PortSwigger's "User role controlled by request parameter" Walkthrough
This blog post is for the first Apprentice-level “user role” lab within Portswigger’s Access Control lab category.
Before we get started, you’ll need a Portswigger Academy account. Log in and then view the lab at https://portswigger.net/web-security/access-control/lab-user-role-controlled-by-request-parameter. This is accessible from the “all labs” view.
Challenge Information
Click the “Access the Lab” button and you will be taken to a temporary website that is created for your account. This will be in format https://<random string here>.web-security-academy.net/.
This challenge once again has us trying to get admin access and delete Carlos’ account. The trick here is a forgeable cookie.
The website is the usual shopping site:
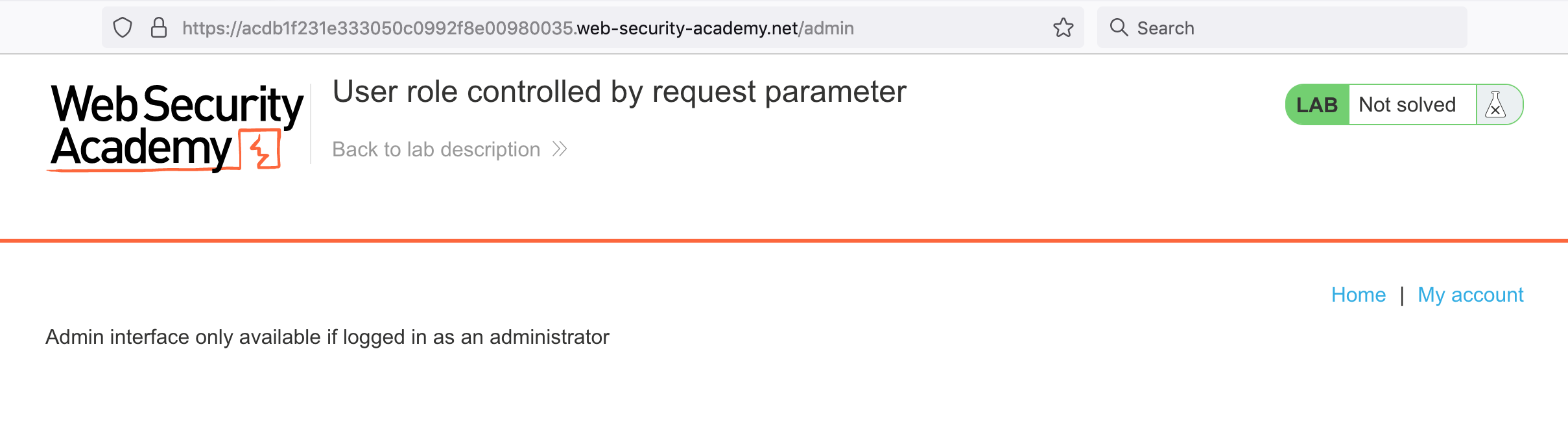
If we go to /admin, we get a message that we’re not allowed to access the controls as a non-admin user.
Let’s try logging in with the provided credentials of wiener:peter after clicking “My account”:
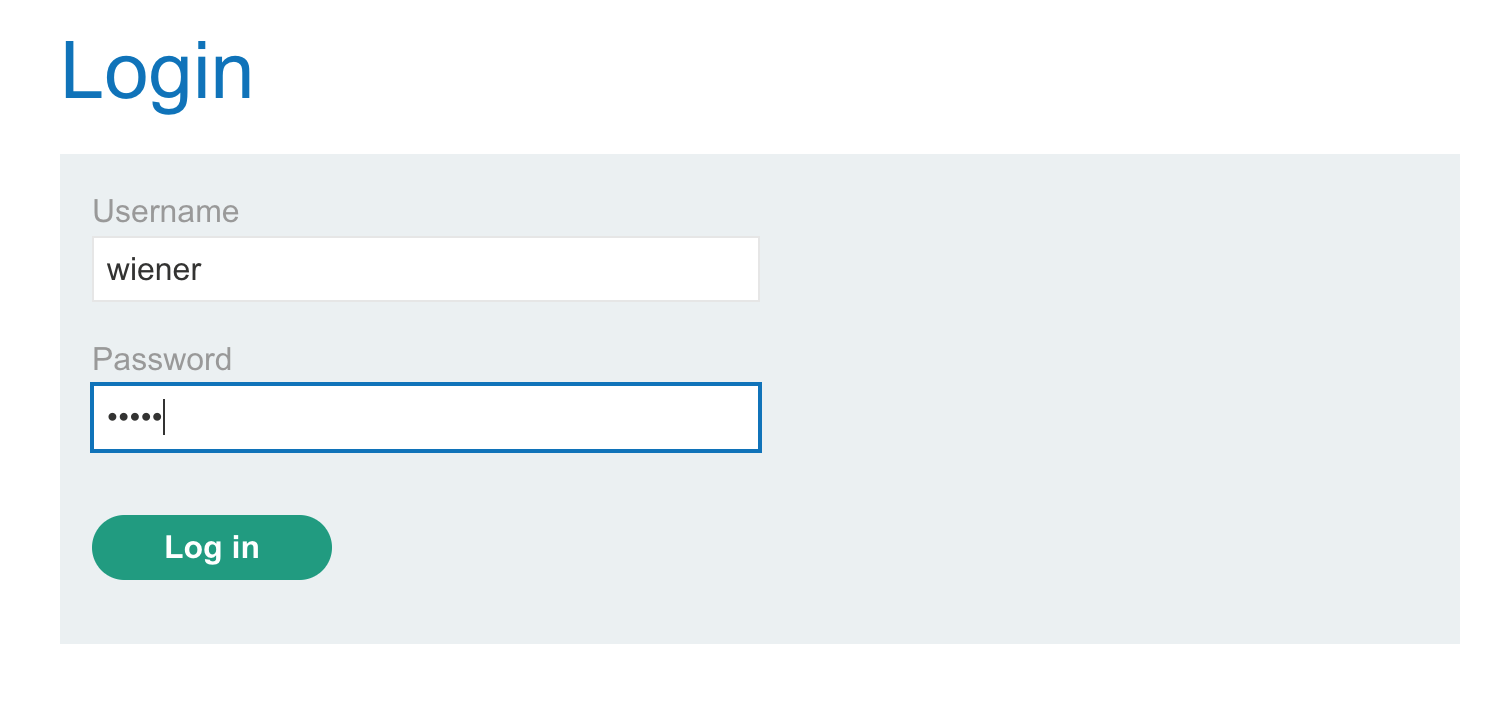
Now that we’re logged in, we should have some kind of session cookie.
Open up Dev Tools and go to Storage (Firefox) or Application (Chrome/others) to view cookies. We see that there’s a admin cookie with value set to false.
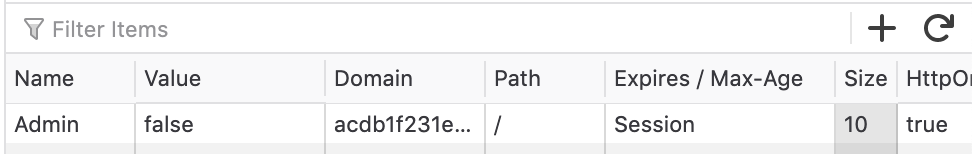
Lab Solution
To solve this lab, we simply have to change the value to true. You can do this within Dev Tools, by double-clicking and changing the value:
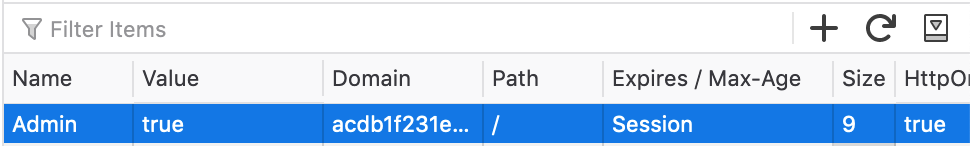
You can also alter it in Burp Suite by sending the request to the Repeater, finding the cookie value and setting it to true:
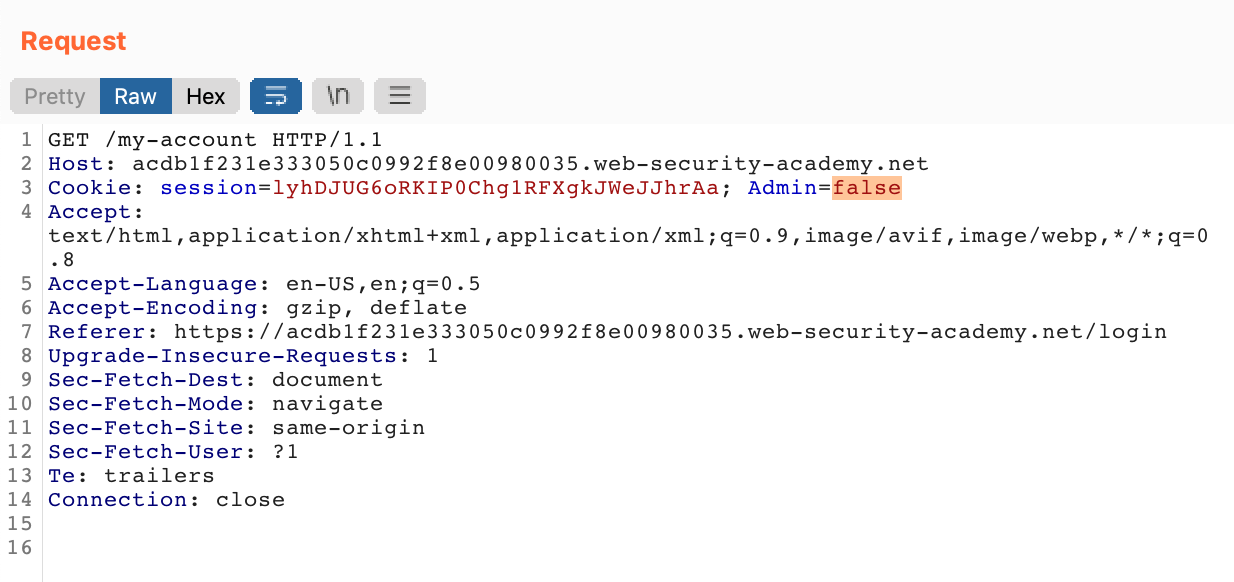
Either way, you can now access the admin panel:
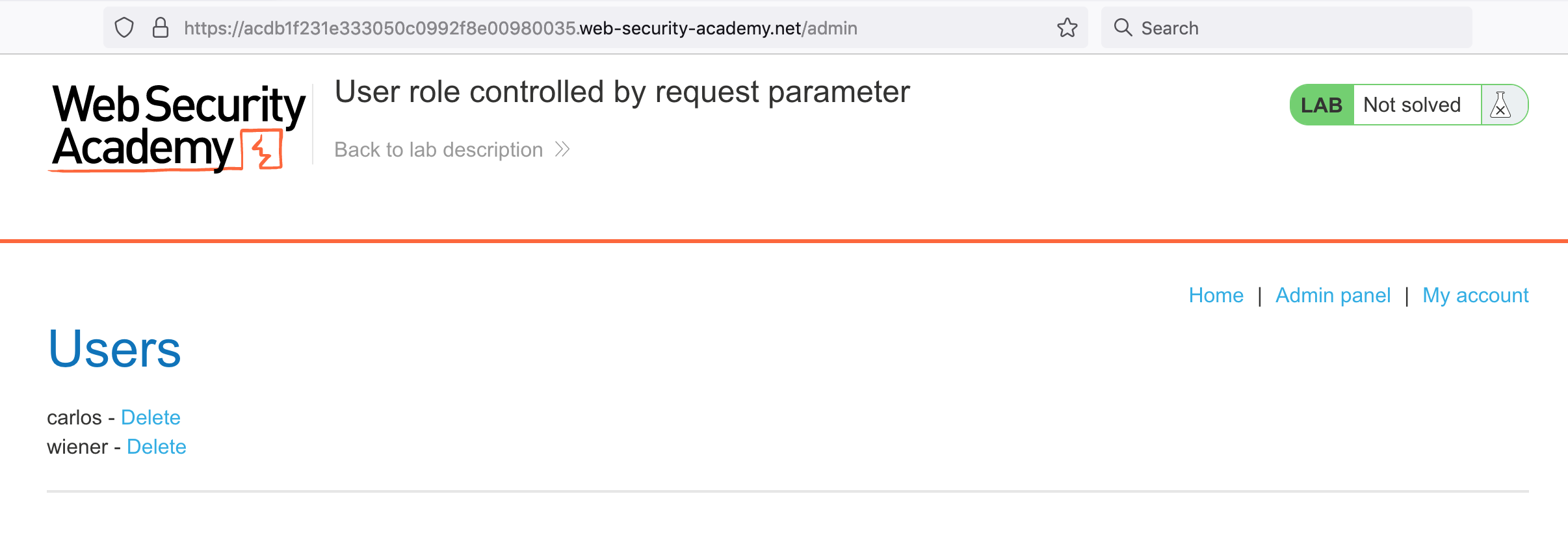
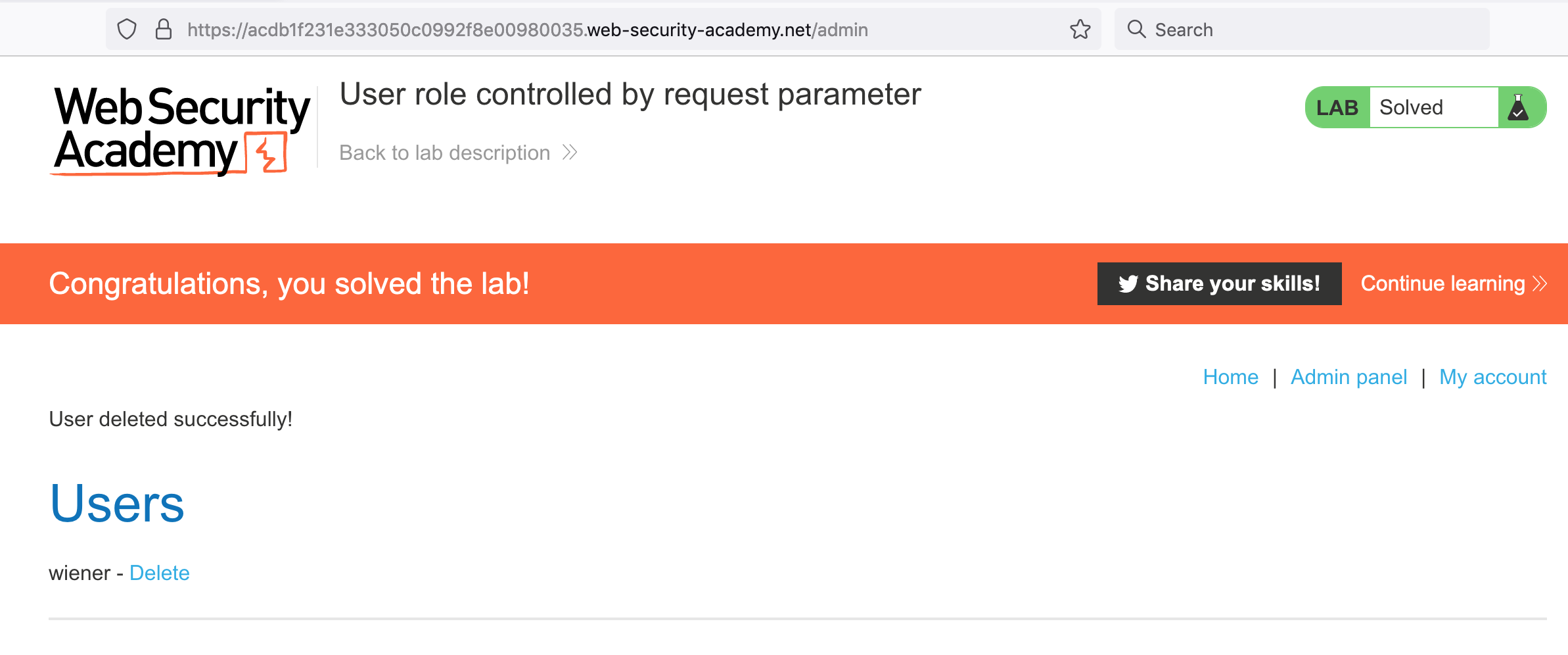
And can delete Carlos’ account to solve the challenge: