PortSwigger's "Information disclosure in error messages" Walkthrough
This is a quick walkthrough of the first of five information disclosure labs (four of which are Apprentice-level).
Before we get started, you’ll need a Portswigger Academy account. Log in and then view the lab at https://portswigger.net/web-security/information-disclosure/exploiting/lab-infoleak-in-error-messages. This is accessible from the “all labs” view.
Challenge Information
Click the “Access the Lab” button and you will be taken to a temporary website that is created for your account. This will be in format https://<random string here>.web-security-academy.net/.
The goal of this challenge is to get the version number of the vulnerable framework being used. Our goal will be to trigger an error with some kind of unexpected input.
Here’s what the website looks like:
Lab Solution
If we open up one of the product pages, the URL pattern is as follows:
https://<random-string>.web-security-academy.net/product?productId=1Previous SQLi levels have returned an error when a non-number value is provided to productId, so let’s try that out by swapping out the number for a ':
https://<random-string>.web-security-academy.net/product?productId='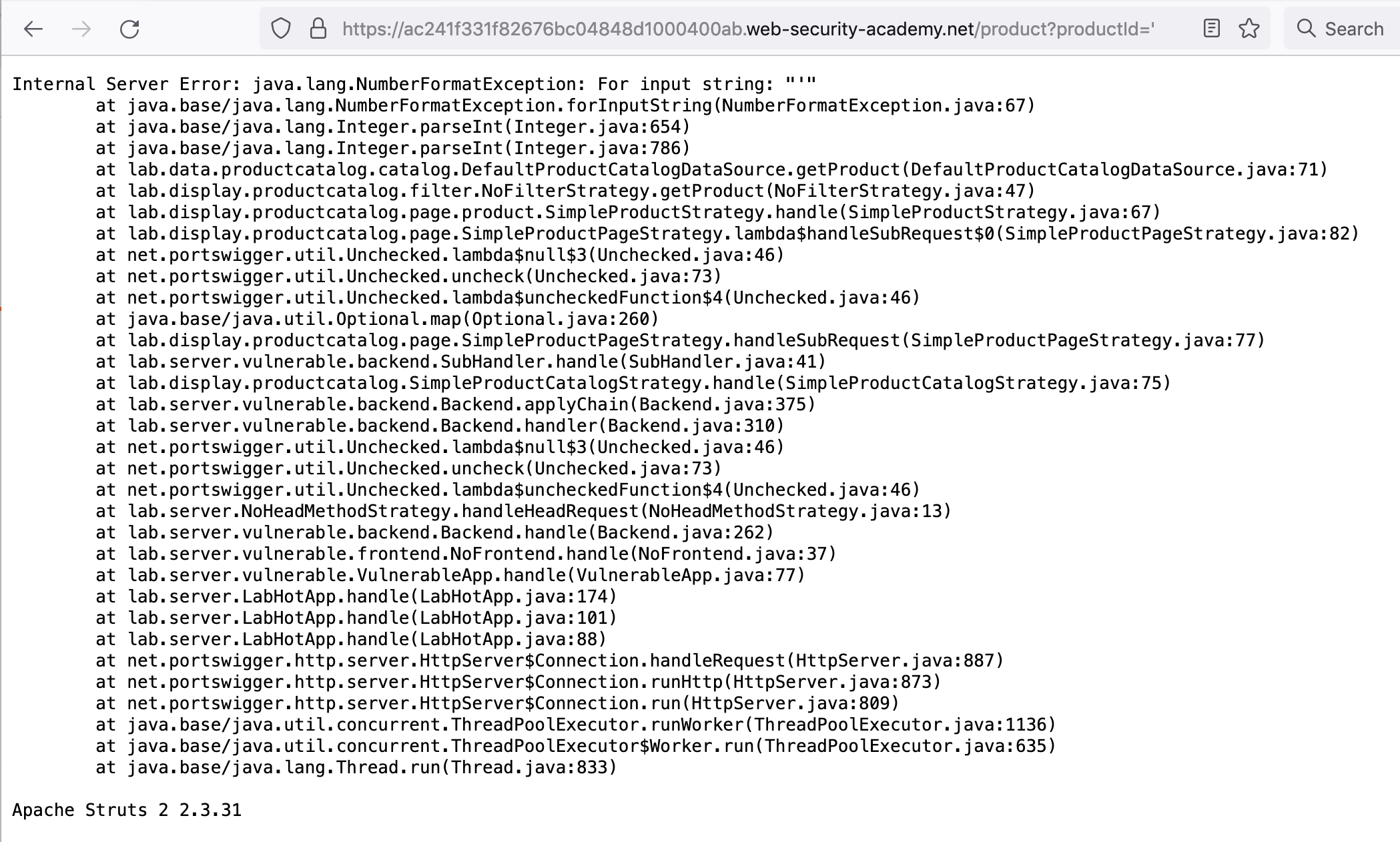
We get a stack trace, and at the bottom, it says:
Apache Struts 2 2.3.31Go back to the website home page, then click the “Submit Solution” button and input Apache Struts 2 2.3.31.
And that’s all!