Quickly identify website technologies with Wappalyzer
In earlier posts about Dev Tools, Burp Suite, and other web posts, the idea of identifying a website’s underlying technologies was briefly discussed. In this post, we’ll talk about how to make the process even faster (with Wappalyzer), and why it matters in the first place.
Why This Matters (hint: enumeration)
If you’ve read about penetration testing (“pen testing” for short, and for less social awkwardness), you probably know that the process begins with enumeration. You may have also heard “enumerate!” as a hint from HTB forums or other groups.
Enumeration is incredibly helpful in pen testing, bug bounty, appsec, you name it.
It can also be useful in CTFs, but the structure of challenges usually gives you hints on how to solve the challenge in a way that “real world” websites might not. So if you are heavily involved in CTFs, it might be good to stretch your enumeration ‘muscles’ a bit using sites like Hack the Box, or on a bug bounty program (or other legal means of testing).
So what does enumeration get you?
- What languages are in use: certain languages have different properties (and vulnerabilities!) that other languages don’t have. While this is closely tied to some of the other points on the list, like frameworks, certain languages have common attack vectors that others don’t. Knowing that a website is written in PHP vs Python vs Javascript is very useful. And, if you’re able to get command injection, you’ll need to know what language to use.
- What databases are in use:
- Web server information: nginx? Apache? Tomcat? Are there proxies in use? Maybe you don’t need to find a vulnerability in their application if they have a vulnerable web server version running.
- What frameworks are in use: in the example above, they might be using Python. Great, are they using Flask, tornado, Django? If they’re using Javascript, is it vanilla JS? React? Angular? Are they using frameworks like Handlebars?
- CMS information: are they using WordPress? Drupal? Something else?
- Version numbers for all of the above: software is updated and new versions come out. Knowing that someone is using Tomcat is not necessarily useful information in itself (although it can help you narrow down web scanning efforts). Knowing a technology and the version number will be very useful for identifying vulnerabilities.
All of this information helps you narrow down your options for attack, search for relevant CVEs and proof-of-concepts, and go about your efforts in an organized way.
There are many ways to get this information but an easy way to view all of this in one place is Wappalzyer.
Install Wappalyzer
Wappalyzer’s website talks a lot about how their product can be used for lead generation and other marketing type things.
Instead, you can jump straight to the browser plugin download pages:
From there, installation should be pretty straightforward. Hit the “add” or “install” button and then it should appear in your browser toolbar as an icon (a stack of purple squares turned sideways).
If you don’t want to install it, you can always use their website to individually profile a given website.
How to Make Use of Wappalyzer
Once you’ve got Wappalyzer installed, you can click it and view the detected frameworks and languages. Sometimes this is really not interesting, such as what is reported on Google.com:

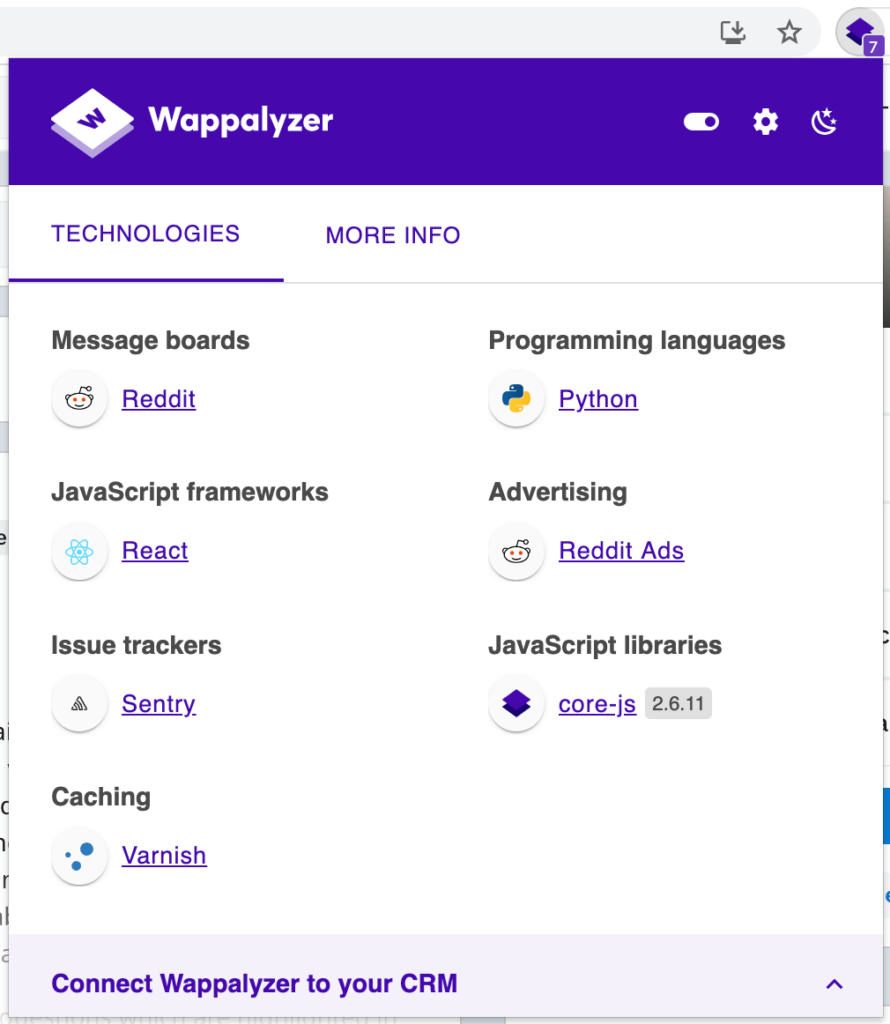
But other sites have more information:
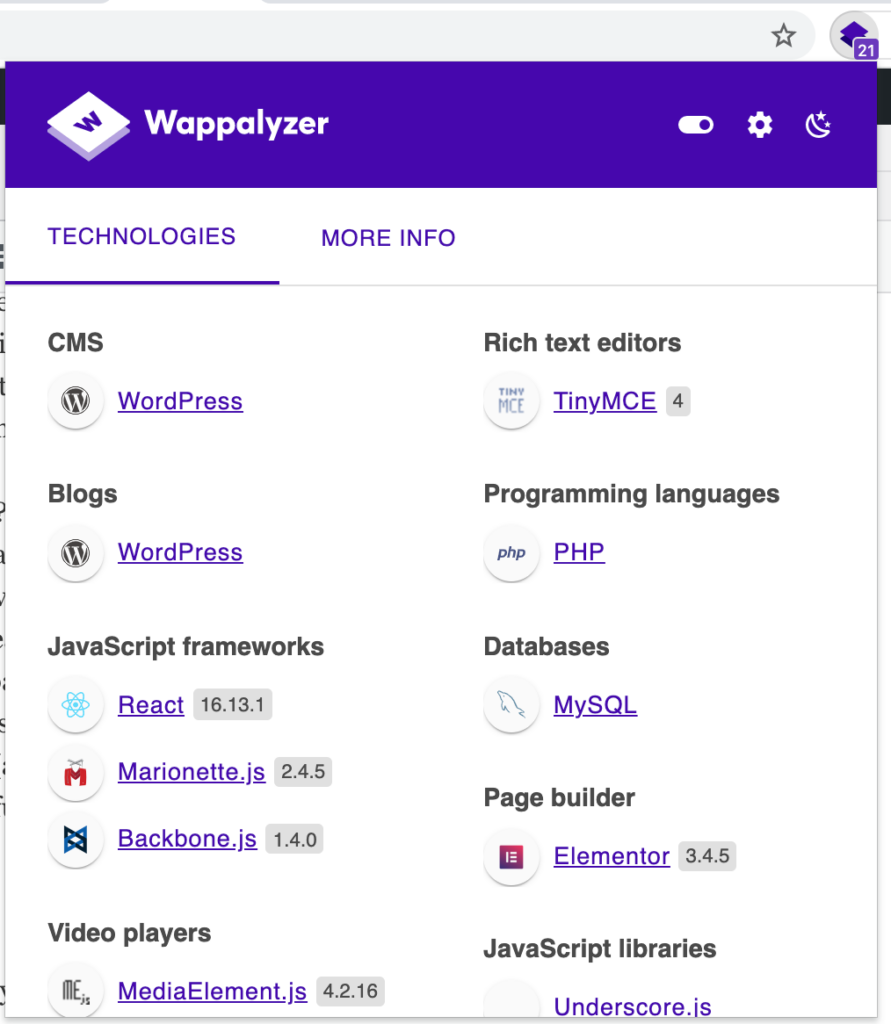
It might also be useful to try this out: just browsing your usual websites, and viewing what Wappalyzer detects.
If you see something you’re unfamiliar with, spend 5 minutes to read up on it.
Hacking is a skillset that builds on knowledge across many different areas, and absorbing this a bit at a time can help your future self out.
To try this out and then find an exploit to use (again, legally), I recommend Hack the Box’s challenges. Sure, nmap is often going to be just as, or more useful, but it’s a handy tool to have.