PortSwigger's "User ID controlled by request parameter with password disclosure" Walkthrough
This post is a writeup of PortSwigger’s “user ID controlled by request parameter with password disclosure” lab, which is part of the Access Control lab grouping.
You’ll need a Portswigger Academy account before you get started. Log in and then view the lab at https://portswigger.net/web-security/access-control/lab-user-id-controlled-by-request-parameter-with-password-disclosure. This is accessible from the “all labs” view or the access control blog post.
Challenge Information
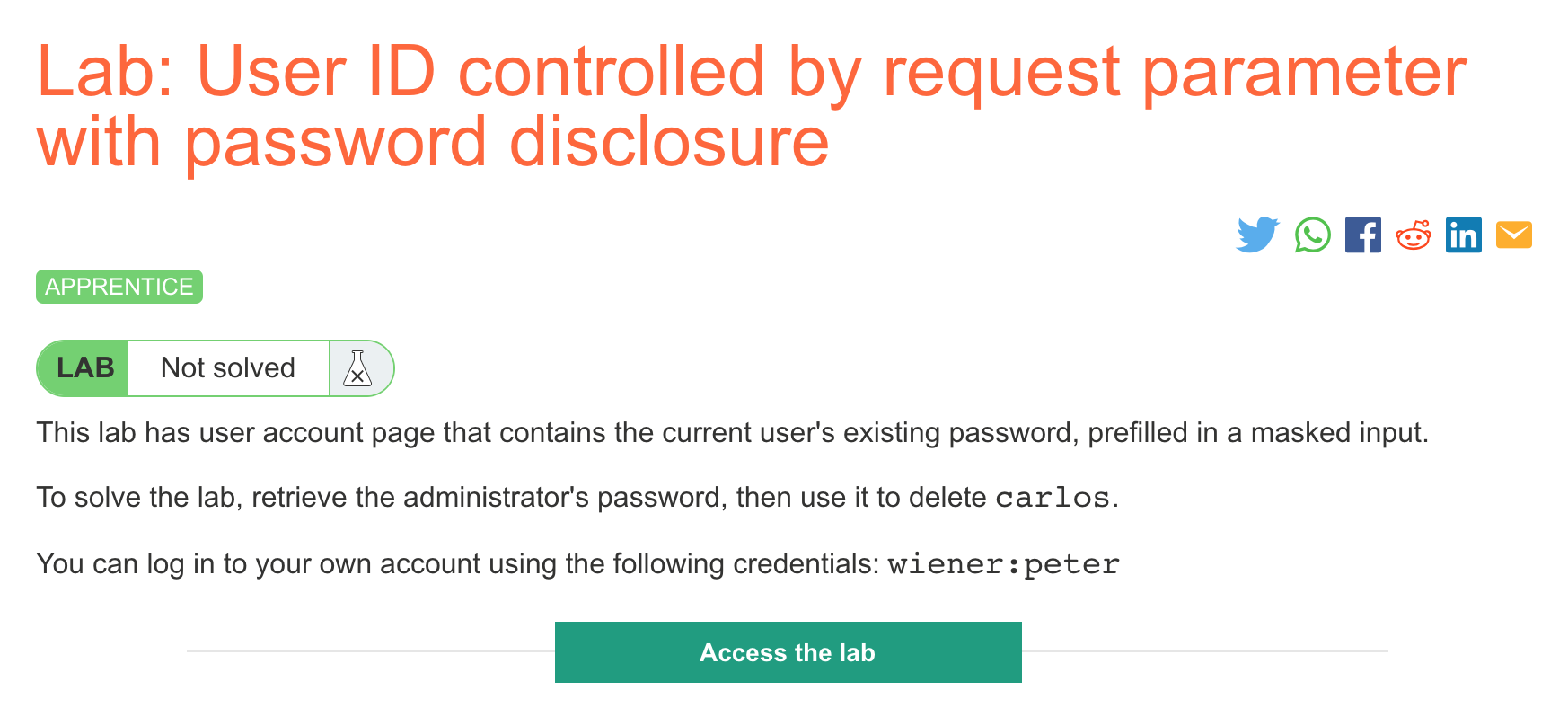
Click the “Access the Lab” button and you will be taken to a temporary website that is created for your account. This will be in format https://<random string here>.web-security-academy.net/.
We’re tasked with finding a vulnerability that lets us know the current user’s password, then using this “horizontal” (user-to-user) privilege escalation to achieve a “vertical” (user-to-admin) privilege escalation. And of course, we’ll finish with deleting Carlos’ account.
The website looks like this:
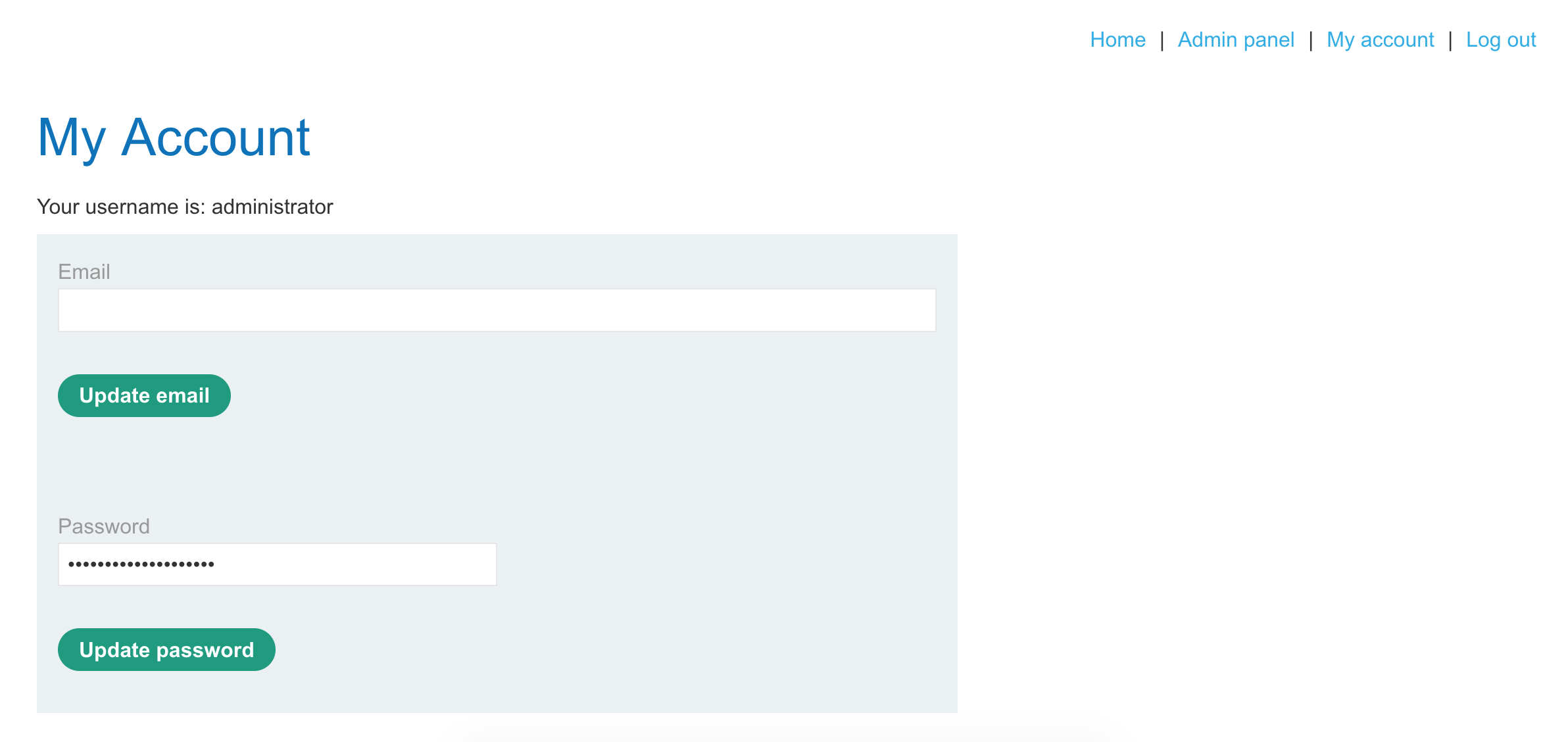
After we login with provided credentials wiener:peter, we see this account page, with a password form already filled in with 5 characters (suspiciously the same length as our own password, peter):
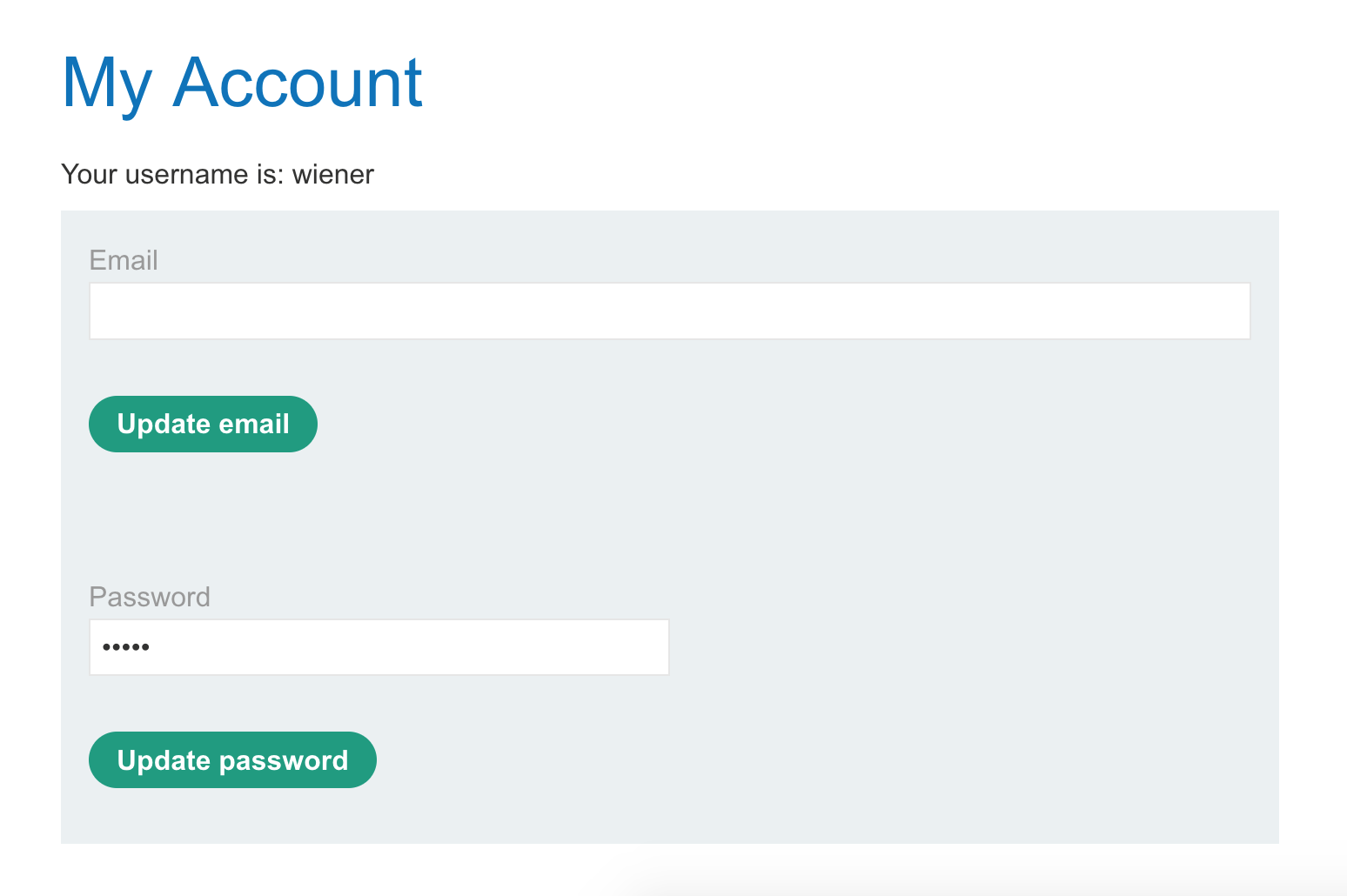
If we use Dev Tools to inspect the password field, it turns out that the value is peter. So the page is showing the user’s password back to them.
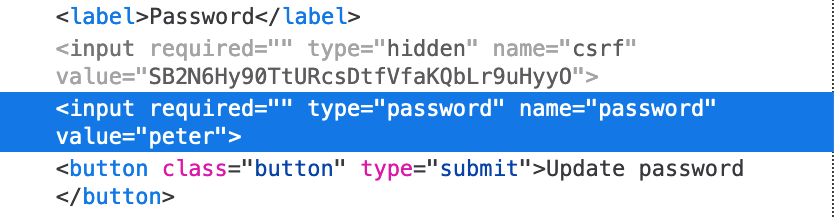
As in previous levels, if we click “My account”, it appends /my-account?id=wiener to the end of the URL. Let’s replace that with /my-account?id=administrator.
Well, that worked incredibly well.
Lab Solution
We’ve got access to the administrator’s information, although we don’t have any additional navigation options (such as to an admin portal). This is the “horizontal” privilege escalation discussed earlier.
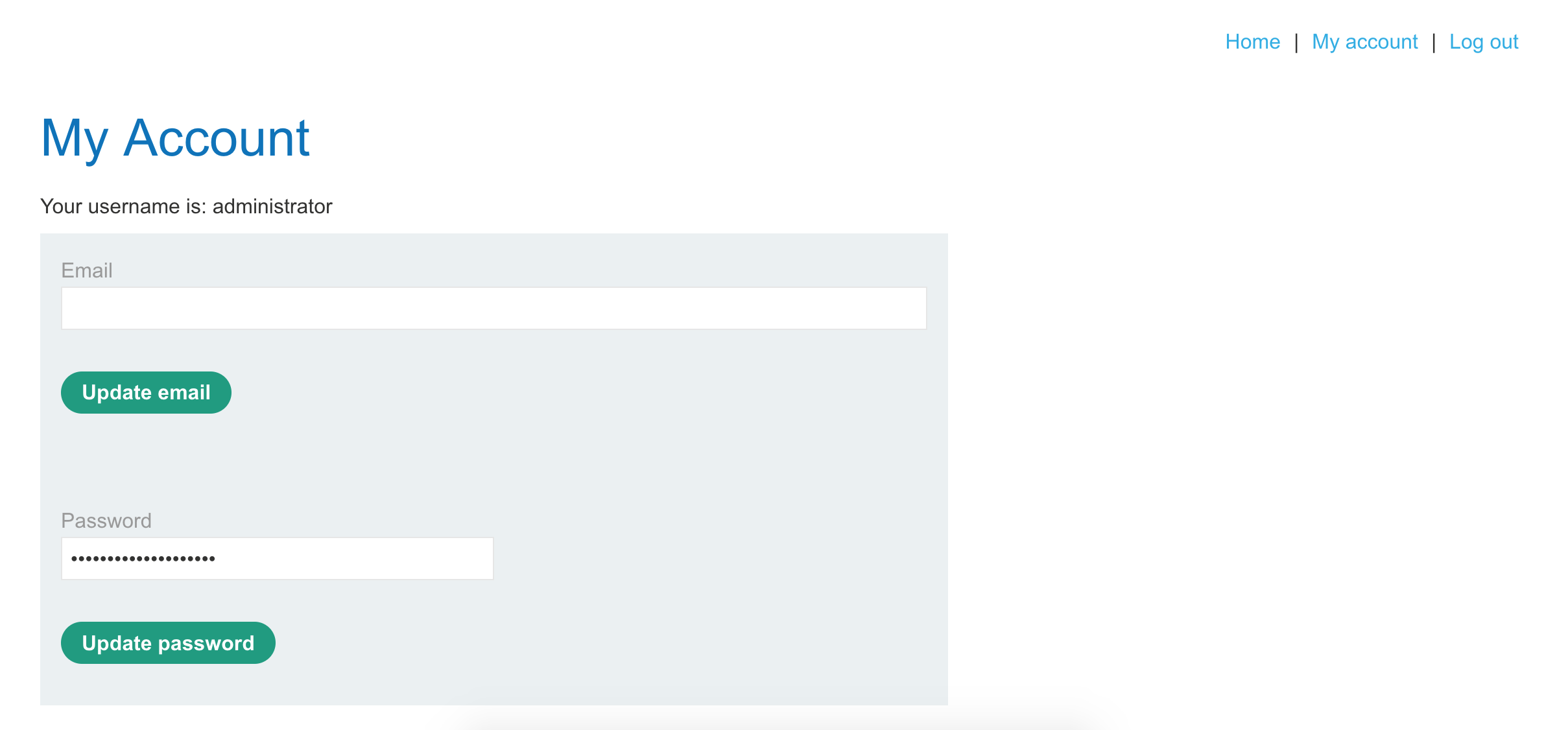
If we use Dev Tools again, we can see their password value: 5j36lh3213a5sqifmyre.
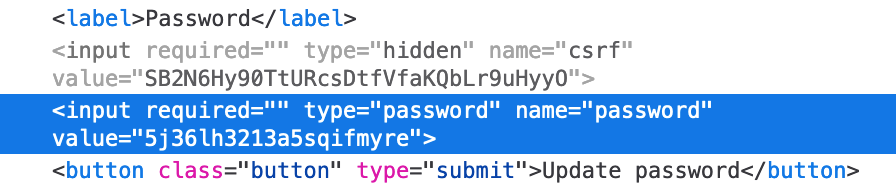
Log out, and then log back in with username administrator and the found password:
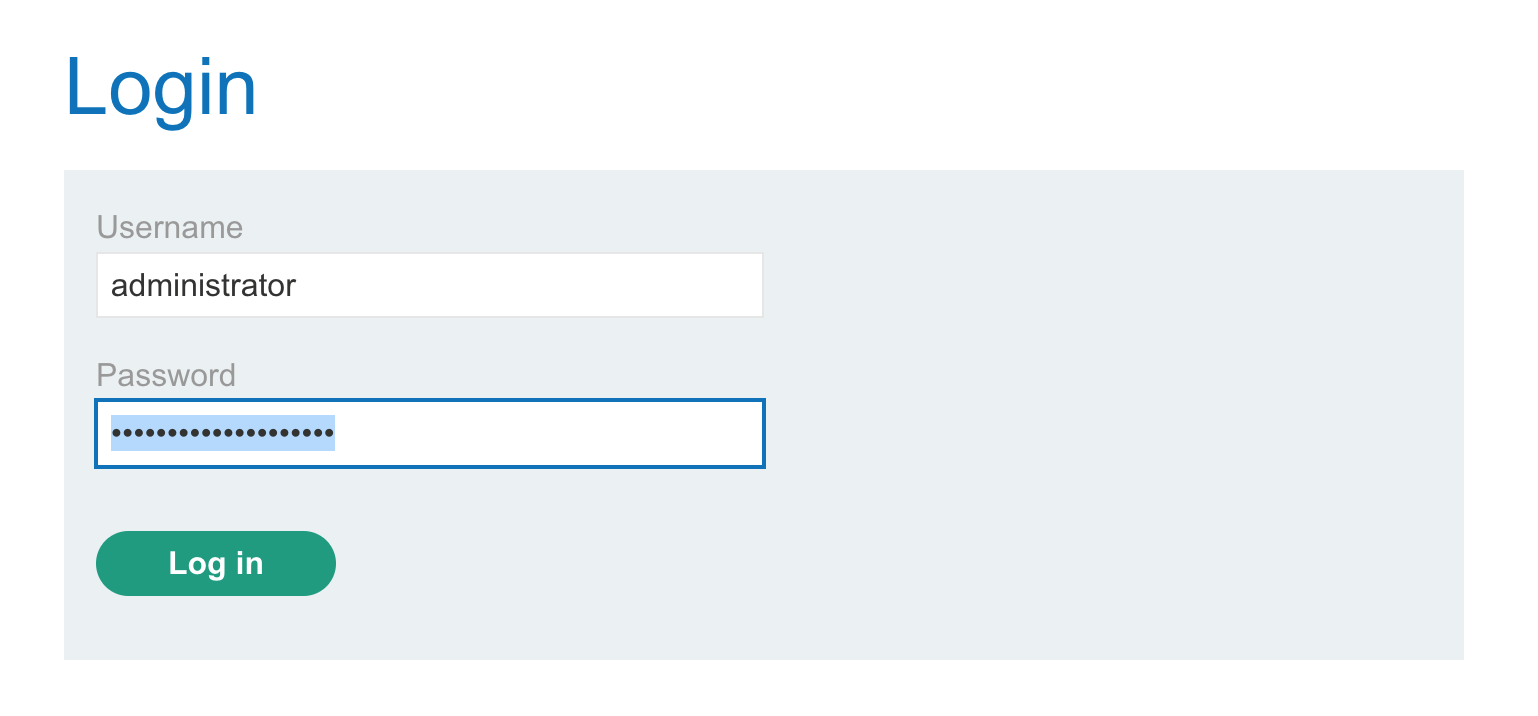
Now we’re truly logged in as the administrator, having achieved vertical privilege escalation. We know that because now the admin portal link is present within our account page.
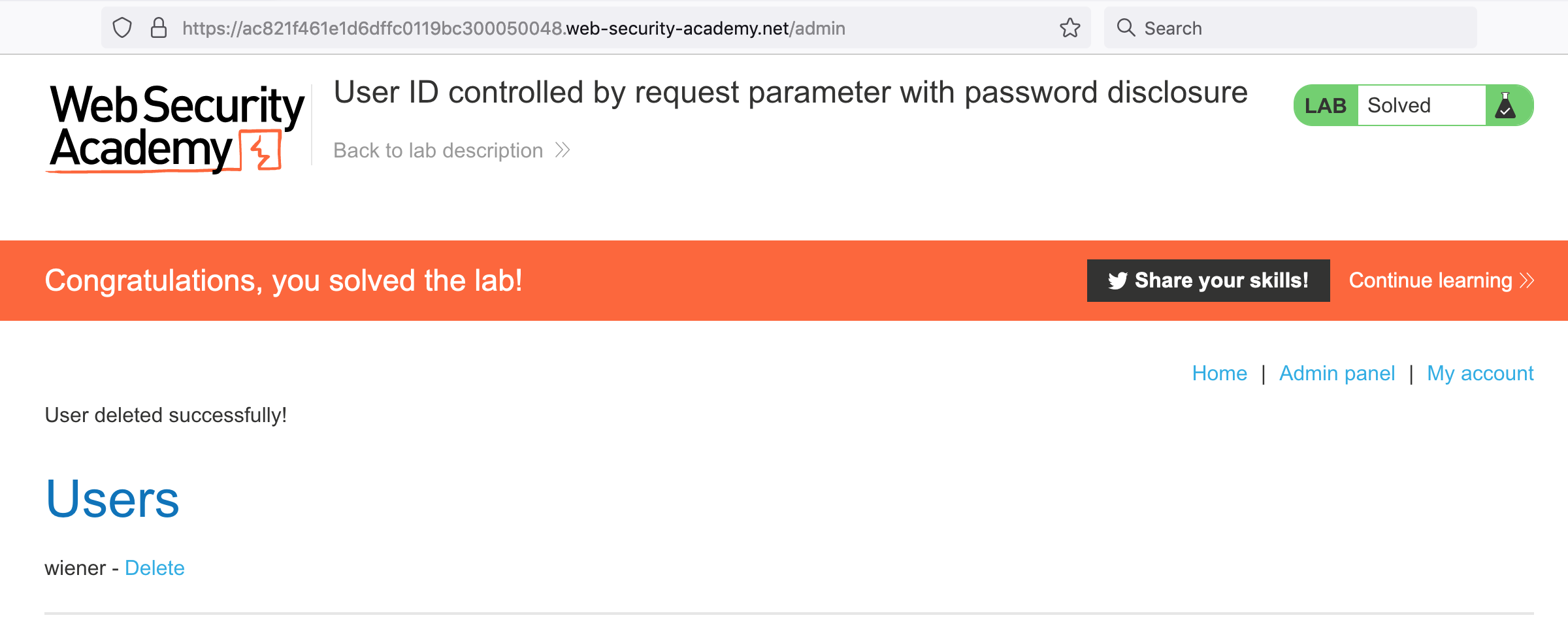
Click that to see the admin portal at /admin:
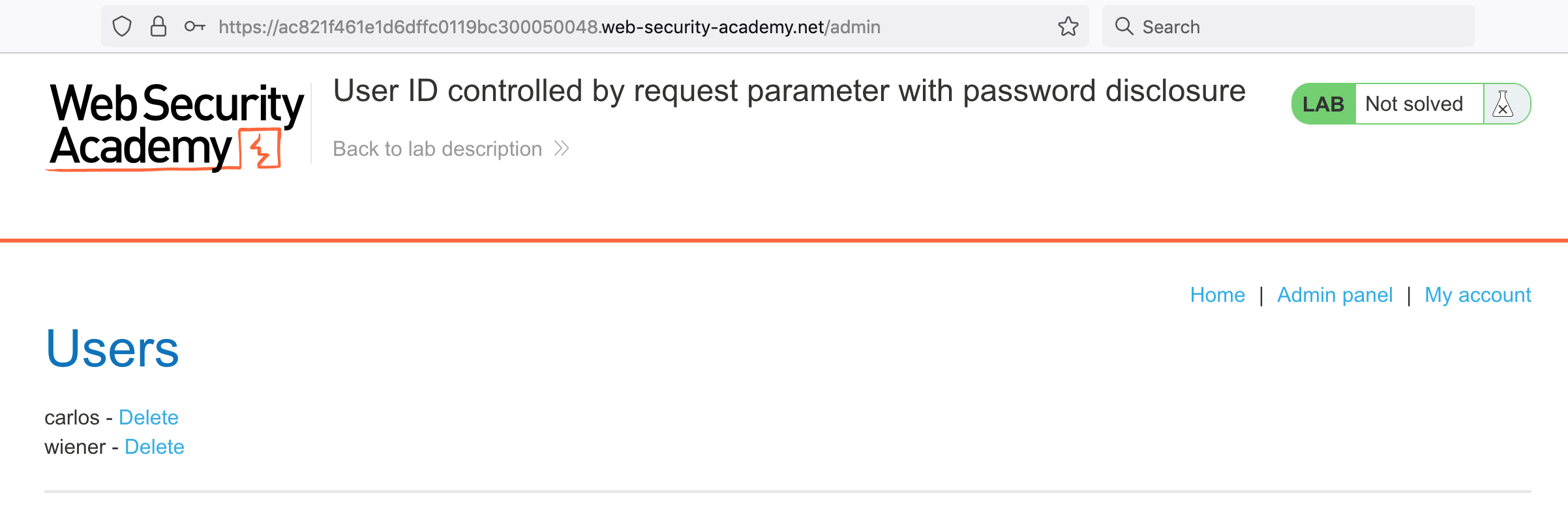
Delete Carlos, and you will have solved the lab!