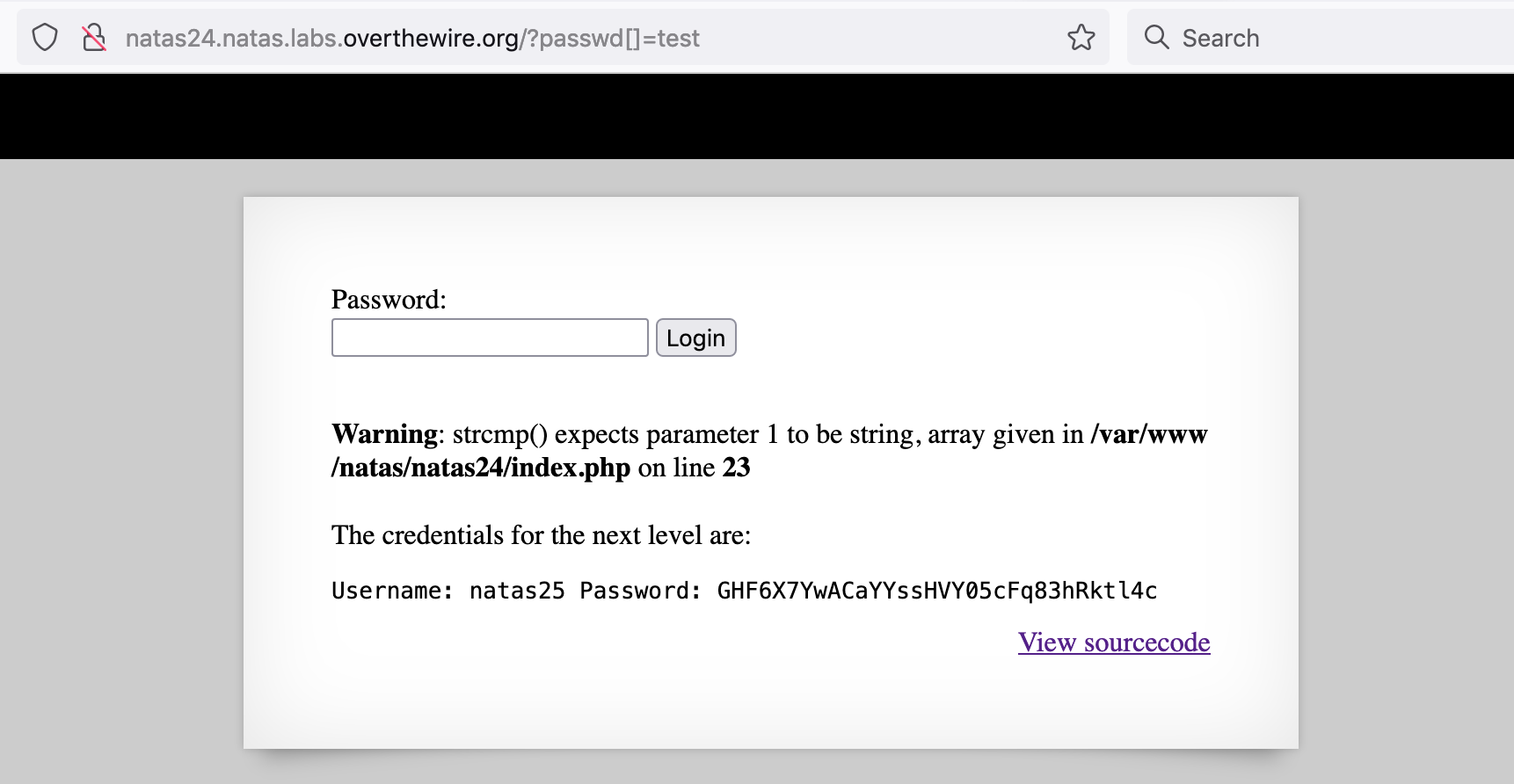
Takeaway: look for ways to submit data types that are not expected or checked by the source code.
Additionally, most PHP function bypasses are well-known and covered pretty well on various blogs, so try searching for function names after you’ve identified where the comparison happens. Devs can do the same search and use that info to avoid making those mistakes.