PortSwigger's "User ID controlled by request parameter, with unpredictable user IDs" Walkthrough
This is a write-up of of PortSwigger Academy’s “user ID controlled by request parameter, with unpredictable user IDs” lab.
You’ll need a Portswigger Academy account before you get started. Log in and then view the lab at https://portswigger.net/web-security/access-control/lab-user-id-controlled-by-request-parameter-with-unpredictable-user-ids. This is accessible from the “all labs” view.
Challenge Information
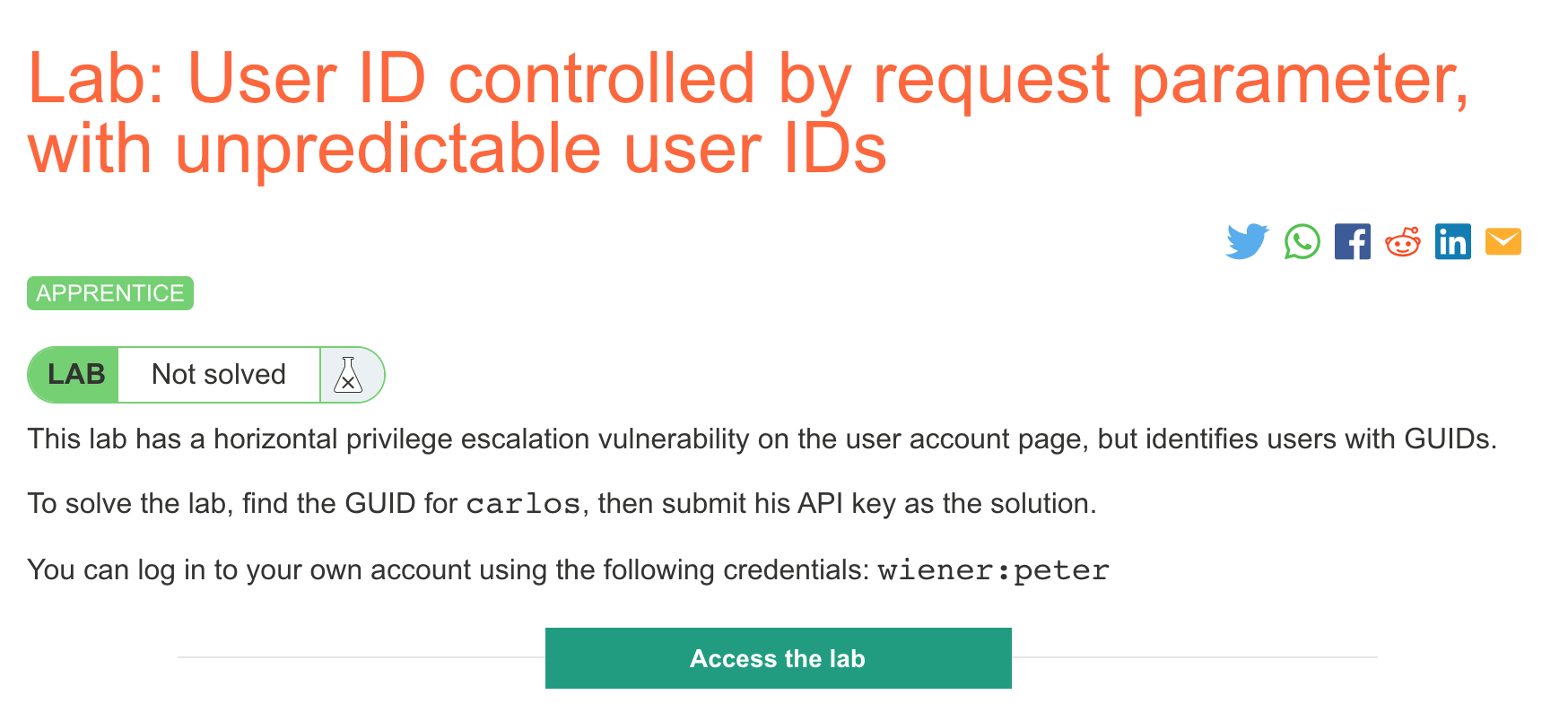
Click the “Access the Lab” button and you will be taken to a temporary website that is created for your account. This will be in format https://<random string here>.web-security-academy.net/.
Similar to previous labs, we’ll need to get Carlos’ API key in order to get credit for solving this lab. Unlike the last lab, users are identified with a GUID (long random string; a globally unique ID) instead of just their names, at least when talking to the API.
The website is a blog this time:
If we login with provided credentials wiener:peter:

We see our own API key on the account page:
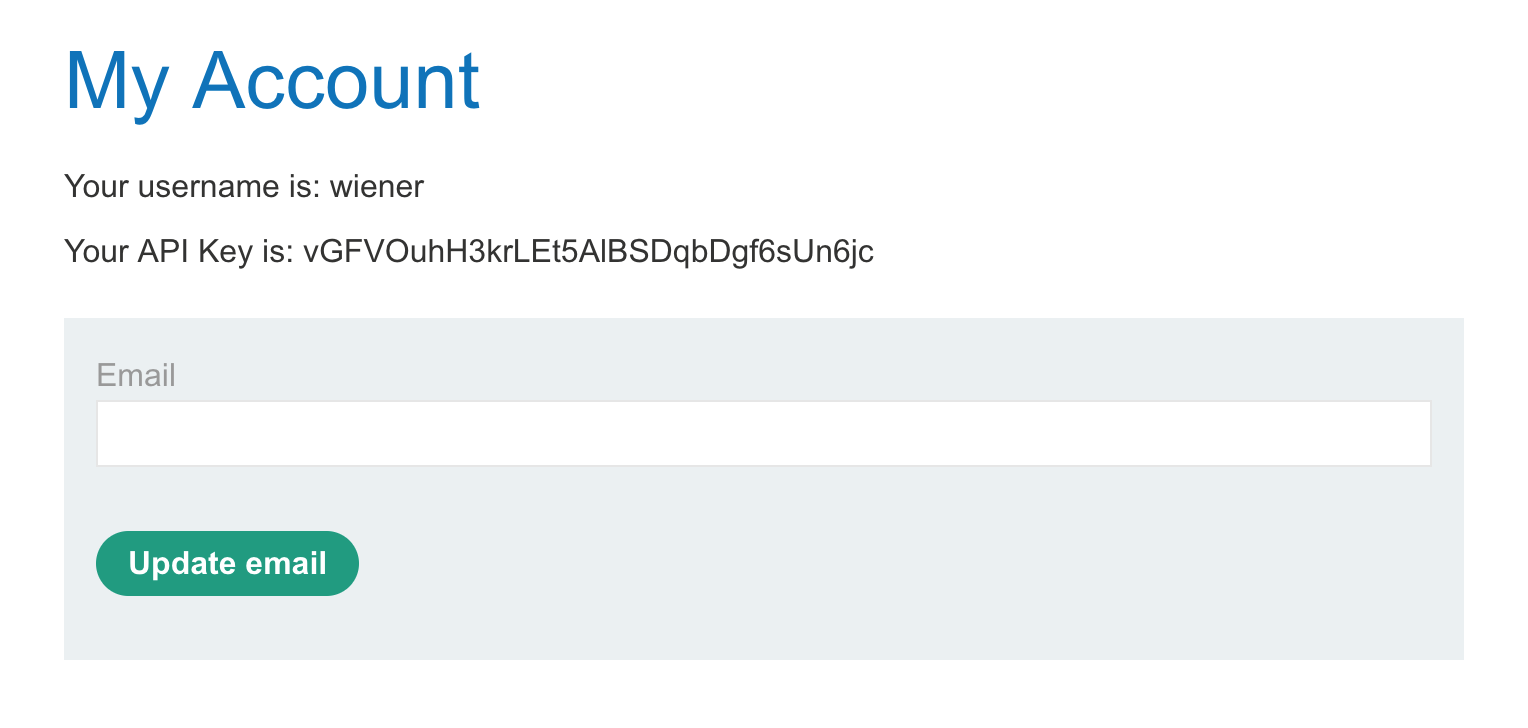
If we click “My account” again, we see that the URL ends in:
/my-account?id=42f81106-87cf-481d-903f-d3bac1dd37c4
(or another similar GUID, who knows, it might be randomly generated each time).
There’s nothing interesting in the email change request, and we already know from the lab description that the vulnerability is in the request parameter (the POST request doesn’t have one, only the “My account” GET request does).
So, we need to find the GUID for Carlos.
This is a blog site… maybe we can find some author pages?
Lab Solution
Click back to the home page, and open up a blog post. The user name includes a link to a user profile (in this case, for administrator) which includes a GUID!
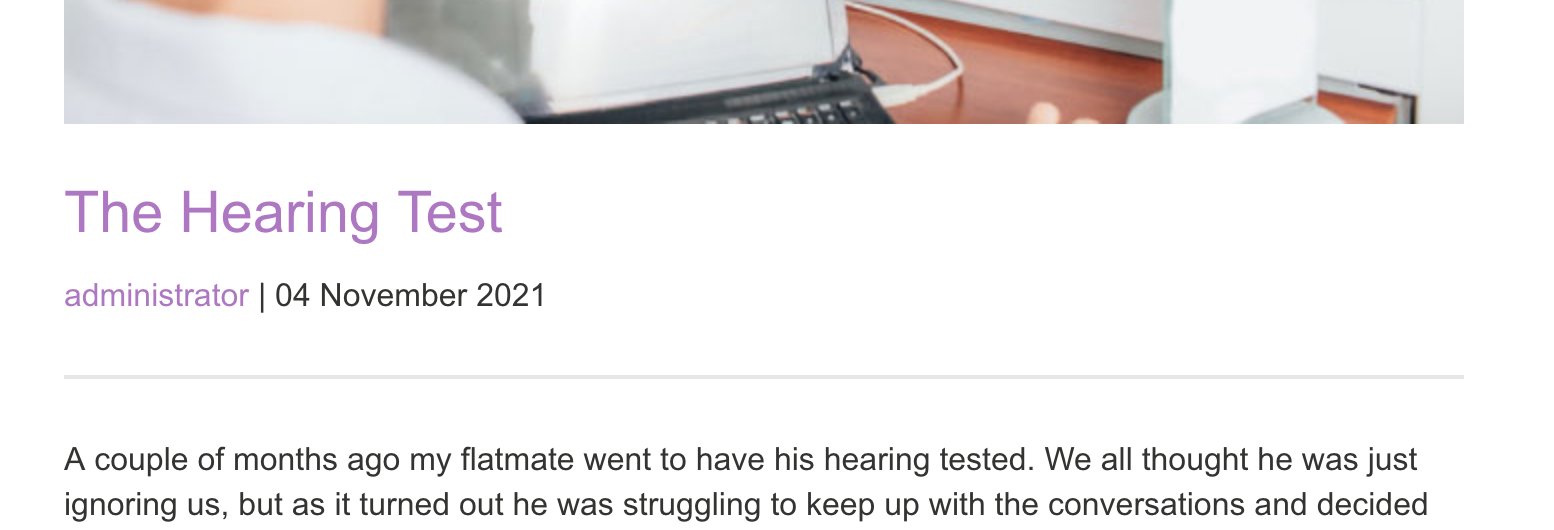
In this case, the administrator profile (and GUID) is /blogs?userId=16a70436-5c7e-47b9-8a0e-63724f874534.
Open up more blog posts until you find one written by Carlos:
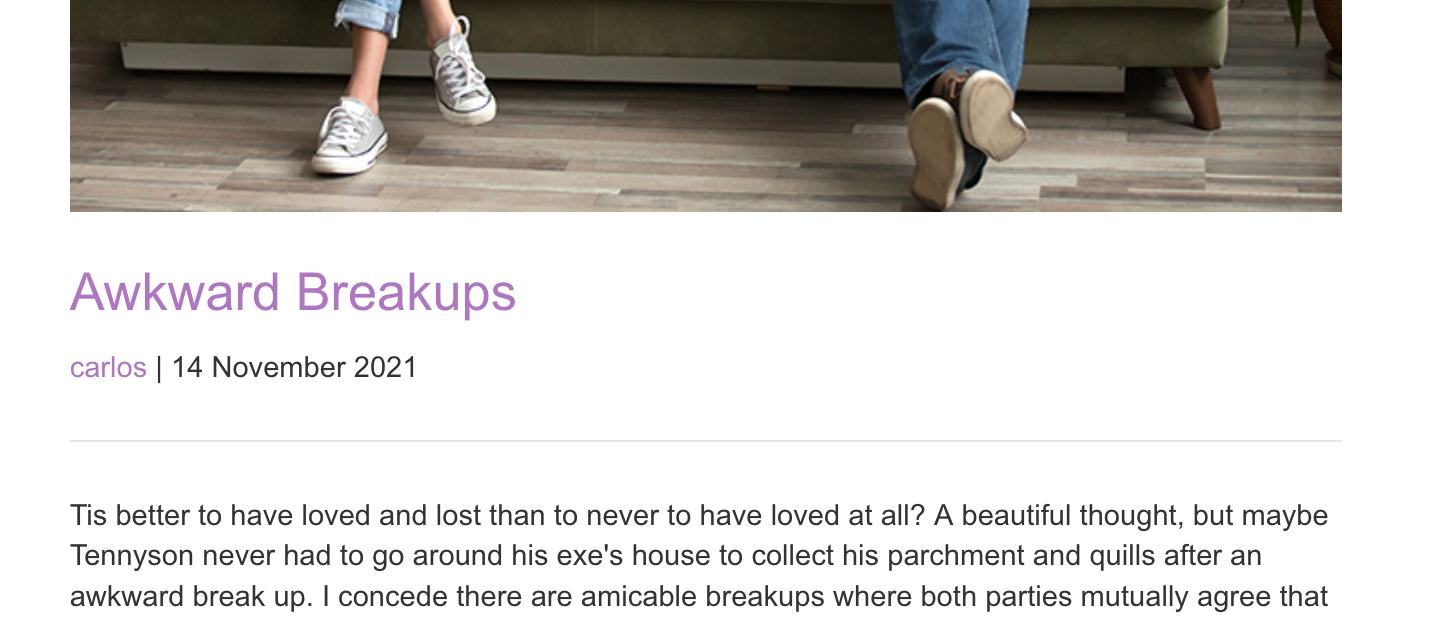
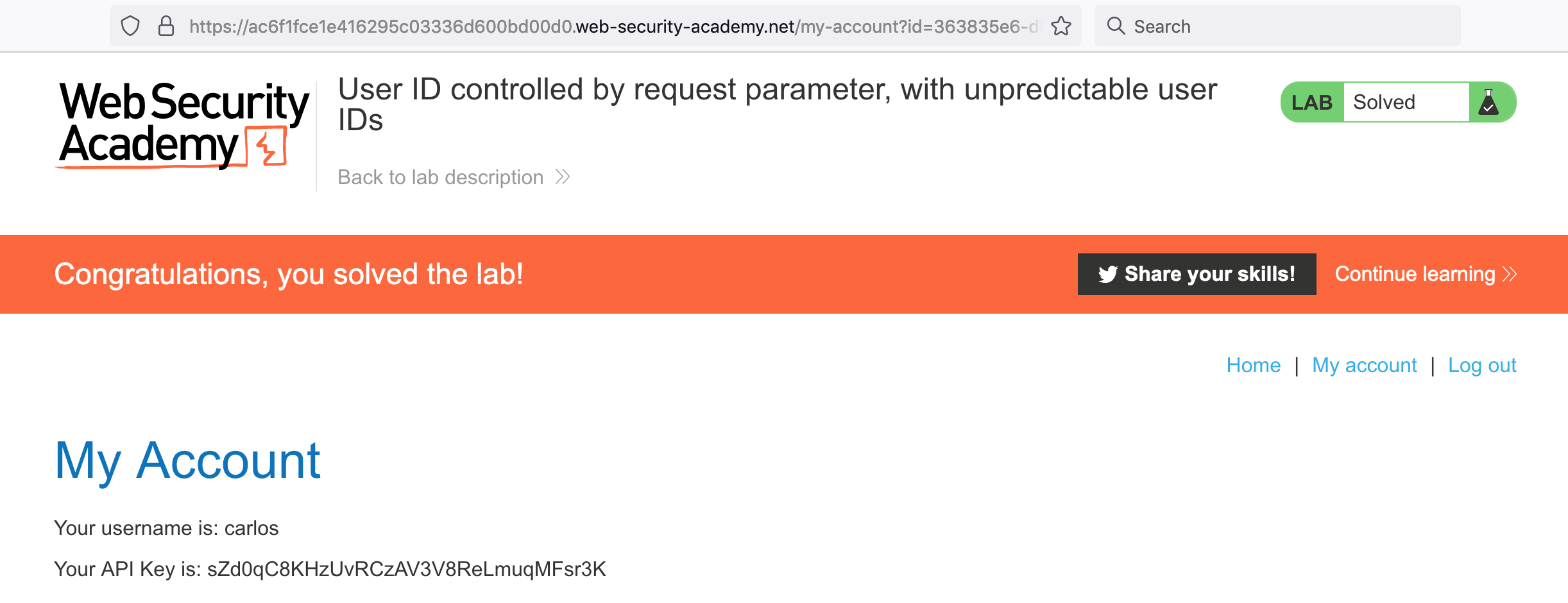
The user profile is /blogs?userId=363835e6-d5d1-4284-9ef2-8507067b06c1, so the GUID is 363835e6-d5d1-4284-9ef2-8507067b06c1.
Go back to the /my-account page and replace the previous GUID with the newly found GUID from Carlos.
In this case, it’s https://<random-string>.web-security-academy.net/my-account?id=363835e6-d5d1-4284-9ef2-8507067b06c1.
And there’s Carlos’ profile and API key!
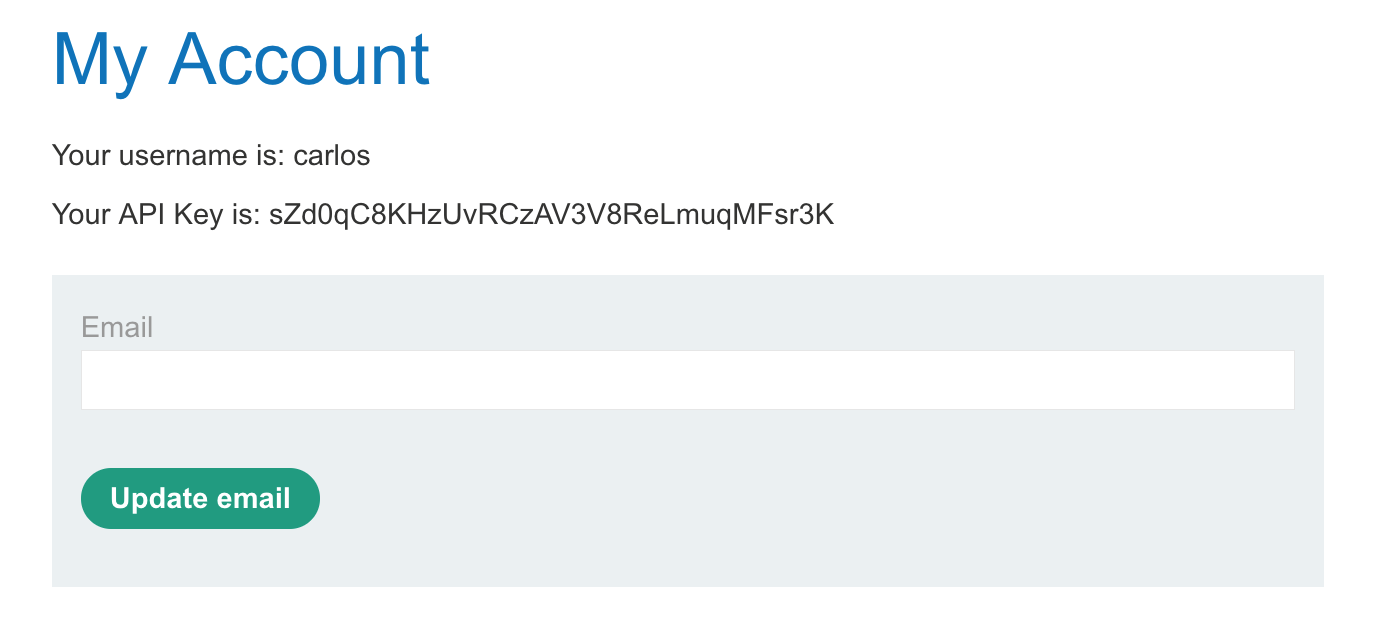
Submit the API key under the “Submit solution” option in the Academy header:
And the lab is now solved: