PortSwigger's "Reflected XSS into HTML context with nothing encoded" Walkthrough
This is the first of Portswigger’s XSS Labs. Before we get started, you’ll need a Portswigger Academy account. You can do this level without Burp Suite, but here’s a guide on how to get it set up for future levels.
After logging in, head over to the lab, located at https://portswigger.net/web-security/cross-site-scripting/reflected/lab-html-context-nothing-encoded. You can find this through the Academy learning path list, or linked within the Reflected XSS blog post.
Challenge Information
Click the “Access the Lab” button and you will be taken to a temporary website that is created for your account. This will be in format https://<random string here>.web-security-academy.net/.
This is a reflected XSS attack that does not require any special tricks or encoding. This means that our malicious input (in the form of some script that executes) will be reflected onto the page, rather than stored in a database or somewhere else more permanent.
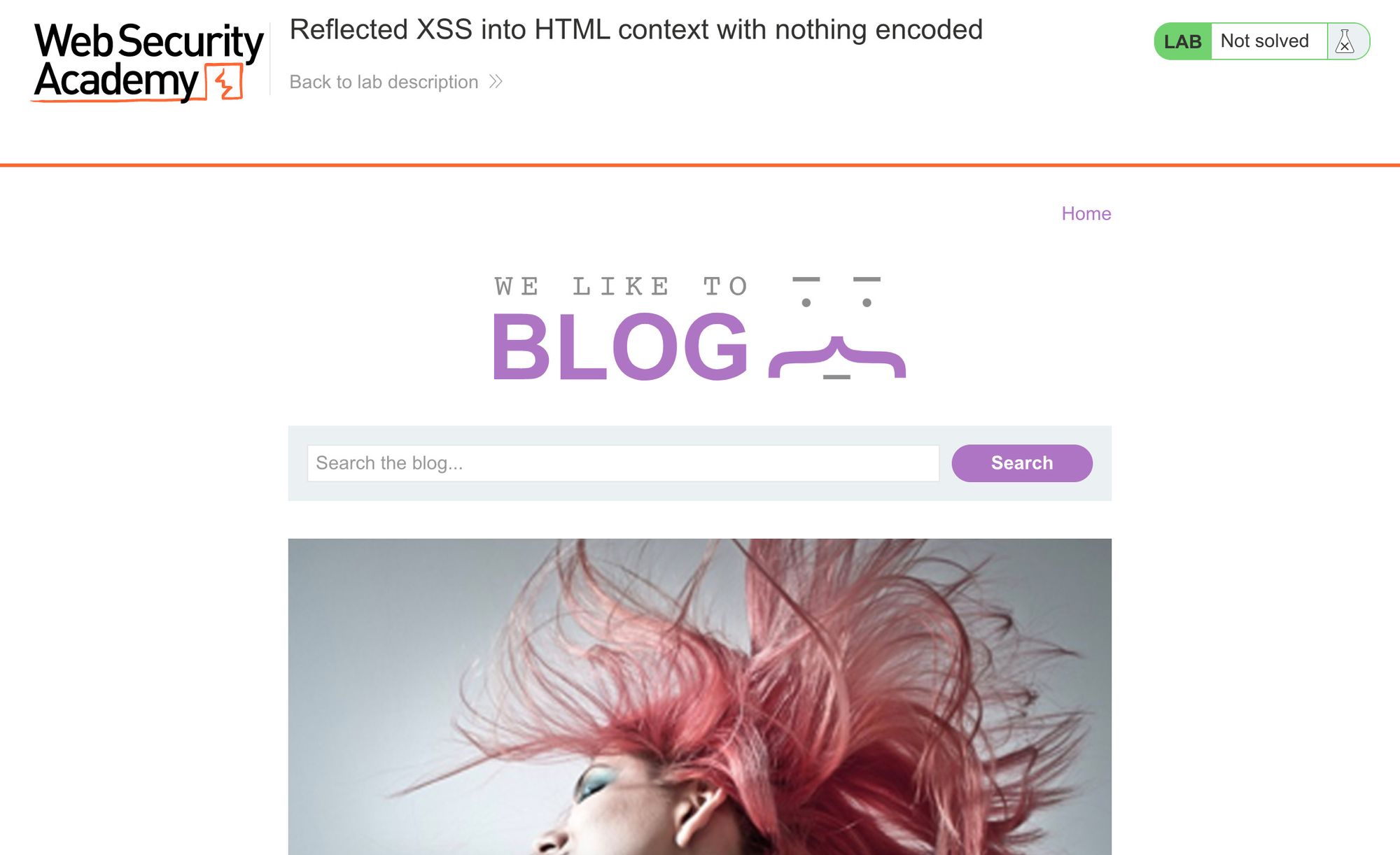
If we open up the website, we see that it’s a blog with a search bar at the top:
Finding the XSS vulnerability
Since we’re expecting a query parameter like /?key=value, we first need to find where a query like this happens.
We’re told in the challenge description that it is in the search parameter, although we could figure this out with experimentation since the blog doesn’t have much going on. If we type a value into the search bar and hit enter:
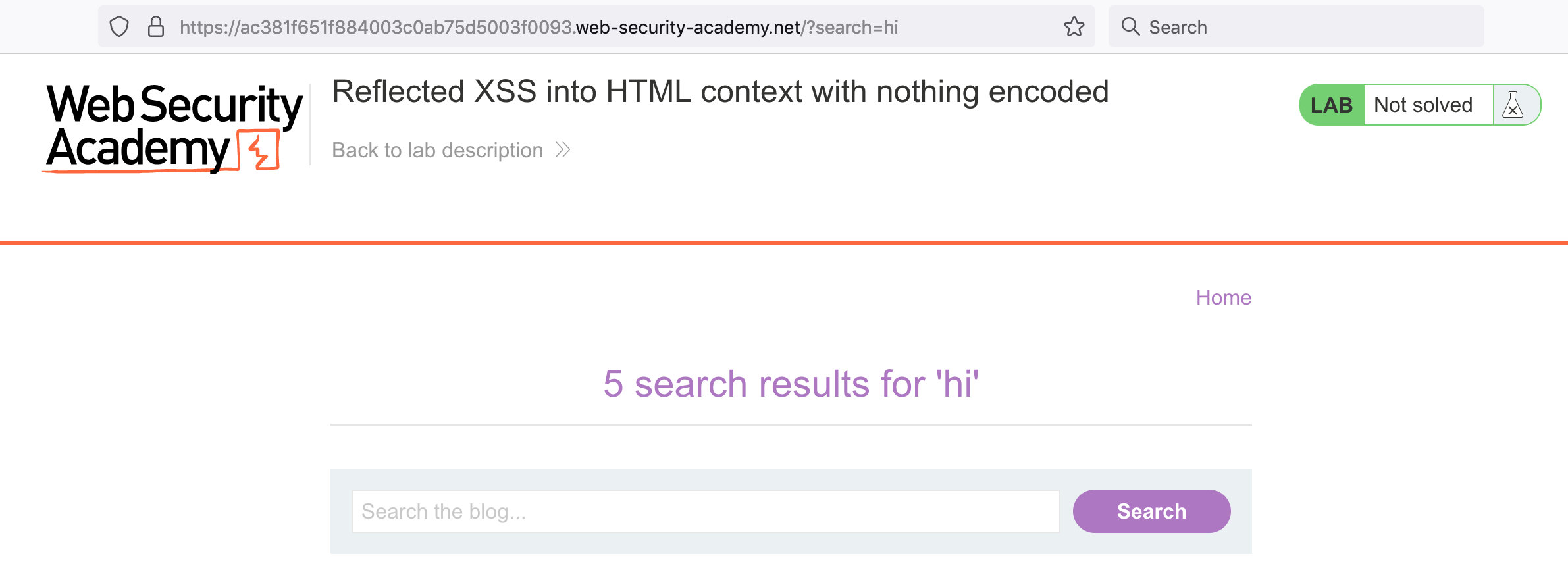
We get a URL parameter as expected, and we see that our input (“hi”) is shown, or reflected, on the page.
Lab Solution
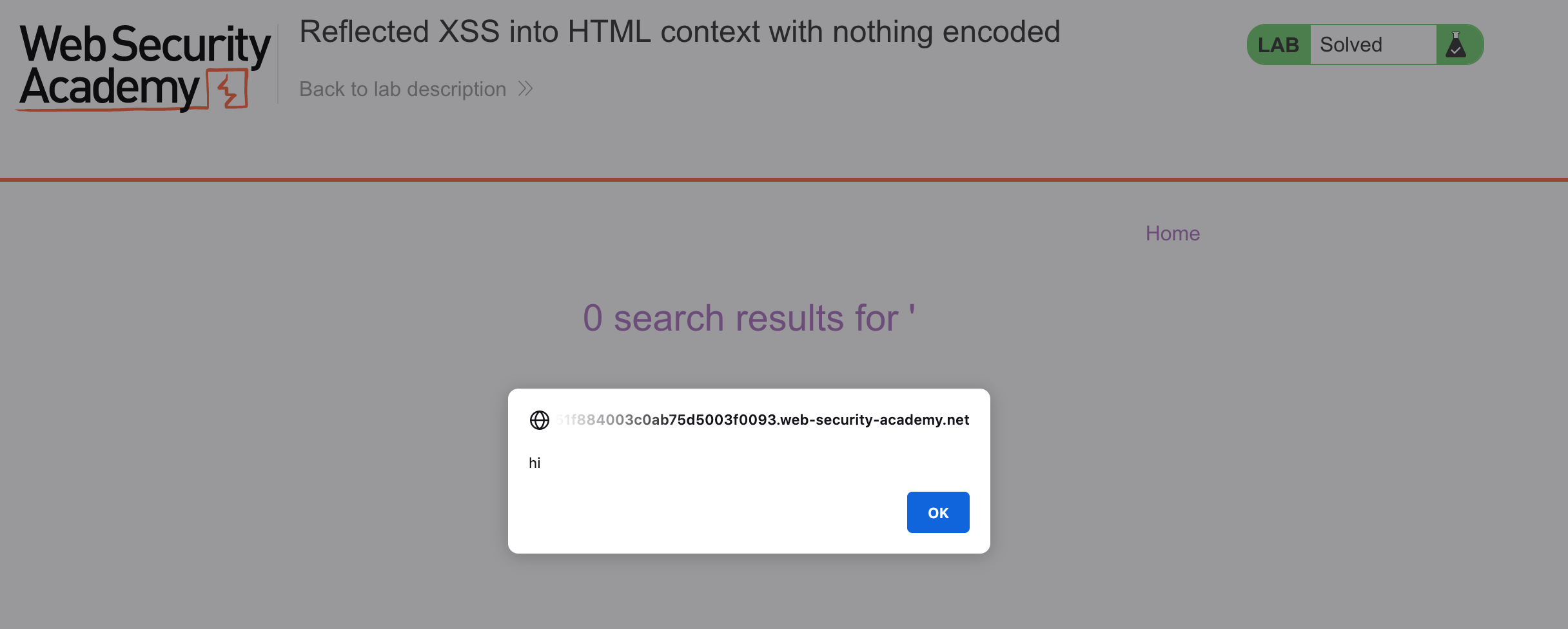
Since this lab does not require any special encoding, let’s try to pop an alert with payload <script>alert('hi')</alert>.
This goes in place of our previous parameter value for a URL like:
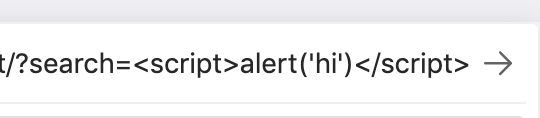
Hit enter, and you should get an alert value:
And that’s it!