PortSwigger's "2FA simple bypass" Walkthrough
This is a walkthrough of PortSwigger’s “2FA Simple Bypass” lab. You don’t necessarily need Burp Suite set up for this, although it does help.
You will need a Portswigger Academy account, however. Log in to your Academy account and then view the lab at https://portswigger.net/web-security/authentication/multi-factor/lab-2fa-simple-bypass. This is accessible from the “all labs” view.
Challenge Information
Click the “Access the Lab” button and you will be taken to a temporary website that is created for your account. This will be in format https://<random string here>.web-security-academy.net/.
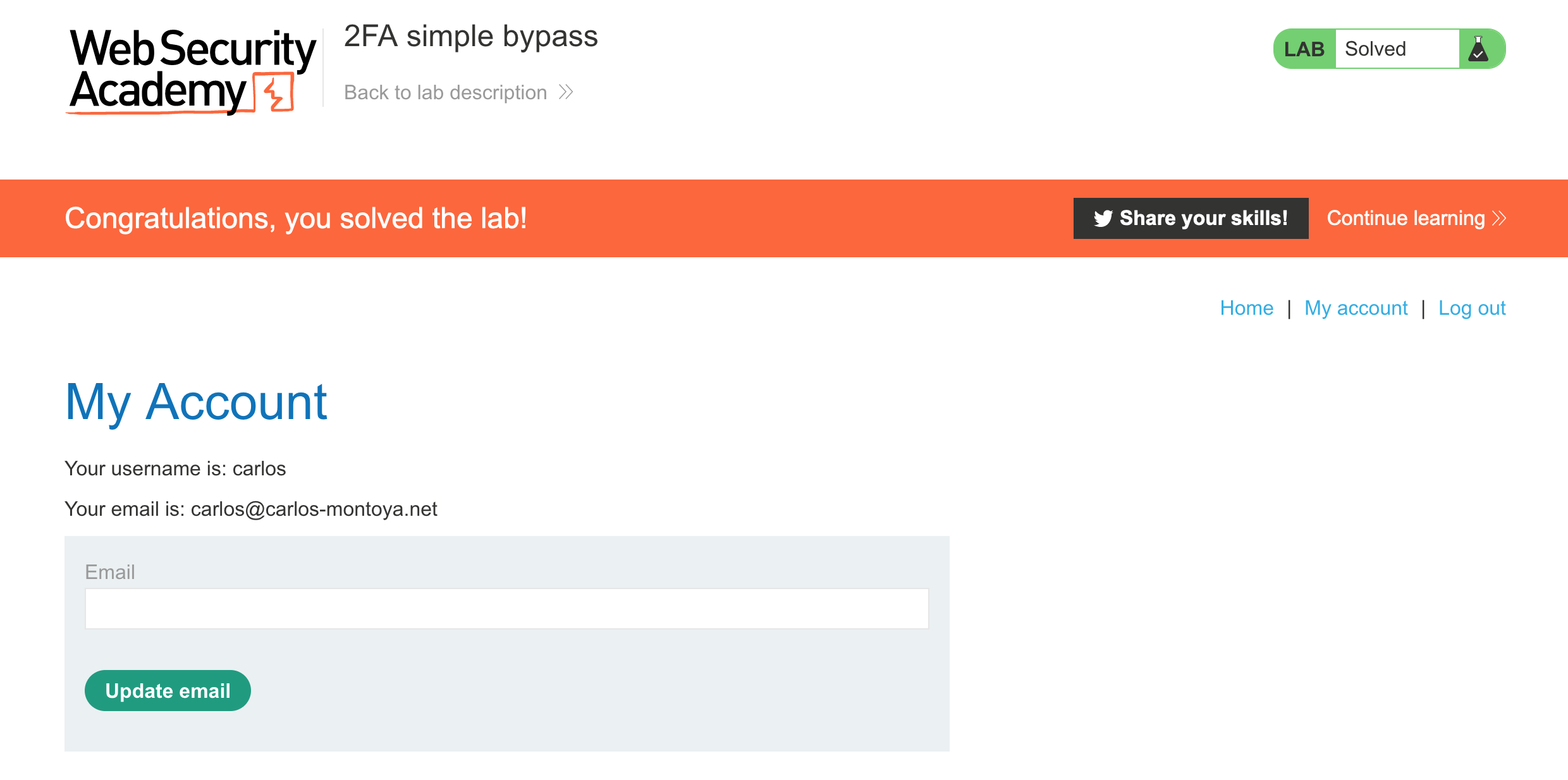
This lab gives us two sets of credentials, one for our own account (plus email inbox) and then one for Carlos. Our goal is to access Carlos’ account, although we don’t have email access for 2FA.
The site is a blog:
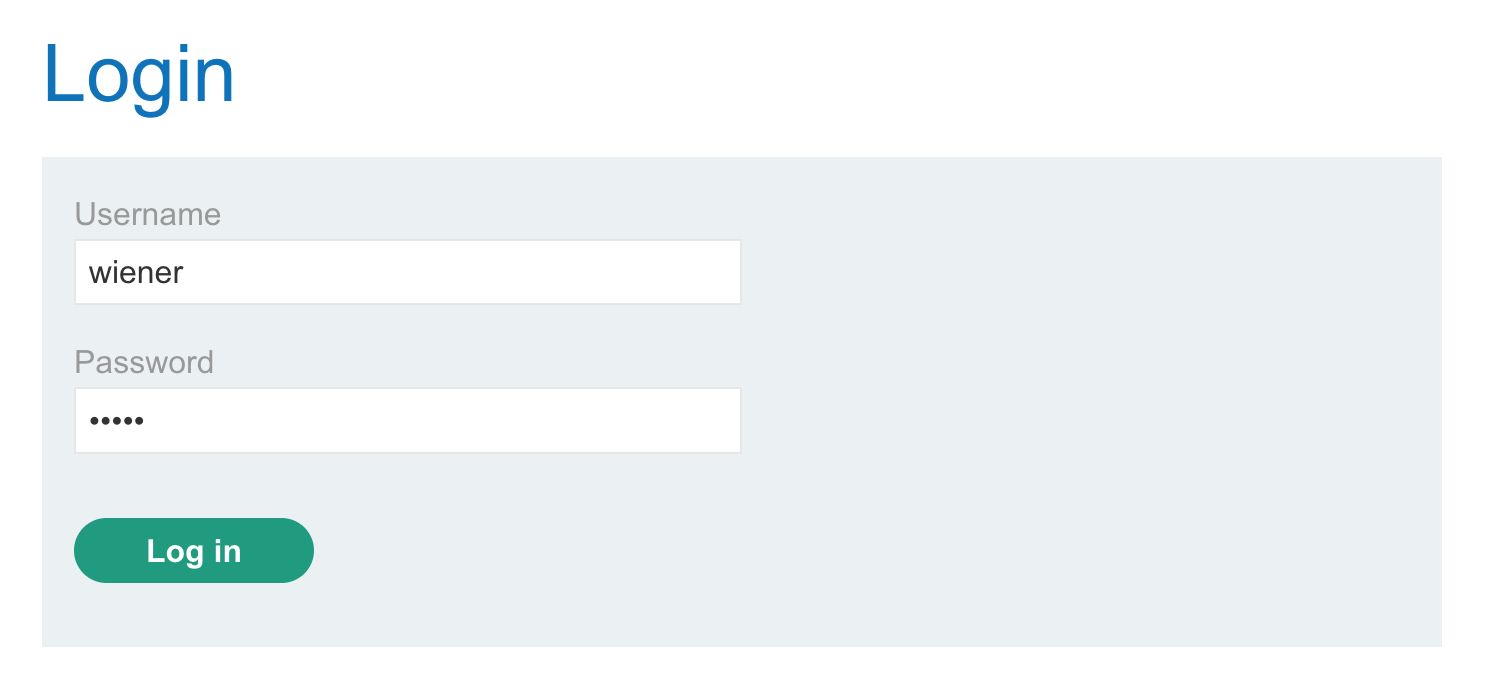
Click “My account” to login, then supply wiener:peter as the credentials:
You’ll be prompted for a 2FA code:
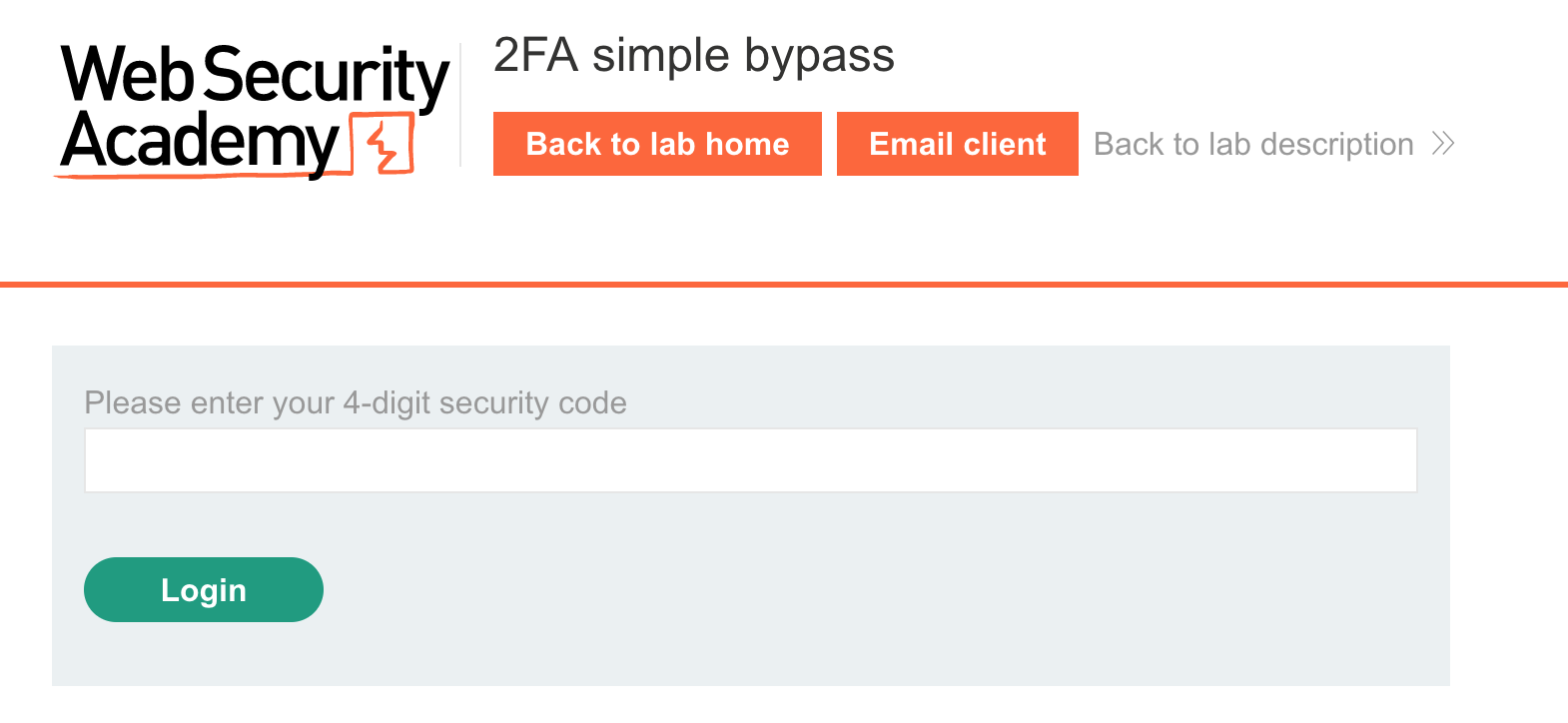
This can be found by clicking Email Client in the banner and then reading the latest email:
After supplying the 2FA code, you’re logged in.
You can repeat this process for Carlos, but you’ll get stuck at the 2FA section. I tried timing the two logins (carlos and wiener) like a race condition, but it turns out the answer is much simpler.
If you have had Burp Suite open during this time, or have simply been watching the URLs, the pattern is as follows:

- The
/loginpage is loaded, then aPOSTrequest is made to/loginwith the username and password. - The server responds to this with a 302 redirect to
/login2, where you are prompted for a 2FA code. - You check your
/email, then aPOSTrequest is made to/login2with the 2FA code. - Finally, you’re forwarded to
/my-account.
We have the credentials carlos:montoya, so we can get through steps 1 and 2. Rather than making a POST request in step 3, why not just try… browsing directly to /my-account?
If we login with credentials carlos:montoya, then go directly to:
https://<random-string>.web-security-academy.net/my-accountWe’re logged in as Carlos! No 2FA code needed.